D0glun Ransomware: Technical Analysis and Protection Guide
D0glun ransomware emerged in January 2025 as a new crypto-ransomware variant with direct links to the Babuk and Cheng Xilun ransomware families. This sophisticated threat encrypts files using AES-256 encryption, appends the “.@D0glun@” extension to compromised files, and demands Bitcoin payment for decryption. This technical analysis explores D0glun’s infection mechanisms, encryption techniques, and provides actionable protection strategies based on the latest threat intelligence.
Technical Overview
D0glun ransomware shares significant code similarities with the leaked Windows version of Babuk and is a direct descendant of Cheng Xilun (Babuk→Cheng Xilun→D0glun). Security researchers have confirmed these connections through analysis of execution patterns, encryption methods, and ransom note formats. The March 2025 crypto crime report indicates that this family was responsible for several incidents within a broader trend of $124 million stolen across 25 separate ransomware incidents in Q1 2025.
The ransomware features:
- Fast encryption process using AES-256 symmetric encryption for file content
- File extension modification to “.@D0glun@[original_extension]” with additional variant patterns of “@zero_d0glun_[original_extension]”
- Three distinct ransom notes including desktop wallpaper modification
- Chinese-language ransom instructions that appear as corrupted text on systems without Chinese character support
- TOR communication channel for ransom payment and negotiation
- Bitcoin wallet for transaction processing (identified address: 1M7JVws3HccTGd14CV3qX21G7gzcJj77UH)
- Additional communication channels via QQ (424714982) and Telegram (https://t.me/CXL13131)
The first samples of D0glun were identified in January 2025, nearly five years after Cheng Xilun’s initial appearance in April 2020. This timing suggests strategic redeployment of the codebase either by the original threat actor under a new alias or a different group with access to the Cheng Xilun source code.
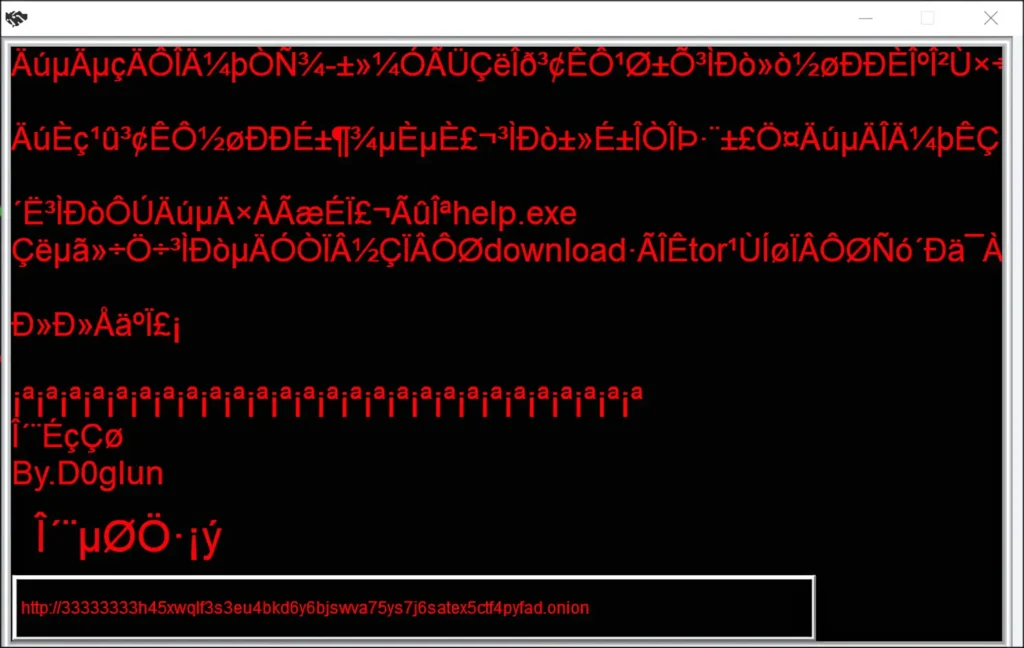
Infection Vectors
D0glun employs multiple distribution methods to infect systems, with recent research from March 2025 identifying exploitation of the Confluence Data Center vulnerability (CVE-2023-22518) as a newly observed attack vector:
Source: WatchGuard’s Ransomware Tracker, combined with GridinSoft Threat Intelligence data, 2025
The most prevalent infection vectors include:
- Phishing campaigns: Emails containing malicious attachments or links that, when opened, download and execute the ransomware payload through PowerShell scripts
- Remote Desktop Protocol (RDP) exploitation: Targeting systems with weak or default credentials or unpatched RDP vulnerabilities
- Fake software updates: Posing as legitimate application updates that actually contain the ransomware payload
- Confluence CVE-2023-22518 exploitation: Targeting the improper authorization vulnerability in Confluence Data Center and Server that allows unauthenticated attackers to reset Confluence and create administrator accounts
- Supply chain attacks: Compromising legitimate software distribution channels to deliver the payload
- Malicious torrent files: Hiding within pirated software, games, or media distributed through P2P networks
According to security reports, organizations in manufacturing, healthcare, and business services sectors are primary targets, with most infections occurring in North America and Europe, but also reported cases in Brazil, Argentina, South Africa, and Japan.
Technical Capabilities and Execution Flow
When executing on a compromised system, D0glun follows a methodical process:
- Initial setup: Creates mutex “hsfjuukjzloqu28oajh727190” to prevent multiple instances from running
- System reconnaissance: Collects system information, installed software details, and network configuration
- Credential harvesting: Attempts to extract credentials from FTP clients, VNC software, browsers, and email applications
- Defense evasion: Disables Windows Defender, modifies security settings, and employs anti-debugging techniques
- Persistence establishment: Creates registry entries to ensure execution after system restart
- Backup destruction: Executes “vssadmin delete shadows /all /quiet” to remove shadow copies
- File encryption: Systematically encrypts over 200 file types including documents, images, databases across local drives and network shares
- Ransom note deployment: Drops ransom notes in each directory and changes desktop wallpaper
- Self-cleanup: Deletes artifacts and potentially removes itself after encryption is complete
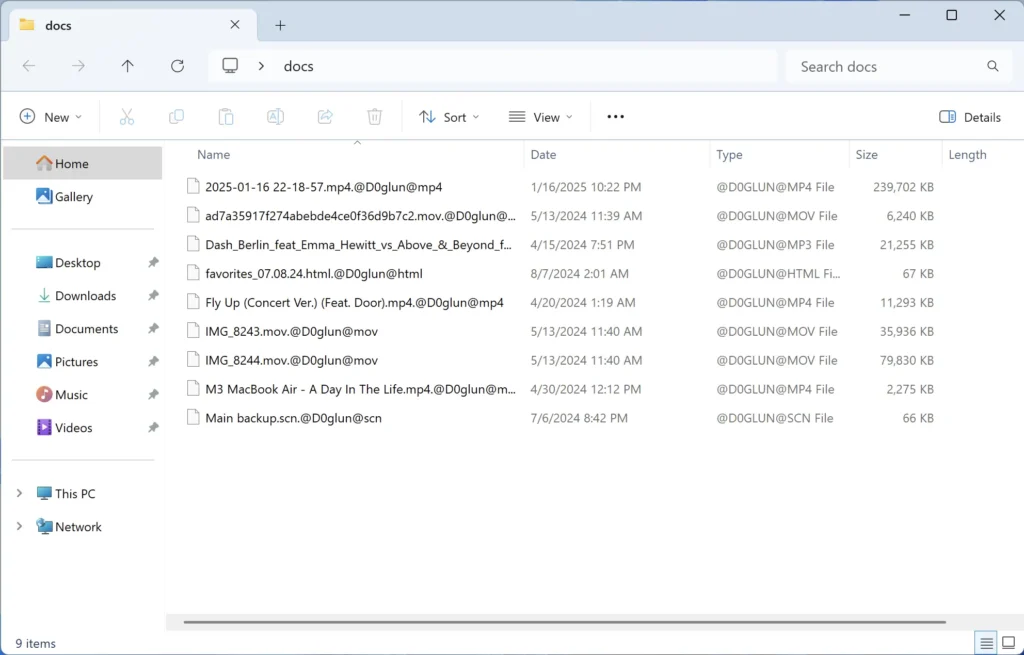
D0glun avoids encrypting files with specific extensions to maintain system functionality:
- .dat – Common data files needed by many applications
- .dll – Dynamic Link Libraries required for system operation
- .exe – Executable files that may be needed to run processes
- .ini – Configuration files for Windows and applications
- .log – System log files that track events
- .sys – System files critical for operating system function
Analysis of sample hash a8df7571e871d22f13ba3eb376eddd1f73ce241d24caa878494e1805219b342a reveals that D0glun uses a sophisticated multi-stage infection process linked to the Confluence exploit:
- Initial exploitation of CVE-2023-22518 to create admin credentials
- Execution of PowerShell scripts to download the main ransomware payload (typically named “svcPrvinit.exe”)
- Deployment via C&C servers at 193.176.179.41 and 193.43.72.11
- Execution with command-line parameters for silent operation
Encryption Methodology
D0glun employs a sophisticated encryption strategy:
- Generates a unique AES-256 symmetric key for file encryption
- Encrypts the AES key using an embedded RSA-2048 public key
- Only the threat actors possess the corresponding private RSA key needed for decryption
- Creates identifiable patterns in encrypted files to verify ownership during ransom negotiation
This approach makes decryption impossible without obtaining the private key from the attackers, as the asymmetric RSA encryption securely protects the symmetric AES key used for file encryption.
Ransom Note Analysis
The D0glun ransom note appears in Chinese, creating additional complications for victims without Chinese language support on their systems. Translation reveals several notable elements:
Your files are encrypted.
What's wrong with my computer?
I've encrypted some of your files.
File types include ZIP|TXT|PNG|JPG|PDF|DOC|and other common file formats.
---------- ---------- ------
Please do not try any antivirus software before decryption, otherwise I can not guarantee the safety of your files!
-------------------------------------------------------
How do I recover my important files?
--------------------------------------
Files with @D0GLUN@+source file suffix.
Such files can only be decrypted by our decryption service.
Trying any other decryption method will be futile.
Please visit our Dark Web site and we will provide you with a specialized decryption service.
Of course, there is a fee for this service
======================================
Can we really decrypt it?
======================================
We will honor our word of honor
We can decrypt a small part of your file for free
to prove that we can actually decrypt it!
---------- ----------
Please download the Tor Browser to your right
Then visit the following address
-
Contact us for help
In the lower right corner is my BTC collection address
Key ransom note elements include:
- Claims that antivirus will damage encrypted files (false intimidation tactic)
- TOR onion address: hxxp://33333333h45xwqlf3s3eu4bkd6y6bjswva75ys7j6satex5ctf4pyfad.onion
- Bitcoin wallet address: 1M7JVws3HccTGd14CV3qX21G7gzcJj77UH
- QQ communication channel: 424714982
- Telegram contact: https://t.me/CXL13131
The ransom note follows patterns similar to Cheng Xilun, further confirming the relationship between these ransomware families. The attackers typically offer to decrypt a small sample file to demonstrate their capability to restore data.
MITRE ATT&CK Techniques
D0glun employs various techniques mapped to the MITRE ATT&CK framework:
- T1486: Data Encrypted for Impact – Primary ransomware function to encrypt victim files
- T1490: Inhibit System Recovery – Deletion of shadow copies and backup mechanisms
- T1082: System Information Discovery – Collection of system details to tailor the attack
- T1562.001: Disable or Modify Tools – Disabling security software to evade detection
- T1083: File and Directory Discovery – Enumeration of files for targeting
- T1112: Modify Registry – Creation of registry entries for persistence
- T1059.001: PowerShell – Use of PowerShell scripts for execution
- T1047: Windows Management Instrumentation – Leveraging WMI for system manipulation
Protection and Remediation
If your system becomes infected with D0glun ransomware, follow these essential steps:
Immediate Response
- Immediately disconnect from all networks to prevent spread to other systems
- Disconnect external storage devices
- Document the ransomware attack details (ransom note, encrypted file examples, contact information)
- Report the incident to local law enforcement and national cybersecurity agencies
Ransomware Removal
To remove D0glun ransomware, use specialized security software that can detect and eliminate this threat:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Note that removing the ransomware only prevents further file encryption; it does not recover already encrypted files.
File Recovery Options
Currently, no free decryptor exists for D0glun ransomware. Your recovery options include:
- Restore from backups: The most reliable recovery method is restoring from clean, disconnected backups
- Shadow Volume Copies: If not deleted by the ransomware, Windows Shadow Copies might contain previous versions of files
- Cloud storage versions: Services like OneDrive, Google Drive, and Dropbox may have previous file versions if versioning was enabled
- Data recovery tools: In some cases, specialized tools like EaseUS Data Recovery might be able to recover fragments of files
Security experts and law enforcement agencies strongly advise against paying the ransom, as payment:
- Does not guarantee file recovery
- Finances criminal operations
- Marks you as a willing payer, potentially leading to future attacks
Prevention Strategies
Implement these security measures to protect against D0glun and similar ransomware:
- Patch management: Apply security updates promptly, especially for Confluence and remote access technologies
- Immutable backups: Maintain 3-2-1 backup strategy (3 copies, 2 different media types, 1 off-site) on write-once media
- Email security: Implement advanced anti-phishing protection and user awareness training
- Network security: Secure RDP access with multi-factor authentication and limit external exposure
- Endpoint protection: Deploy modern anti-malware solutions with behavioral detection capabilities
- Least privilege: Restrict user permissions to reduce the impact of successful attacks
- Network segmentation: Isolate critical systems to limit lateral movement
- Application control: Implement application whitelisting to prevent unauthorized executables
- Network monitoring: Deploy intrusion detection systems to identify unusual activity
Organizations should also develop and regularly test incident response plans specific to ransomware attacks to minimize recovery time and data loss.
Technical Indicators of Compromise (IOCs)
Security teams should monitor for these D0glun indicators:
File Hashes (SHA-256):
3eb7f1dd0274bd4ffcdf463876ab547503f9e6120db22c5e1923fe16cab71b50
a8df7571e871d22f13ba3eb376eddd1f73ce241d24caa878494e1805219b342a
d6d55a8fbd1c603719fe611e572e2431512e7063c44896f705524dab66234d45
f549ae8d509dab97f2d8b12ecf344c72ab2e715b2667e78d8fdd892eb6a459de
bec9d2dcd9565bb245f5c8beca4db627390bcb4699dd5da192cc8aba895e0e6a
IP Addresses:
193.176.179.41
193.43.72.11
45.145.6.112
File Extensions:
.@D0glun@<original extension>
.<original extension>.@d0glun@<original extension>
.<original extension>.@zero_d0glun_<original extension>
Ransom Note Files:
@[email protected]
Desktopcxl.txt
help.exe
Mutex:
hsfjuukjzloqu28oajh727190
Communication:
TOR: http://33333333h45xwqlf3s3eu4bkd6y6bjswva75ys7j6satex5ctf4pyfad.onion
QQ: 424714982
Telegram: https://t.me/CXL13131
BTC: 1M7JVws3HccTGd14CV3qX21G7gzcJj77UH
Process Names:
svcPrvinit.exe
Conclusion
D0glun ransomware represents a continuing evolution of the Babuk/Cheng Xilun ransomware lineage with significant technical enhancements. Its emergence in 2025 and recent exploitation of Confluence vulnerabilities demonstrates how threat actors recycle, modify, and improve existing ransomware code to create new threats. The Chinese language elements and possible connection to North Korean actors (based on similar TTPs observed in other campaigns) suggest a complex attribution picture that continues to evolve.
Organizations must maintain strong security postures, implement comprehensive backup strategies, and deploy modern endpoint protection solutions like GridinSoft Anti-Malware to defend against these evolving threats. For additional protection against online threats, consider using the Website Reputation Checker to verify the safety of web resources before access.
Is D0glun ransomware targeting specific industries?
Yes, D0glun primarily targets manufacturing, healthcare, and business services sectors. Most infections have been reported in North America and Europe, but the ransomware has global reach including South America, Africa, and Asia. Organizations in these industries should implement enhanced security measures including offline backups, network segmentation, and advanced endpoint protection. The recent campaign targeting Confluence servers has particularly affected organizations that haven’t patched CVE-2023-22518.
Can files encrypted by D0glun be recovered without paying the ransom?
Currently, no free decryption tool exists for D0glun ransomware. The most reliable recovery method is restoring from clean backups that were disconnected or stored separately from the infected system. Other potential recovery options include checking for Windows Shadow Volume Copies (if not deleted by the ransomware) or previous versions in cloud storage services. Security experts strongly advise against paying the ransom, as payment does not guarantee file recovery and finances criminal operations. The AES-256 encryption with RSA-2048 key protection makes brute-force decryption computationally infeasible.
What is the relationship between D0glun and earlier ransomware variants?
D0glun is directly related to the Babuk and Cheng Xilun ransomware families, following the lineage: Babuk → Cheng Xilun → D0glun. Technical analysis confirms similarities in code structure, encryption methods (AES-256), execution patterns, and ransom note formats. Cheng Xilun first appeared in April 2020, while D0glun emerged in January 2025, suggesting either the return of the original threat actor under a new alias or a different individual with access to the Cheng Xilun codebase. The ransomware has been significantly enhanced with new exploitation techniques, particularly targeting Confluence servers through CVE-2023-22518.
How does D0glun exploit the Confluence vulnerability?
D0glun exploits CVE-2023-22518, an improper authorization vulnerability in Confluence Data Center and Server. This vulnerability allows unauthenticated attackers to reset Confluence and create administrator accounts. Once administrative access is obtained, the attackers execute PowerShell commands to download and run the ransomware payload, typically named “svcPrvinit.exe”, from command and control servers. This attack vector first emerged in early November 2023, just one day after the vulnerability was disclosed, and has been incorporated into D0glun’s arsenal in 2025. Organizations should immediately patch Confluence installations and implement network segmentation to limit potential damage.




