The researchers warned that the Qbot malware is already exploiting an unpatched zero-day vulnerability in Windows MSDT called Follina.
Let me remind you that the discovery of Follina became known at the end of May, although the first researchers discovered the bug back in April 2022, but then Microsoft refused to acknowledge the problem.
The vulnerability has been tracked under the identifier CVE-2022-30190 and is known to be exploitable to execute arbitrary code through the normal opening of a Word document or preview in File Explorer, resorting to executing malicious PowerShell commands through the Microsoft Diagnostic Tool (MSDT).
The bug affects all versions of Windows that receive security updates, that is, Windows 7 and later, as well as Server 2008 and later.
Let me remind you that we wrote that Microsoft Is in No Hurry to Fix the Follina Vulnerability, Which Has Become a Real Disaster.
Previously, experts have already warned that the vulnerability is exploited by Chinese hackers, and it is also being used to attack European governments and municipal authorities in the United States. Now, Proofpoint experts write that even the Qbot malware has begun using malicious Microsoft Office documents (.docx) to abuse CVE-2022-30190 and infect recipients of such phishing emails.
To attack, hackers use emails with HTML attachments that download ZIP archives containing images in IMG format. Inside such an image, the victim will find a DLL file, Word, and a shortcut.
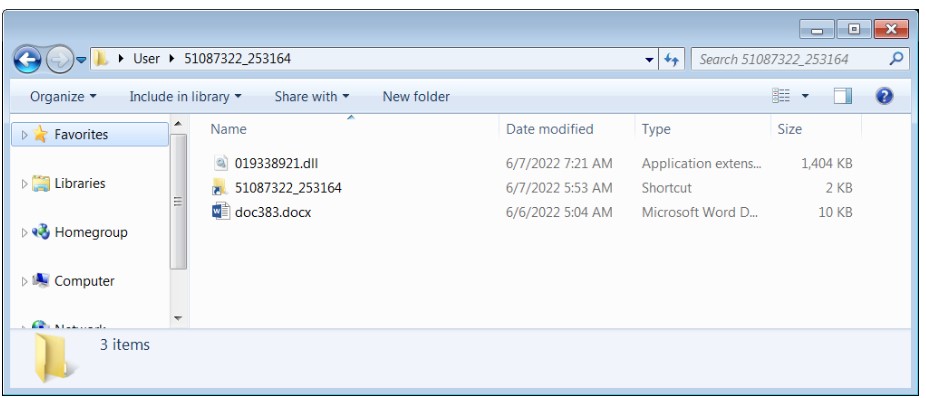
Whereas the shortcut file directly downloads the Qbot DLL already present in the image, the empty .docx document contacts an external server to download an HTML file that exploits the Follina vulnerability to run PowerShell code, which in turn downloads and executes another Qbot DLL payload.
Indicators of Compromise related to this campaign can be found here.
The researchers believe that the use of two different infection methods indicates that hackers are conducting an A/B testing campaign to evaluate which tactics will give the best results.




