The forums on the dark web are well-known for being a hub of cybercriminal activity, including an auction system. Here, bad actors can trade tips on hacking, share samples of malware, and demonstrate how to exploit vulnerabilities. For those who develop malware, Darknet communication platforms, specifically forums, became a perfect marketing platform. The developers of questionable or dual-purpose software appreciate such a law-free place as well. Here, I’ve picked 6 malware samples that are promoted actively on the Darknet.
EvilExtractor Stealer
The developers of EvilExtractor present it as a legitimate subscription-based tool. However, researchers have discovered that it has been advertised to threat actors on multiple hacking forums since 2022. Attackers use it to steal sensitive information, particularly data from web browsers. Kodex created it and it has been regularly updated since its release in October 2022.
Most infections occurred due to a phishing campaign. There attackers sent account confirmation requests with a compressed executable attachment resembling a legitimate PDF or Dropbox file. Fortinet discovered several such attacks. When the target opens the file, a PyInstaller file is executed, which launches a .NET loader that further launches an EvilExtractor executable using a base64-encoded PowerShell script. To avoid detection, the malware checks the system time and hostname on launch to determine if it is running in a virtual environment. If it is, the malware will exit.
Trigona affiliate program
One of the Darknet forums offers an affiliate program Trigona. The Trigona ransomware was initially detected in October 2022 and has gained notoriety for exclusively demanding ransom payments in Monero cryptocurrency. In the short time it has been active, this group has victimized people globally.
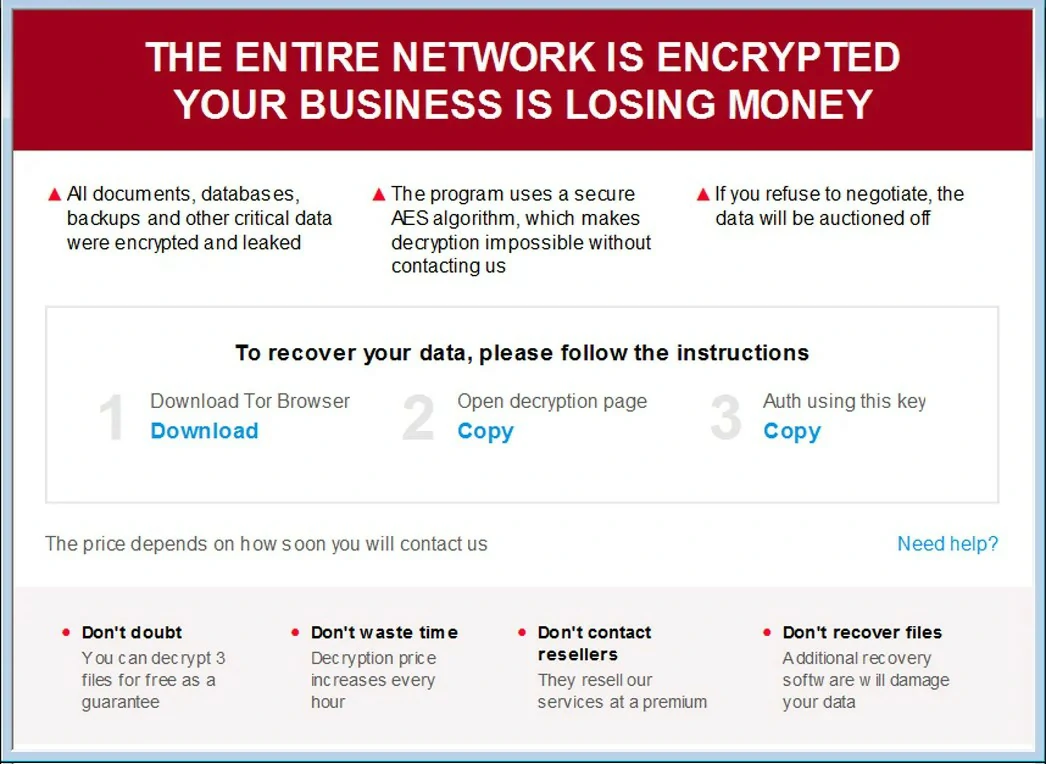
Trigona is a group that hacks into victims’ devices and encrypts all their files, except those in specific folders such as the Program Files and Windows directories. Additionally, they steal sensitive documents and add them to their dark web leak site before encrypting them. This program provides ransomware-as-a-service (RaaS) and has several capabilities:
- The Tor network’s admin panel comes equipped with end-to-end encryption for all data.
- Storing leaked databases on the cloud.
- Cross-platform build with cryptographically advanced encryption.
- DDoS capabilities.
- Call facilities for countries across the globe.
Shadow Vault – MacOS Stealer
A malware called RedLine Stealer is being sold on underground forums. It is specifically designed to target users of MacOS. A harmful software known as malware is designed to extract sensitive information from internet browsers, such as saved login details, autocomplete data, and credit card information. Once installed on a computer, it takes an inventory of the system, collecting details like the username, location data, hardware configuration, and information on installed security software. The latest versions of RedLine can even steal cryptocurrency. This malware targets FTP and IM clients and can upload and download files, execute commands, and periodically send information about the infected computer.
- This software has a keylogging function that records keystrokes and creates several copies of the stolen data. These copies are saved in various locations so the information can still be retrieved even if deleted.
- The extractor can grab data from Metamask, Exodus, Coinomi, Binance, Coinbase, Martian, Atomic, Phantom, Trust, Tron Link, Kepler, etc.
- This software can be installed using either PKG or DMG file formats.
- The process of extracting data from Apple devices’ keychain database is encrypted, making it difficult to detect the amount of stolen information and avoid being caught.
Mystic Stealer’s rise
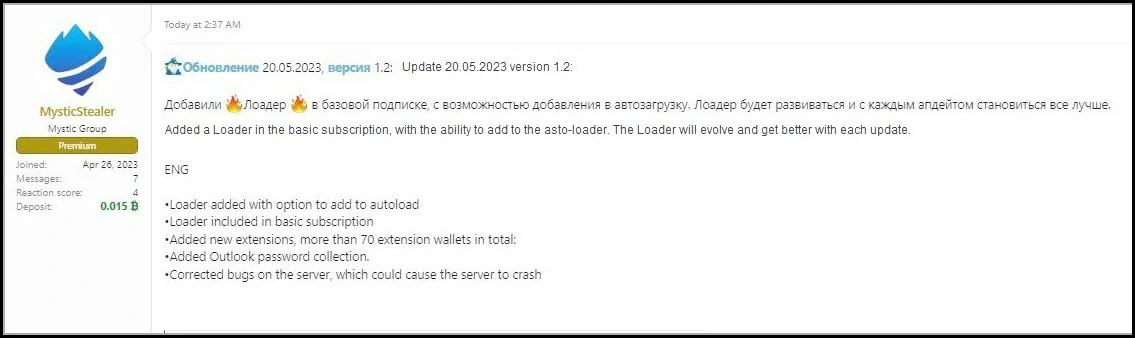
A new version of Mystic Stealer, version 1.0, was released in late April 2023, but an updated version, 1.2, was quickly launched in May, indicating that the project is actively being developed. The seller is advertising the malware on various hacking forums, such as WWH-Club, BHF, and XSS, and is available for rent to interested parties.
Mystic is capable of stealing login credentials from nearly 40 different web browsers, such as Chrome, Edge, Firefox, and Opera (but not Safari), as well as over 70 browser extensions, including Coinbase Wallet, Dashlane, and LastPass.
- The Mystic Stealer is capable of operating on different Windows versions, ranging from XP to 11, and is compatible with 32-bit and 64-bit OS architectures.
- It works in a computer’s memory to avoid detection from anti-virus software.
- The C2 communication is encrypted using a unique binary protocol over TCP. Also, any stolen data is directly sent to the server without being stored on the disk.
- Mystic performs multiple anti-virtualization checks, including examining the CPUID information to confirm that it is not being run in a sandboxed environment.
Akira ransomware
In March of 2023, cybercriminals began using a new ransomware called Akira. This ransomware encrypts data and changes the filenames of all affected files by adding the extension “.akira”. It also creates a ransom note called “akira_readme.txt”. The letter claims that the company’s internal infrastructure has been partially or fully shut down and that all backups have been deleted.
The attackers also state that they obtained important corporate data before encryption. The ransom note offers a negotiation process with reasonable demands and promises not to ruin the company financially. It includes instructions on accessing a chat room through a Tor browser and a login code. The attackers emphasize that the quicker the company responds, the less damage will be caused. Akira has released information about four individuals on their data leak website. The amount of leaked data varies from 5.9 GB for one company to 259 GB for another.
LummaC2 Stealer
In December 2022, LummaC2 was introduced on cybercrime forums. Since then, it has been continuously developed and has become a highly advanced yet reasonably priced information-stealing malware. This malware, available as a service, is around 150-200 KB in size and is designed to extract data from several browsers, such as Chrome, Chromium, Mozilla Firefox, Microsoft Edge, and Brave. Its primary target is the latest Windows operating system, from 7 to 11.
Recent updates have been made to LummaC2 that involve improving its security by redesigning the modules used for creating harmful builds and receiving stolen logs. Additionally, a new module with a load balancer already added. The developers have also advertised their MaaS on a well-known Russian language forum frequently used by RaaS operators to promote their affiliate and partnership programs.
So what?
Darknet forum sites provide their member’s anonymity, letting them freely share their ideas, thoughts, and expertise. As a result, these online communities are valuable intelligence sources for cybersecurity professionals. The impact of the dark web on businesses across various industries highlights the need for a thorough understanding of cyber threats and effective defensive strategies.
To safeguard your organization from the dangers of the dark web and stay one step ahead of cybercriminals, it’s essential to adopt a proactive approach. Cybersecurity experts monitor threat actor communities on the clear and dark web, illicit Telegram channels, and other messengers.
Law enforcement recently shut down the widely popular Darknet forums. As a result, the Darknet community is curious to see which forums will take their place. The Popular Forums provided a one-stop-shop for a vast amount of data, with vetted postings, and users considered it a reliable intermediary for vendor transactions. However, the increased popularity of leak-focused Telegram channels and sites indicates a trend toward decentralization. This trend highlights that small groups and individuals are selling leaked data, not just ransomware groups. Therefore, individuals have more decentralized options to buy, sell, and download leaked data.





