Recorded Future, in collaboration with CERT-UA researchers, has unveiled a recent cyber offensive orchestrated by Russian-speaking hackers affiliated with the APT28 Group (also known as Fancy Bear, BlueDelta, Sednit, and Sofacy). Their target: Roundcube mail servers of various Ukrainian organizations, including government entities.
As a reminder, we previously reported on the divergence of hacker groups, some siding with Russia and others with Ukraine. Additionally, Microsoft accused Russia of cyberattacks against Ukraine’s allies.
Recent media coverage also highlighted the arrest of two members of the DoppelPaymer Group by law enforcement in Germany and Ukraine.
The report details that the attackers, employing spear phishing and bait emails, capitalized on the Russian invasion of Ukraine. The hackers crafted spear-phishing emails with news topics related to Ukraine, appearing as legitimate media content.
The campaign demonstrated a high level of readiness by hackers who quickly turned news content into bait for recipients. The spear-phishing emails contained news topics related to Ukraine, with topics and content reflecting legitimate media sources.
Recipients were compelled to open the malicious messages, exploiting old vulnerabilities in Roundcube (CVE-2020-35730, CVE-2020-12641, and CVE-2021-44026) to compromise unpatched servers—requiring no user interaction with malicious attachments.
The attachment contained JavaScript code that executed additional JavaScript payloads from BlueDelta controlled infrastructure.
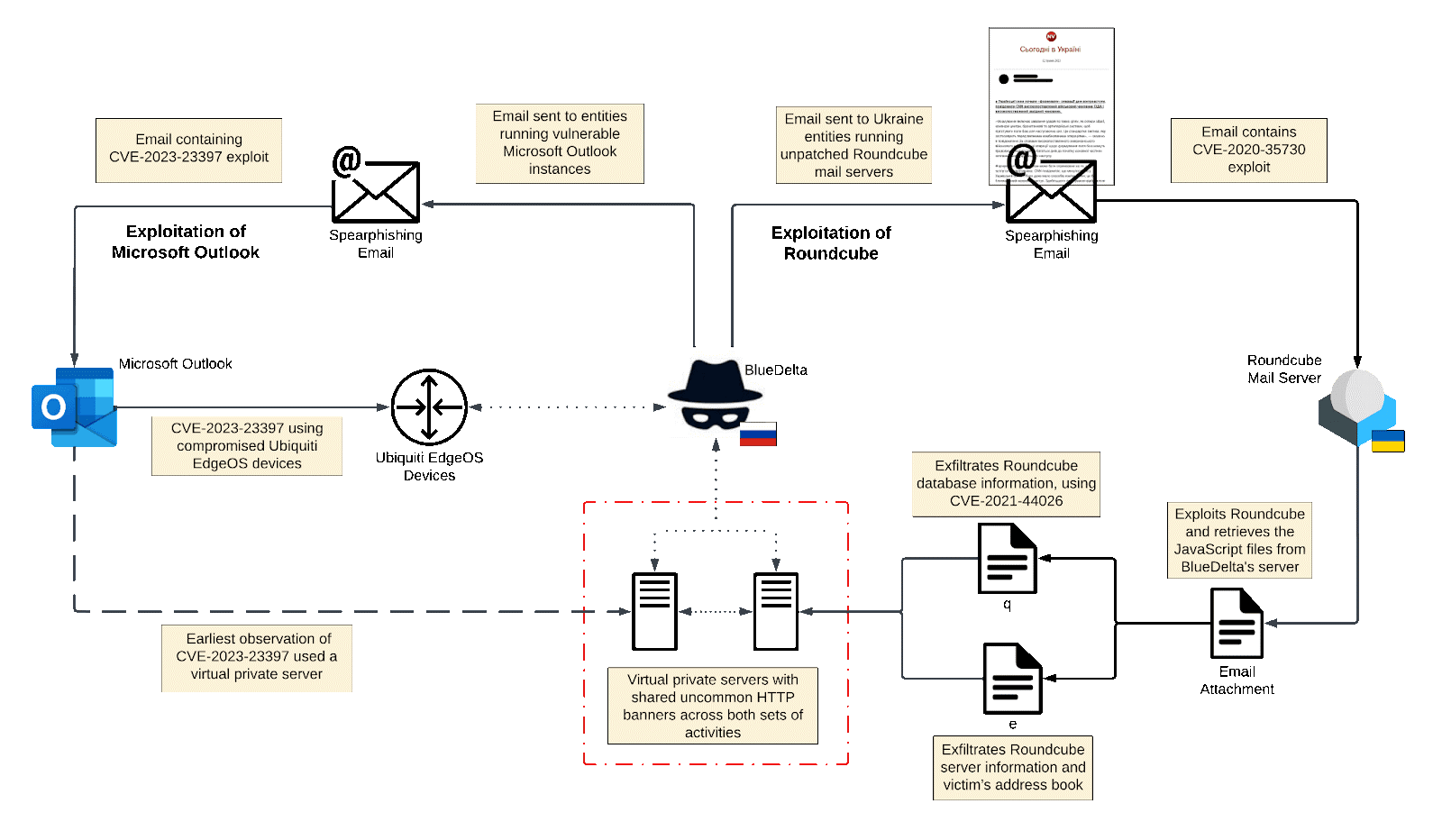
If the compromise succeeded, the attackers deployed malicious scripts redirecting incoming messages to an email address under their control. These scripts were also employed to locate and pilfer victims’ address books, session cookies, and other data stored in the Roundcube database.
Researchers suggest that the infrastructure used in these attacks has been active since around November 2021, with APT28‘s activities focused on “gathering military intelligence.”
We have identified BlueDelta activity, most likely targeted at the regional Ukrainian prosecutor’s office and the [unnamed] central executive body of the country, and also found intelligence activities associated with other Ukrainian state structures and organizations, including those involved in the modernization and repair of infrastructure for the Ukrainian military aviation.
This collaboration between Recorded Future and CERT-UA emphasizes the crucial role of partnerships between organizations and governments in ensuring collective defense against strategic threats—particularly in the context of Russia’s ongoing conflict with Ukraine.




