Lumen Black Lotus Labs has discovered a new Remote Access Trojan (RAT) called ZuoRAT, attacking remote workers’ routers in North America and Europe since 2020. The malware appeared in the first months of the COVID-19 pandemic but remained unnoticed for more than two years.
The researchers write that the complexity of this targeted campaign, as well as the tactics and methods of “work” of the attackers, indicate that some government hackers are behind ZuoRAT.
Recall that we also wrote that Trojan Qbot Took Advantage of the Famous Follina Vulnerability, and also that Trojan Source attack is dangerous for compilers of most programming languages.
As noted above, the start of this campaign coincided with the widespread shift to remote work following the beginning of the COVID-19 pandemic, which has dramatically increased the number of routers (including Asus, Cisco, DrayTek and NETGEAR devices) used by employees to access corporate networks remotely.
Hackers gained initial access to routers by looking for known unpatched vulnerabilities, which were then used to download a remote access tool. Having gained access to the network, the attackers delivered to the victim the shellcode loader for the next stage of the attack, which had already been used to provide Cobalt Strike and custom backdoors, including CBeacon and GoBeacon, which were capable of executing arbitrary commands.
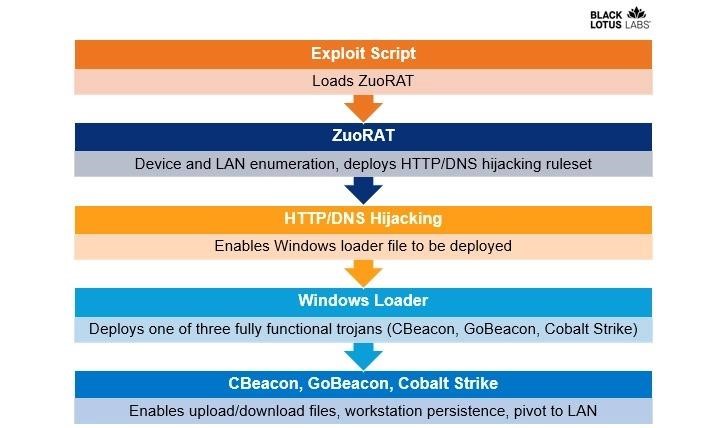
The researchers say that the malware of this hacking group is capable of conducting in-depth surveys of the target network, collecting traffic, intercepting network communications, and generally describe the malware as a heavily modified version of the well-known Mirai malware.
Also, the malware has an active function of collecting TCP connections through ports 21 and 8443, which are associated with FTP and web browsing, potentially allowing you to monitor the victim’s Internet activity behind a compromised router.
Other ZuoRAT features include features for monitoring DNS and HTTPS traffic. This is done to intercept requests and redirect victims to malicious domains using predefined rules that are generated and stored in temporary directories.
ZuoRAT also allowed hackers to move further along the victim’s network to compromise other devices and deploy additional payloads (such as Cobalt Strike beacons). During such attacks, the already mentioned CBeacon and GoBeacon Trojans were used.
At the same time, hackers took various steps to hide their actions. For example, behind the attacks was a complex, multi-layered C&C infrastructure that included using a virtual private server to propagate the initial RAT exploit, as well as the use of the compromised routers themselves as C&C proxies.
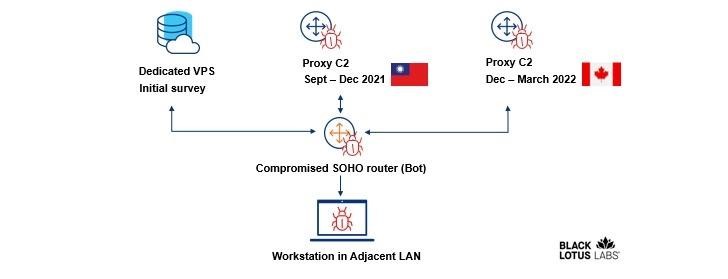
The researchers note that, like most router malware, ZuoRAT does not survive reboots. A simple restart of the infected device will remove the original ZuoRAT exploit stored in the temporary directory. However, to fully restore infected devices, experts advise performing a factory reset. It is also emphasized that devices connected to a hacked router may already be infected with other malware, and it will be impossible to cure them just as quickly.





For this Zuorat malware, is there a definitive list of brands and models of routers affected.