Researchers have created a side-channel attack called “Freaky Leaky SMS”, which allows finding out the location of the recipient of messages, based on the delivery time of reports on the receipt of SMS messages.
Let me remind you that we also wrote about true Apocalypse Now: experts presented a new type of cyber-biological attack, and also that Researchers hacked TikTok app via SMS.
And also the media reported that Researchers Suggest Using EMFI to Hack Drones.
Experts say that in the mobile network, SMS delivery reports are processed by the SMSC (Short Message Service Center) and are needed to inform that the message was delivered, accepted, not delivered, sending failed, was rejected, and so on.
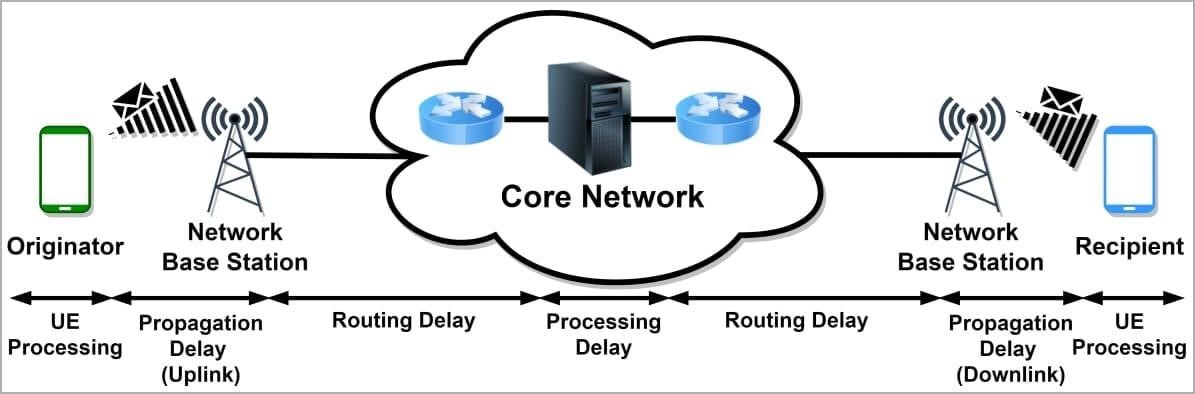
Although there are routing delays in this process, the immutable nature of mobile networks and their specific physical characteristics allow a time-predictable result if the signal follows a standard paths.
Researchers have created a machine learning algorithm that analyzes the response time of SMS responses and uses this to determine the location of the recipient of a message with an accuracy of up to 96% (for locations in different countries) and up to 86% (for two locations within the same country).
Before launching an attack, an attacker must collect certain metrics in order to establish a connection between SMS delivery reports and known locations of their target. The more accurate this location data is, the more accurate the results presented in machine learning model predictions will be.
In order to collect data, the attacker must send multiple SMS messages to their target, either disguising them as marketing messages that the recipient will ignore or mistake for spam, or using “silent” SMS messages (type 0 messages with no content that do not display notifications on the screen recipient, but their receipt is acknowledged by the device and SMSC).
The authors of the study used ADB to send packets of 20 “silent” SMS messages and sent them to several test devices in the US, UAE and seven European countries (covering ten carriers and various generations of communication technologies) every hour, on for three days.
They then measured the time to receive SMS delivery reports in each case and combined this data with the corresponding location signatures to create a machine learning dataset.
Overall, the researchers report that their model is highly accurate and distinguishes between domestic and foreign locations quite accurately (96%), performs well in identifying a specific country (92%), and performs fairly well for locations within the same region (62– 75%).
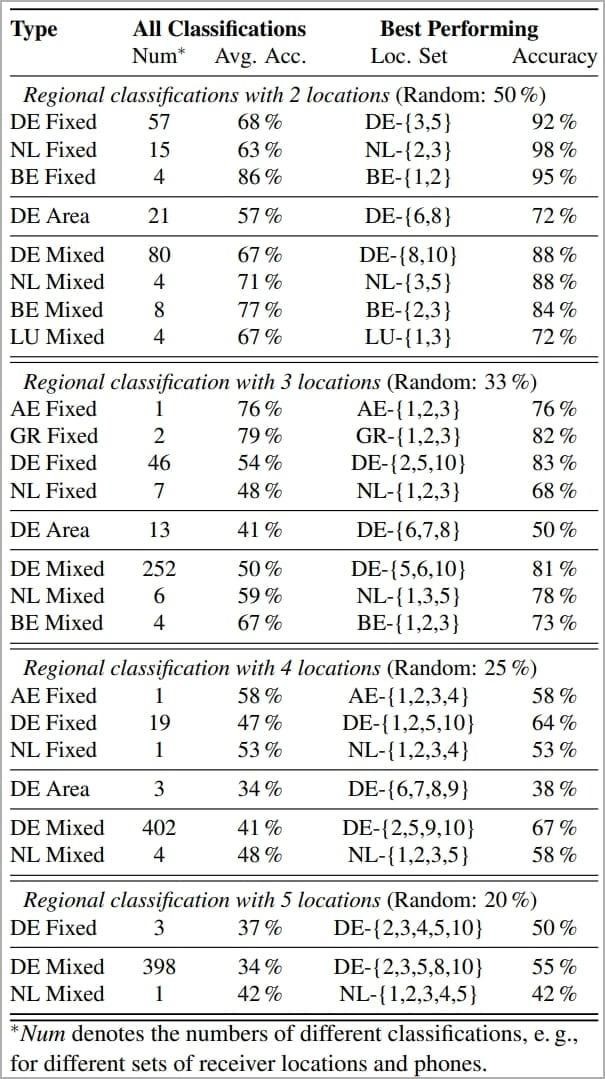
At the same time, the accuracy of the results depends on the specific location, telecom operator and a number of conditions. For example, in Germany, the model showed an average accuracy of 68% across 57 different classifications, but the best performance was 92% in a particular region. And Belgium showed the best results of all: an average of 86% correct answers and up to 95% accuracy in one of the regions.
For the time being, researchers have left cases of “open world”, that is, situations where their target visits unknown places, for the future. However, the paper briefly explains that the model can be adapted to such scenarios as well.
Although the attack requires a lot of preparatory work, does not work in all cases, and has a number of limitations, it still poses a significant risk to user privacy. Thus, experienced attackers with a lot of resources and time may well achieve good results and effective attacks.