Trustwave SpiderLabs specialists spoke about the new Rilide malware, which steals confidential data and cryptocurrency, targeting Chromium browsers.
Basically, Rilide masks as a legitimate Google Drive extension.
Let me remind you that we also wrote that has Specialists Discovered a New Version of Malware from Russian Hackers LOLI Stealer.
Moreover, the malware can display fake dialog boxes to force users to enter a two-factor authentication code to confirm the transfer of digital assets.
Analysts write that they immediately identified two different campaigns involving Ekipa RAT and Aurora Stealer, which led to the installation of a malicious extension. If Ekipa RAT is distributed through malicious Microsoft Publisher files, then Aurora Stealer is mainly distributed through fraudulent ads in Google Ads.
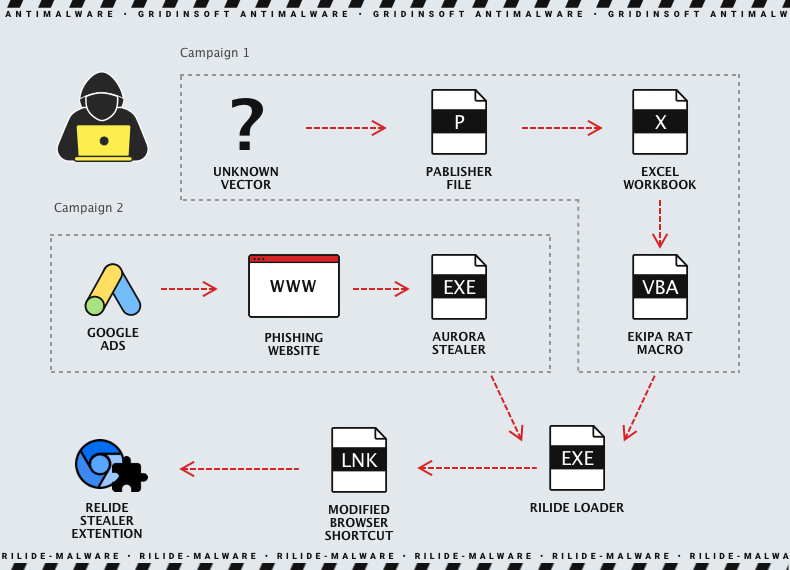
Attack scheme
Both chains of attacks lead to the execution of the Rust loader, which in turn modifies the browser LNK file and uses –load-extension to launch the extension.
Who is behind these attacks is still unclear, but experts managed to find a post on a hacker forum made back in March 2022. This message advertised the sale of a botnet with similar functions, and since then, part of the source code of the malware has been released to the public due to an unresolved dispute over payment.
The report also notes that the C&C address provided in the Rilide code identified GitHub repositories owned by a user with gulantin that contain loaders for the malicious extension.
The researchers say the upcoming move to Manifest v3, which defines the capabilities and limits for extensions, could make it harder for attackers to work, but it’s unlikely to completely solve the problem, as most of the functionality used by Rilide will still work.
Last fall, The Developers Postponed the Release of Manifest V3 to 2024, but it should be noted that the other day the transition to Manifest V3 was again postponed. This time, Google developers do not give exact terms at all, but they promise that the creators of extensions will have enough time to transit – at least six months.




