Wise Remote Stealer is a potent and malicious software that operates as an infostealer, Remote Access Trojan (RAT), DDoS bot, and ransomware. It has gained notoriety within the cybersecurity community due to its extensive range of capabilities and the threat it poses to individuals and organizations.
Unveiling the Wise Remote Stealer
Revelations from cybersecurity experts have shed light on a concerning development in the underbelly of the internet—a burgeoning menace known as “Wise Remote“. This pernicious malware, operating as a Malware-as-a-Service (MaaS), has emerged as a highly adaptable and insidious tool. Its capabilities encompass remote access, DDoS botnet recruitment, data theft, and even extortion, raising the alarm for organizations and individuals alike.
The Stealthy Proliferation of Wise Remote Stealer
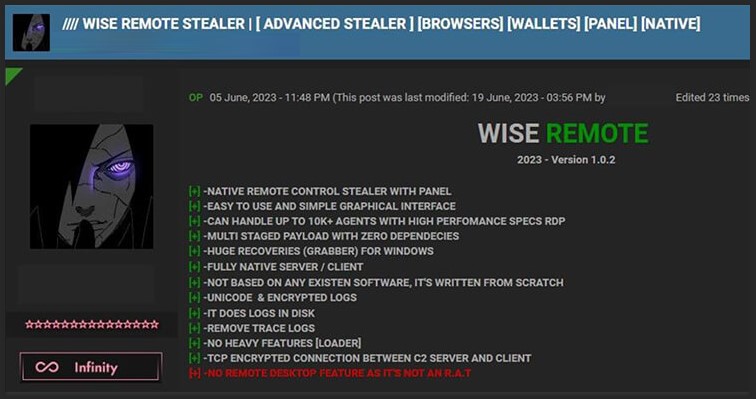
Since its initial appearance in early June, Wise Remote Stealer has been making waves across hacker forums such as HF and cracked-io. Its shadowy creators tirelessly refine and enhance their creation, showcasing its malevolence on platforms like Discord and Telegram. Disturbingly, these demonstrations have ensnared and impacted the lives of over a thousand unsuspecting victims, cementing its reputation as a significant threat.
Engineered using a combination of programming languages, including Go, C++, C#, and Python, Wise Remote primarily targets Windows systems—versions 8/10, and 11—in its crosshairs. Its developers exhibit an astute ability to elude conventional antivirus measures, employing various evasion techniques. To further cloak their operations, all communication with the command-and-control (C2) server, stationed in the secure confines of Switzerland, remains encrypted, ensuring anonymity.
The Tactical Ingenuity of Wise Remote
Wise Remote operates with calculated precision, showcasing a level of sophistication that sets it apart from other malicious tools. Through cloud-based module imports and strategic data storage within the victim’s disk, it carefully conceals its activities. Once the sensitive information has been exfiltrated, the malware meticulously erases all traces, leaving behind no digital footprints.
Subscribers to this nefarious service gain access to a comprehensive builder, allowing for customization and fine-tuning of the malware’s appearance and behavior. Remarkably, the resulting payloads rarely exceed 100 kilobytes, facilitating rapid dissemination and maximizing its reach.
The existing capabilities of Wise Remote Stealer are indeed alarming:
- Systematic collection of extensive system information, providing cybercriminals with a wealth of valuable data.
- Creation of a potent reverse shell, granting complete remote access and control over the compromised system.
- Facilitation of additional malicious file downloads and executions, enabling expansion of the attack surface.
- Extraction of critical data from web browsers, encompassing saved passwords, cookies, banking credentials, bookmarks, browsing history, and installed extensions, resulting in a treasure trove of personal information.
- Theft of funds from unsuspecting victims’ cryptocurrency wallets, inflicting significant financial damage.
- Seamless covert operation, opening and interacting with websites undetected, masquerading as legitimate user activity.
- Stealthy capture of screenshots, potentially compromising sensitive and confidential information.
- Utilization of the AppData folder as a discreet repository for surreptitiously uploaded files.
- Empowerment of attackers to customize and tailor malicious agents and modules to suit specific targets and preferred attack vectors.
- Camouflaging its tracks by manipulating system logs, erasing any trace of malicious activities, evading detection.
The Command Hub of Wise Remote
Serving as the central command hub, Wise Remote boasts a potent control panel that bestows unprecedented oversight and control over a vast network of up to 10,000 infected machines. With a single command, the operator can unleash devastating DDoS attacks or orchestrate a range of malicious activities, amplifying the disruptive potential of this malware.
As the cybersecurity community races to counter this emerging threat, the significance of Wise Remote becomes increasingly evident. Its adaptability, sophistication, and capacity for stealth underline the need for robust security measures and unwavering vigilance in today’s rapidly evolving digital landscape.





