In the current digital world, organizations face more risks than ever due to fast-paced technological changes. However, while external cyber threats such as hackers and malware often dominate the headlines, there is a lurking danger that often goes unnoticed and is underestimated – the insider threat.
Insider Threat Definition
An insider threat refers to harmful actions taken by individuals authorized to access an organization’s network, applications, or databases. The people with access to the organization’s physical or digital assets include current and former employees and third-party entities such as partners, contractors, or temporary workers. They may also have compromised service accounts. Although the term typically denotes illicit or malicious activity, it can also encompass unintentional harm caused by users to the business.
Insider threats differ from external threats because they can work without being noticed. They can blend in with the organization’s daily activities, and their actions may go unnoticed for a long time. In addition, they can carry out their activities without triggering the usual security measures, making it difficult to identify and mitigate insider threats. To address this challenge, organizations need to have a good understanding of human behavior, proactive monitoring systems, and a culture of security awareness.
How dangerous is that?
Financial motives usually drive data breaches and compromises. Still, they can also occur due to espionage, retaliation, grudges towards employees, carelessness in maintaining security or accessing unlocked or stolen devices. Insider threats are prevalent in specific industries, including healthcare, finance, and government institutions, but any company can be vulnerable to information security risks.
According to a recent Ponemon study, “Cost of Insider Threats: Global Report”, insider threats are becoming a growing problem:
- Over 60% of organizations experience 30 or more insider-related incidents yearly.
- Negligence was responsible for 62% of incidents caused by insiders.
- Out of all insider-related incidents, 23% were caused by criminal insiders.
- User credential theft was responsible for 14% of insider-related incidents.
- Over two years, there was a 47% increase in incidents involving insiders.
- On average, companies spend $755,760 for every incident related to insiders.
Detecting Insider Threats is challenging because the perpetrator has authorized access to the company’s systems and data. Employees must access email, cloud applications, and network resources to perform their duties effectively. Depending on their job functions, some staff members may also need access to sensitive information, such as financials, patents, and customer details.
Since insiders have legitimate credentials and access to the company’s systems and data, they are often considered normal behavior by many security products, and no alerts are triggered. The difficulty of detecting the insider threat increases as the attacks become more complex. For instance, threat actors may use lateral movement to conceal their tracks and gain access to high-value targets. Alternatively, an insider might exploit a system flaw to gain elevated privileges.
Types of Insider Threat
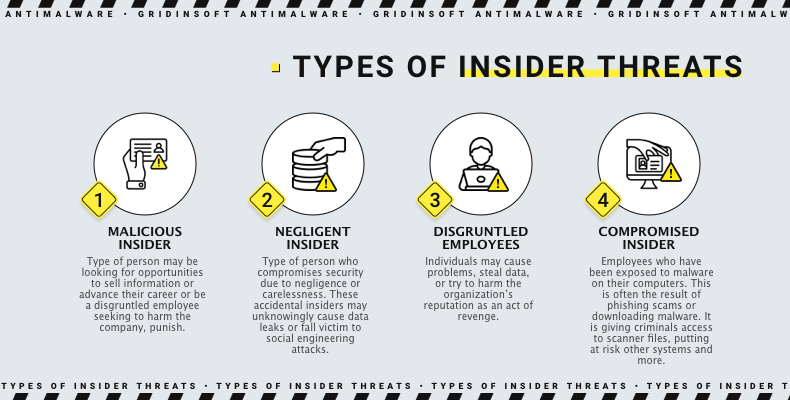
Malicious Insider
A malicious insider is a contractor or employee who intentionally steals information or disrupts operations. This type of person may be looking for opportunities to sell information or advance their career or be a disgruntled employee seeking to harm the company, punish or embarrass them. For example, some Apple engineers were recently charged with data theft after stealing driverless car secrets and sharing them with a China-based company.
Negligent Insider
Insider threat can come from employees or individuals who compromise security due to negligence, carelessness, or lack of awareness. These accidental insiders may unknowingly cause data breaches, open phishing links, or fall victim to social engineering attacks. It is crucial to acknowledge these risks and take measures to avoid them.
Disgruntled Employees
Be aware that employees with negative feelings towards their organization or who have faced personal or professional issues can be a potential danger. Such individuals may cause problems, steal data, or try to harm the organization’s reputation as an act of revenge.
Compromised Insider
It’s common for employees to fall victim to malware infections on their computers. Often through phishing scams or downloading malware through links. These infected devices can become a hub for cybercriminals, giving them access to scan files, compromise other systems, and more. A perfect example of this is a 2020 Twitter breach. Attackers used a phone spear phishing attack to access employee credentials and their internal network. With this information, they targeted employees with access to account support tools. Leading to the successful hacking of high-profile accounts and spreading a cryptocurrency scam that earned over $120,000.
How to mitigate insider threats?
Organizations have various technical and non-technical measures they can implement to detect and prevent each type of insider threat. Each type of threat shows different symptoms, but security teams can proactively address them by understanding the attackers’ motivations. Successful organizations take a comprehensive approach to mitigating the insider threat.
So how to prepare against insider threats?
To prevent insider threats, organizations can take several measures. Here are the primary areas to concentrate on, which are four in number:
1. User behavioral analytics
User Behavior Analytics (UBA), also called User and Entity Behavior Analytics (UEBA), involves tracking, collecting, and analyzing user and machine data to identify organizational threats. UEBA uses different analytical techniques to distinguish between normal and abnormal behaviors. This is typically achieved by gathering data to establish what normal user behavior looks like and then flagging any behavior that deviates from the norm. UEBA can effectively detect unusual online behaviors, such as credential abuse, unique access patterns, and large data uploads, which are often signs of insider threats. Additionally, UEBA can detect these unusual behaviors among compromised insiders well before criminals can access critical systems.
2. Train your employees
Moreover, organizations must provide comprehensive training to their employees, enabling them to recognize and address potentially risky behavior exhibited by their colleagues. Encouraging employees to report such concerns promptly to the Human Resources (HR) department or the Information Technology (IT) security team is essential in proactively mitigating the risks posed by disgruntled individuals who may pose malicious insider threats. Facilitating anonymous tips further enhances the confidentiality and security of such reporting mechanisms.
3. Coordinate IT security and HR
Numerous accounts highlight instances where IT security teams were caught off guard by layoffs, underscoring the need for effective collaboration between the Chief Information Security Officer (CISO) and the HR leadership. These key stakeholders can proactively prepare the IT security infrastructure by fostering a close working relationship. One effective measure involves creating a watchlist of affected employees and implementing behavioral monitoring systems to detect potential threats before they materialize.>
Moreover, HR can play a vital role by sharing pertinent information with the IT security team, such as when certain employees were overlooked for promotions or salary increases. Another valuable strategy involves leveraging input from HR to fine-tune data loss prevention (DLP) tools, enabling the early detection of indicators associated with self-harm and disgruntlement within the organization. By incorporating active thought and collaboration from HR, organizations can establish a robust early warning system to prevent potential security breaches and foster a safer work environment.
4. Frequent password change
Frequent password changes can be one method to mitigate insider threats, but there are better solutions than this one. Insider threats refer to the risks posed by individuals within an organization who have authorized access to sensitive information or systems and misuse that access for malicious purposes. While password changes can help somewhat, a comprehensive approach is necessary to address insider threats effectively.
5. Access Control
To enhance security and mitigate potential risks, it is imperative to establish robust access control measures. These measures should be designed to grant employees access only to the resources and information essential for their designated job roles. Adhering to the principle of least privilege ensures that individuals have the minimum necessary permissions, minimizing the likelihood of misuse or unauthorized access.