Symantec specialists detected Raindrop malware, which was used during the attack on SolarWinds along with other malware.
According to the researchers, Raindrop was used by cybercriminals in the last stages of the attack and was deployed only on the networks of a few selected targets (only four malware samples were found).
Let me remind you that SolarWinds, which develops software for enterprises to help manage their networks, systems and infrastructure, was hacked in mid-2019, and this attack on the supply chain is attributed to an allegedly Russian-speaking hack group, which information security experts track under the names StellarParticle (CrowdStrike), UNC2452 (FireEye) and Dark Halo (Volexity).
Among the victims are such giants as Microsoft, Cisco, FireEye, as well as many US government agencies, including the US Department of State and the National Nuclear Safety Administration.
Microsoft researchers also reported that Supernova and CosmicGale malware detected on systems running SolarWinds.
Additionally, as it became known earlier from reports of other information security experts, the attackers first deployed the Sunspot malware on the SolarWinds network.
CrowdStrike analysts wrote that this malware was used to inject the Sunburst backdoor into Orion code. The infected versions of Orion went undetected and were active between March and June 2020, while Orion user companies were compromised. According to official figures, among 300,000 SolarWinds customers only 33,000 were using Orion, and the infected version of the platform was installed on approximately 18,000 customers’ machines. At the same time, the hackers developed their attack further only in rare cases, carefully choosing large targets among the victims.
Sunburst itself was not particularly important, it only collected information about the infected network and transmitted this data to a remote server. If, finally, the malware operators decided that the victim was a promising target for the attack, they removed Sunburst and replaced it with the more powerful Teardrop backdoor Trojan.
However, Symantec now reports that in some cases attackers have chosen to use Raindrop malware over Teardrop. Both backdoors have similar functionality and are characterized by researchers as a “downloader for the Cobalt Strike beacon”, that is, they were used by cybercriminals to expand access within the compromised network. However, Raindrop and Teardrop also have differences, which the researchers listed in the table below.
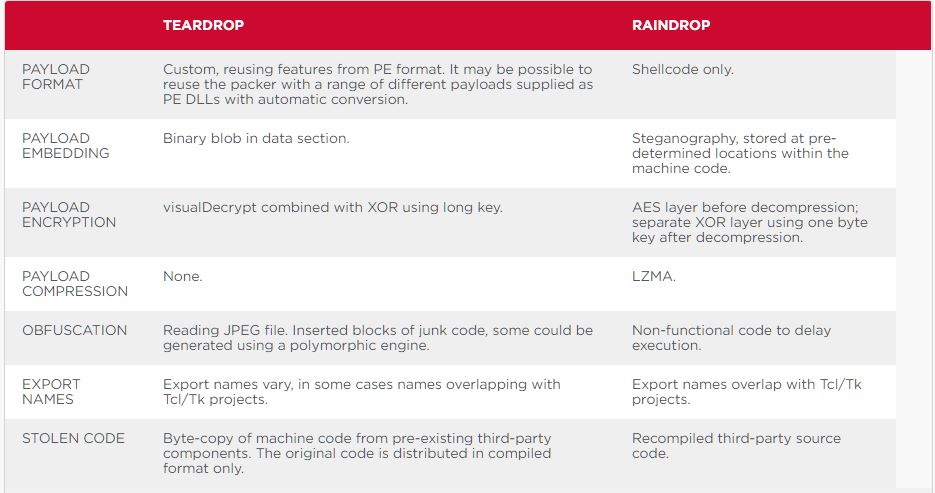
The way malware was deployed was also different. For example, the widely used Teardrop backdoor was installed directly by the Sunburst malware, while Raindrop appeared mysteriously on victims’ systems where Sunburst was also installed, that is, experts have no direct evidence that Sunburst initiated its installation.
It must be said that earlier in the reports of specialists it was already mentioned that Sunburst was used to launch various fileless PowerShell payloads, many of which left almost no traces on infected hosts. It can be assumed that the mysterious “appearance” of Raindrop in the systems of victims was exactly the result of these operations.
Let me remind you that Google experts exposed sophisticated hacking campaign against Windows and Android users.

