Organizations face an alarming reality in the digital world: data breaches and cyberattacks are becoming more frequent. Cybercriminals find more opportunities to exploit vulnerabilities as reliance on technology grows, and personal information is collected, stored. One of the primary methods that bad actors use to scam companies is social engineering attacks. Let’s look at crucial access vectors, reasons the companies remain vulnerable, and ways to counteract that.
Key vectors of cyberattacks
History knows dozens of possible ways to attack the organization. Though, among others, there are four most prevalent ones, at least in the modern environment:
Social Engineering
Cybercriminals use psychological tactics to manipulate employees and gain access to sensitive information. They often pretend to be trustworthy figures and communicate through phone calls or emails to obtain valuable information.
Hackers aim to acquire confidential data, carry out fraudulent activities, or take unauthorized control of computer networks or systems. To appear authentic, they often contextualize their messages or impersonate recognizable individuals. Social engineering has several ways: Phishing, Vishing, Baiting, Malware, and Pretexting.
SQL Injection
Cybercriminals can exploit a company’s website or application vulnerabilities by injecting malicious SQL code. This enables them to manipulate the backend database and gain unauthorized access to confidential information.
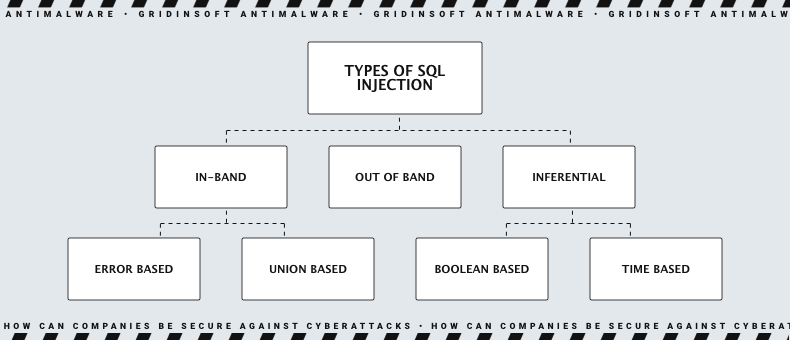
SQL injection has various ways of being used, which can lead to significant issues. An attacker can use SQL injection to bypass authentication, gain access to databases, and alter or delete their contents. Additionally, SQL injection can even be used to execute commands in the Operating system. That enables the attacker to cause even more extensive damage, even if the network is behind a firewall. Generally, SQL injection can categorize into three main types – In-band SQLi, Inferential SQLi, and Out-of-band SQLi.
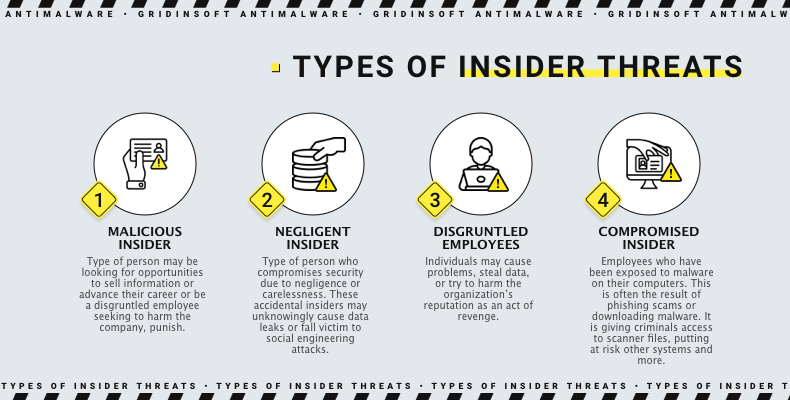
Insider Threats
Sometimes, cybercriminals team up with insiders or take advantage of unhappy employees who can access company data. These individuals might deliberately share or steal confidential information for their benefit or to sell on the dark web.
Internal threats are distinct from external ones because they can operate without detection. They can integrate themselves into the daily workings of the organization. And their actions may remain unnoticed for an extended period. Furthermore, they can perform their tasks without setting off the standard security protocols. It making it hard to recognize and counteract internal threats. Organizations must comprehensively comprehend human behavior, proactive monitoring systems, and a security-conscious mindset to overcome this difficulty.
Vulnerability exploitation
Attackers can create new methods or use existing ones to exploit weaknesses when discovers a vulnerability. They may execute code, bypass access controls, gain higher privileges, launch denial-of-service attacks, or remotely take over the targeted system.
Taking advantage of vulnerabilities can lead to severe outcomes, including unauthorized access to data, theft, modification, or destruction of sensitive information, disruption of services, unauthorized account access, or installing malware or backdoors for continuous access.
Why do hackers attack companies?
- Financial gain is a significant motivation for hackers who steal sensitive information like credit card details, bank account credentials, or customer data to sell on the dark web or use for fraudulent activities. They use ransomware to encrypt a company’s critical data, demanding a ransom for access and threatening to delete or release the data if the victim doesn’t pay.
- One of the primary reasons is to steal intellectual property. Hackers may target a company’s valuable intellectual property, such as trade secrets, patents, or proprietary technology, for theft. Intellectual property theft enables the perpetrator to acquire a competitive edge or trade it to rival entities for financial gain.
- Political motivation has been prevalent recently. This is often referred to as
"Hacktivism". Hacktivists may oppose groups whose ideologies do not coincide with their own. Some state-sponsored actors conduct devastating cyber attacks and claim that their cyber espionage activities are legitimate activities on behalf of the state. - Some hackers are motivated by anger and feelings of revenge. They use their skills to directly affect a person, group, or company without fear of repercussions. Unauthorized sharing or distributing private explicit images or videos to cause distress to the person depicted is considered a criminal act. Despite this, cybercriminals continue to blackmail or take revenge on their victims.
Depending on the hackers’ goals, they can conduct various activities, such as encrypting data and extortion, installing a back door for later access, disrupting systems, or even destroying data.
Biggest cyberattacks of recent time
It is not uncommon to experience an attack in a similar manner to a previous one. It happens frequently. And here are examples of significant attacks:
- A Lithuanian national perpetrated the most significant social engineering attack against two of the world’s biggest companies: Google and Facebook, in 2015. He cheated these companies out of over $100 million.
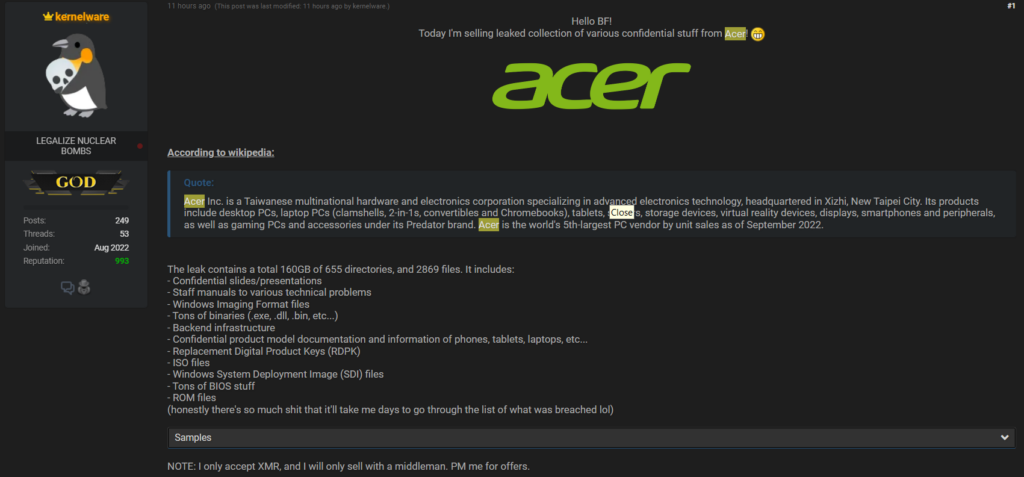
- Acer, the extensive technical company, was hit twice in one week by the same hacker. Acer confirmed a security breach but reassured that only employee data suffered by the hacks in Taiwan.
- Following the attack on MailChimp, there were subsequent cyberattacks, including one on DigitalOcean, a customer of MailChimp, and a cloud service provider. Due to the attack, DigitalOcean experienced communication issues with their customers for a few days and had to ask them to reset their passwords.
Recoveries after an attack often lead to new episodes.
When internal tools become vulnerable and allow for customer data theft, cybercriminals are incentivized to target them. This means the next attack will likely exploit the same vulnerabilities as the previous one. When a cyber incident is made public, the countdown to a copycat attack begins.
Cyberattacks will first use the same methods they used in the first attack. And sometimes, simple password changes are not enough to keep companies safe from sophisticated attacks.
How to prevent companies from impending attacks?
Companies must prioritize protection against cyberattacks, especially the ones that have already happened. In a significant cyberattack, the appropriate response is to reset the organization’s cybersecurity approach and posture completely. Following a powerful attack, every organization must reflect on its actions and decisions.
- The organizational chart must change by hiring senior-level security specialists like a CISO, rearranging reporting structures, or adding cybersecurity experts to the board of directors.
- You must entirely revamp your employee cybersecurity training to ensure better security measures.
- By adopting Zero Trust principles, the security posture can be completely transformed.
- Regularly update the systems. It is essential to regularly update your operating systems, software, and applications with the latest security patches and updates to fix known vulnerabilities.
- Enforce strict access controls, including strong passwords, multi-factor authentication (MFA), and role-based access control (RBAC), to limit unauthorized access to sensitive data and systems.
- Perform regular backups of critical data and ensure that backups are stored securely offline to mitigate the impact of potential ransomware attacks or data breaches.
By adopting robust security strategies, embracing the Zero Trust model, regularly updating and patching systems, providing comprehensive security awareness training, implementing strong access controls, employing network segmentation, using advanced threat detection tools, regularly backing up data, conducting security assessments, and leveraging third-party security services, companies can significantly reduce their vulnerability to cyberattacks.
Organizations must prioritize cybersecurity and continuously adapt their defenses to stay ahead of evolving threats. By doing so, they can safeguard their assets, protect personal data, and keep the trust of their stakeholders in an increasingly digital and interconnected world.




