BlackCat ransomware continues to make a fuss globally for the second year now, targeting various sectors. Most of the time, it goes to healthcare, government, education, manufacturing, and hospitality. The group constantly improves operations, automating data exfiltration and releasing new ransomware versions with upgraded capabilities.
What is BlackCat Ransomware?
The cybercriminals use ALPHV (BlackCat), a sophisticated ransomware-type program written in the Rust programming language, for their operations. It is distributed as Ransomware-as-a-Service (RaaS) model, encrypts data by locking files, and actively demands payment for decryption. In most cases, the malicious actors responsible for this type of malware rename the encrypted files by appending them with specific extensions. Since the software is distributed as a service, the name of the blocked file extensions depends on the current attackers.
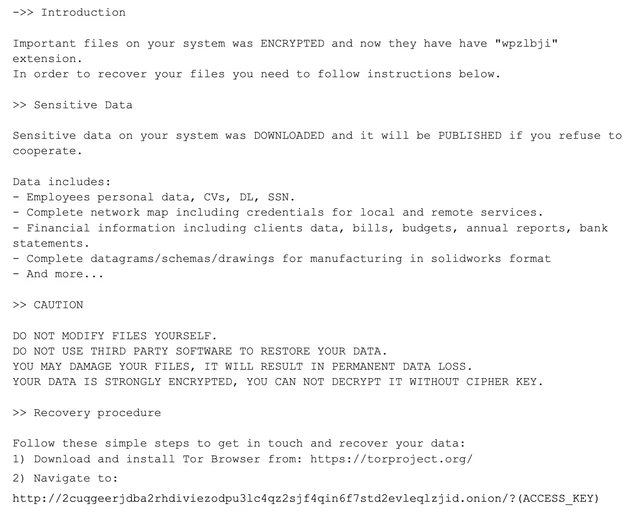
Though, these details are quite trivial for any successful modern ransomware group. More interesting details about BlackCat include their unique approach towards spreading methods and rough behavior when it comes to data publication. The latter, actually, is done on a clear web site, instead of a more regular Darknet page. Moreover, these hackers were among the first who used so-called triple extortion – asking additional money to keep the attack fact in secret.
BlackCat’s level up
BlackCat gained notoriety almost immediately after its launch in November 2021. It was regularly at the top of the most active ransomware groups and was associated with the now-defunct BlackMatter. /DarkSide ransomware. In addition, in 2022 BlackCat switched to the Rust programming language. This gave the customization provided by this language and the ability to bypass malware detection and analysis. However, even after a year and a half, there is no hint that BlackCat’s career is nearing its end.
Over the last six months, BlackCat has been constantly improving its tools. They have abused the functionality of Group Policy Objects to deploy tools and interfere with security measures. For example, attackers may try to increase the speed of their operations by changing the default Group Policy update time, thereby shortening the time between the changes taking effect and the defenders being able to react.
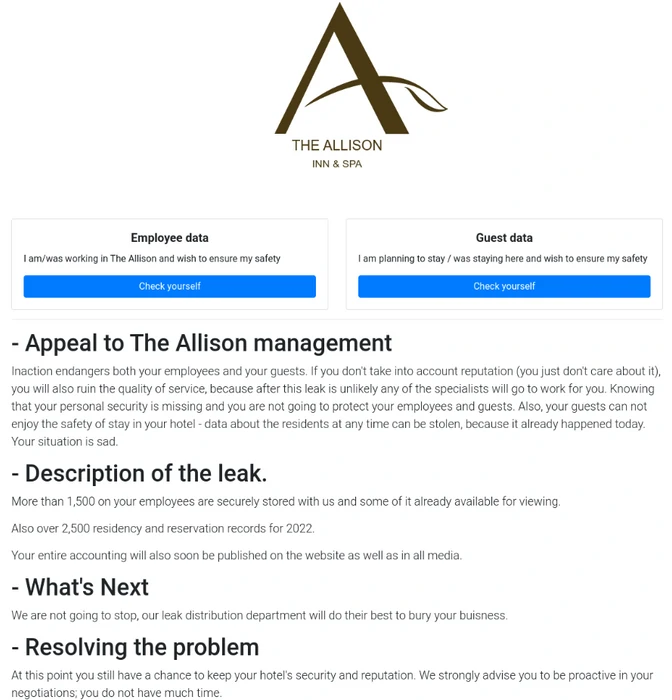
In addition, BlackCat ransomware operators are deploying a double extortion scheme, using tools for both data encryption and theft. One tool, ExMatter, was used to exfiltrate multiple terabytes of data from victims to the attackers’ infrastructure. One BlackCat affiliate exclusively uses this tool, tracked by Microsoft as DEV-0504. The attackers frequently post stolen data publicly on their official leak site. They are doing that for one reason – to pressure their extortion victims.
New version of BlackCat
A new version of BlackCat, called Sphynx, was also observed by IBM X-Force. It was announced in February 2023 and has updated capabilities that make it harder to detect. Sphynx differs significantly from previous variants. For example, reworking the command line arguments and using raw structures instead of JSON formatting for configuration data. This makes it harder to detect and analyze the ransomware. The BlackCat group has stated that it was a global update and it was done to optimize detection by AV/EDR. In short, the BlackCat Sphynx Loader is an obfuscated loader that decrypts strings and payloads upon execution. It conducts network discovery activities and creates a ransom note in encrypted files. The BlackCat ransomware sample may also function as a toolkit based on tools from Impacket.
How does it work?
Initial access and privilege escalation
Researchers tend to believe that attackers used valid credentials obtained through Raccoon and Vidar stealers in the earliest stages. After successfully penetrating a network, attackers use PowerShell and the command line to gather information. In particular, they are interested in information about user accounts, domain computers, and permissions. As a result, they use the PowerShell code associated with “PowerSploit” to obtain domain administrator credentials.
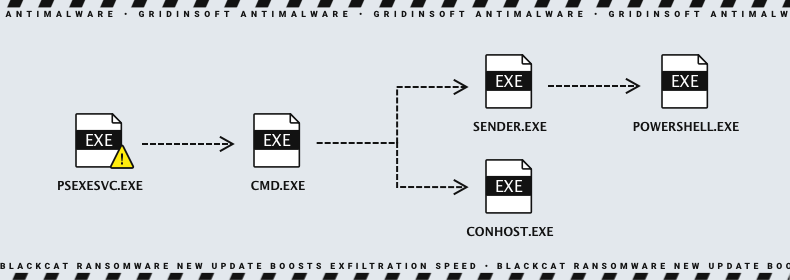
Defense Evasion and Lateral Movement
Next, the attackers use Remote Desktop Protocol (RDP) to move around the network. Using credentials for accounts with administrative privileges, they authenticate to domain controllers. Eventually, they modify the default domain group policy object (GPO). These actions allow them to disable security controls, Microsoft Defender, system monitoring, security, and notifications. In addition, attackers edit the default domain group policy settings.
Exfiltration and self-destruction
As mentioned above – BlackCat extracts data using ExMatter before launching the ransomware. This malware installs itself as a service in the system registry section in the following key. Then, a secure file transfer protocol and WebDAV send the stolen data to the attacker’s infrastructure. After exfiltrating the data, Exmatter launches a specific process to remove all its traces.
BlackCat vs. Linux
In addition to attacking Windows systems, BlackCat affiliates can attack unix systems. In this case, the payload is deployed on ESXIi hosts with virtual machines using WinSCP. The attackers then access the hosts using PuTTY to run the ransomware. Releasing malware versions adjusted to attack Linux systems appears to be a new trend among cybercriminals – and it should not be ignored.
How to Protect Against BlackCat Ransomware Attacks
- Educating employees. Educating employees is crucial to safeguard against ransomware like BlackCat. Training them on identifying phishing emails, avoiding suspicious links and attachments, keeping software updated, and reporting any suspicious activity to IT or security personnel can reduce the risk of an attack. Regular security awareness training can inform employees about the latest threats and best practices.
- Encrypting sensitive data. Encrypting sensitive data is an effective way to protect against BlackCat ransomware and other malware. This involves converting the data into a code requiring a decryption key. Financial records, personal information, and important files should always be encrypted. Access controls should also be implemented to restrict who can view or modify the data. By encrypting sensitive data and implementing access controls, businesses can significantly reduce the risk of attack and potential impact.
- Backup data. Backing up and storing your data offline is the best way to keep and protect your files from any ransomware and other malware. We recommend storing a copy of essential files in a separate location. For example, you can use an external or cloud storage. If infected, you can erase files and restore data from the backup. Keep backups secure by storing them in a location physically separate from your computer or using a reputable cloud storage service with strong security and encryption.
These were the main ways to prevent negative consequences. But in addition, it is essential to use multi-factor authentication, use strong passwords, Install updates, Monitor network traffic, and Monitor file and folder activity.