Hackers are actively exploiting the critical 0-day Follina vulnerability, which Microsoft is in no hurry to fix.
Researchers warn that European governments and municipalities in the US have been targeted by a phishing campaign using malicious RTF documents.
Let me remind you that the discovery of Follina became known at the end of May, although the first researchers discovered the bug back in April 2022, but then Microsoft refused to acknowledge the problem.
The vulnerability has been tracked under the identifier CVE-2022-30190 and is known to be exploitable to execute arbitrary code through the normal opening of a Word document or preview in File Explorer, resorting to executing malicious PowerShell commands through the Microsoft Diagnostic Tool (MSDT).
The bug affects all versions of Windows that receive security updates, i.e. Windows 7 and later, as well as Server 2008 and later.
Worse, it is noted that the vulnerability is in many ways similar to the PrintNightmare problem, which Microsoft could not fix for quite some time. The fact is that Follina also pulled the discovery of other bugs, the consequences of exploiting which can be no less serious.
We have already written that Chinese hackers are actively using the fresh 0-day, and experts warned that soon there will be more such attacks. Unfortunately, the predictions of the experts turned out to be correct: now Proofpoint analysts report that they have discovered a phishing campaign aimed at government agencies in Europe and municipal authorities in the United States, which in total affected at least 10 of the company’s customers. According to experts, government hackers are behind these attacks.
To deceive potential victims and force them to open a decoy document, the attackers used the theme of a pay increase. Opening the document resulted in the deployment of a Powershell script that checked to see if the system was a virtual machine and was then used to steal information from multiple browsers, email clients, and file services, as well as collect system information, after transferring the data to a server controlled by hackers.
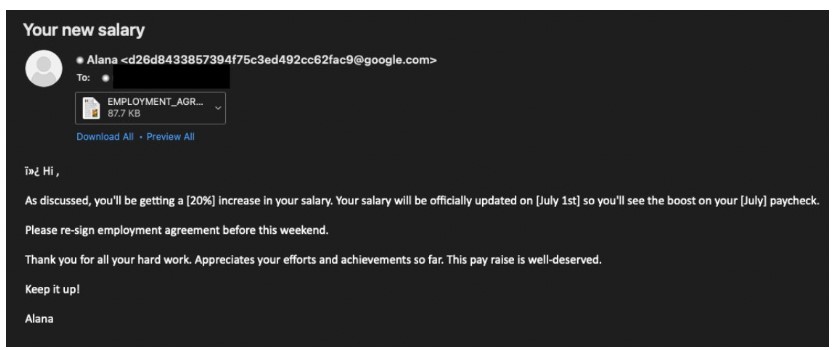
According to Bleeping Computer, the payload collected a lot of data from a wide variety of applications, including:
- passwords from browsers: Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, Yandex, Vivaldi, CentBrowser, Comodo, CheDot, Orbitum, Chromium, Slimjet, Xvast, Kinza, Iridium, CocCoc and AVAST Browser;
- data from other applications: Mozilla Thunderbird, Netsarang session files, Windows Live Mail contacts, Filezilla passwords, ToDesk configuration file, WeChat, Oray SunLogin RemoteClient, MailMaster, ServU, Putty, FTP123, WinSCP, RAdmin, Microsoft Office, Navicat;
- system information: computer information, list of usernames, Windows domain information.
Most of the attacks are reported to have been in the United States, as well as Brazil, Mexico and Russia.
Since there is still no patch for Follina, administrators and users can block attacks on CVE-2022-30190 by disabling the MSDT protocol, which attackers use to launch debuggers and execute code on vulnerable systems. It is also officially recommended to disable file previews in Windows Explorer, because the attack is possible in this way as well.

In the absence of an official patch, an unofficial one has already appeared, from 0patch. Let me remind you that 0patch is a platform designed just for such situations, that is, fixing 0-day and other unpatched vulnerabilities, to support products that are no longer supported by manufacturers, custom software, and so on.
Unofficial patches are provided for Windows 11 v21H2, Windows 10 (1803 to 21H2), Windows 7 and Windows Server 2008 R2. Moreover, instead of disabling MSDT recommended by Microsoft, 0patch specialists added additional cleaning of the path provided by the user, which also helps to avoid exploiting the bug.
Meanwhile, information security experts are already beginning to criticize Microsoft for its sluggishness and lack of fixes.




