Google Project Zero researcher Maddie Stone published a study on 0-day vulnerabilities in 2022 on GitHub called “0-day In-the-Wild Exploitation in 2022…so far”.
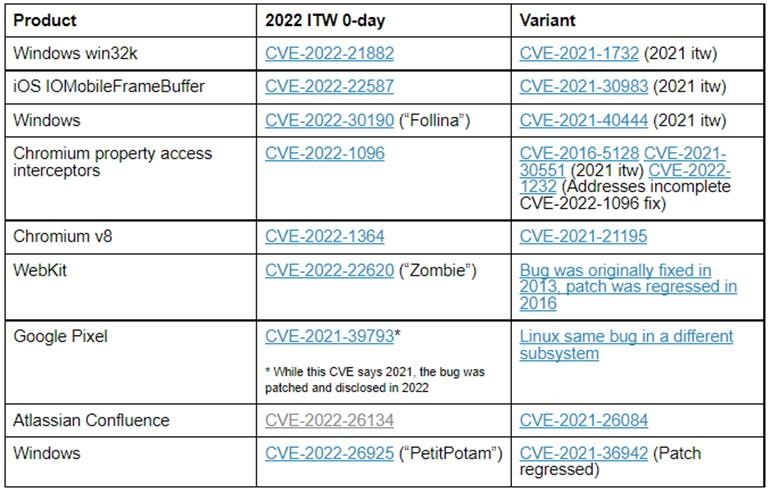
According to Stone, 9 of the 18 exploited zero-day vulnerabilities are variants of previously patched vulnerabilities.
In many cases, the attacks were not sophisticated, and the attacker could have exploited the vulnerability in another way. For example, the recently discovered Follina vulnerability for Windows (CVE-2022-30190) is a variant of CVE-2021-40444 MSHTML.
Let me remind you that we wrote about Russian Hackers Use Follina Vulnerability to Attack Users in Ukraine, as well as Microsoft Fixed Follina Vulnerability and 55 Other Bugs.

Many of the zero days of 2022 are due to the fact that the previous vulnerability was not fully fixed. In the case of win32k and Chromium Windows property access interceptor bugs, the flow of execution that was used to test the concept of exploits was fixed, but the root cause problem was not fixed: the attackers were able to go back and activate the original vulnerability. through another path.
And in the case of problems with WebKit and Windows PetitPotam, the original vulnerability was previously fixed, but at some point regressed so that attackers could exploit the same vulnerability again. In iOS, IOMobileFrameBuffer fixed a buffer overflow error by checking if the size is less than a certain number, but not checking the minimum bound of that size.
A researcher on the Google Project Zero blog gave several examples of 0-day vulnerabilities and their associated variants.
To properly mitigate zero-day vulnerabilities, Google researchers recommend investing in root cause analysis, options, fixes, and exploits.




