Cyble Research Labs specialists found a sample of malware in the wild, which turned out to be an updated version of a previously discovered malware named LOLI Stealer.
Let me remind you that we also reported that FFDroider Stealer is the new hazard to your social networks, and also that STOP Ransomware Spreads through Discord, Carrying RedLine Stealer.
LOLI Stealer is an information stealer that extracts sensitive data from the victim’s computer such as passwords, cookies, screenshots, etc.
Reports of this malware first surfaced on cybercrime forums around June 2022.
Cybercriminal forum post about LOLI Stealer
This software was sold at fairly low prices:
- 499 rubles (~9 USD) – month
- 799 rubles (~14 USD) – 2 months
- 1499 rubles (~25 USD) – for life + universal sorter as a gift.
The attackers claimed that the malware has the following features:
- Theft of passwords, cookies, history, etc. from a huge number of browsers based on Chromium
- Collection of information from 10 cryptocurrency wallets
- Extracting session data from Telegram and Steam apps.
Cyble Research Labs has identified more than 20 different samples associated with LOLI malware since June 2022, which they say is indicative of active malware deployment, especially in the last month
After analyzing the malware file line by line, Cyble revealed that it was a binary file of a program written in Golang.
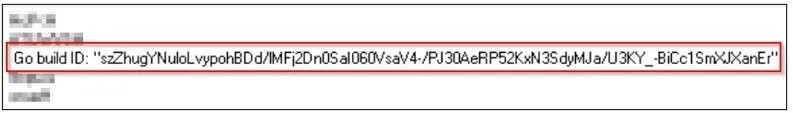
Go build ID
After launching a malicious LOLI file, Stealer attempts to determine if the file is running under WINE by checking the wine_get_version() function via theGetProcAddress() API.
The malware then creates a new folder with a random name in the %homepath% folder and will use it to store the stolen information
After that, the hijacker starts extracting information about cryptocurrency wallets by requesting and reading files from standard directories that are created by the corresponding software and saving them in a subfolder named “Wallets”.
After extracting the cryptocurrency wallet data, the malware looks for the following browser-related files stored in “SQLite format 3”:
- Cookies
- Passwords
- History
- Autofill
- Shortcuts
- Bookmarks
In addition, if Telegram and Steam applications are installed on the victim’s computer, LOLI Stealer looks for configuration files for these programs and saves them in the “Telegram” and “Steam” folders, respectively.
The thief then extracts all the text files from the Desktop folder and stores them in the Grab Files folder. It also takes a screenshot of the victim’s machine using the BitBlt() API from the Gdi32.dll library and saves it under the name “WebStealer.png”.
And then the malware starts processing browser-related “SQLite format 3” files, extracts sensitive information and saves it in a text file.
LOLI Stealer hunts down the passwords of all browsers and saves them to a new “Passwords.txt” file.
After collecting all the information, the thief creates a ZIP archive of the stolen files for transmission to attackers.
The hijacker then sends a Base64 encoded ZIP file along with the amount and status of the stolen data to the URL:
hxxp[:]//webStealer[.]ru/gate[.]php.
After exfiltration, the hijacker deletes all collected files from the folder that was previously created by the malware using the DeleteFileW() API function
Attackers often choose to use new toolkits that help them brush up on their tactics, methods, and procedures and avoid detection. LOLI Stealer is just such a rather “fresh” tool.




