A new malware campaign by the North Korean hacker group Lazarus has been discovered, which was active from February to July 2022. This time the hackers have targeted energy suppliers around the world, including companies in the US, Canada and Japan.
Let me remind you that we also reported that Microsoft accused Russia and North Korea of attacks on pharmaceutical companies, and also that Cybersecurity researchers discovered the Chinese hack group Earth Lusca.
Cisco Talos experts talk about the new campaign, according to which, the goal of Lazarus was “to infiltrate organizations around the world to establish long-term access and subsequent theft of data of interest to the enemy state.”
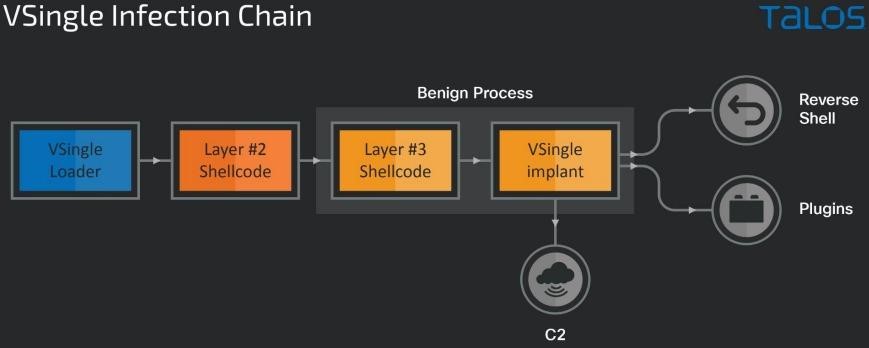
Whereas earlier Lazarus attacks resulted in the use of Preft (Dtrack) and NukeSped (Manuscrypt) malware, the new campaign was notable for the use of a number of other malware: the VSingle HTTP bot, which executes arbitrary code on a remote network; YamaBot backdoor written in Go; as well as the previously unknown Remote Access Trojan (RAT) MagicRAT, which has been used to find and steal data from infected devices, but can also be used to launch additional payloads on infected systems.
It is worth saying that Symantec and AhnLab analysts have already written about this activity of Lazarus, but the latest Cisco report turned out to be more in-depth and reveals much more details about the activities of hackers.
It is known that Lazarus obtained initial access to the corporate networks of its victims by exploiting vulnerabilities in VMware products (for example, Log4Shell). These problems have been used to run shellcode, create reverse shells, and execute arbitrary commands on a compromised machine.
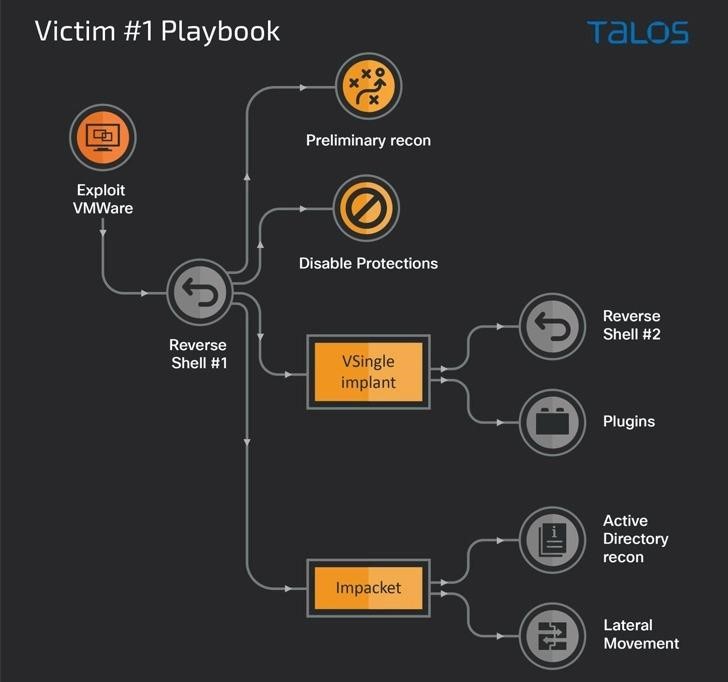
Thus, the use of VSingle malware in one of the attacks allowed the attackers to perform various actions, including reconnaissance, data theft, and manual installation of backdoors, which gave them a clear understanding of the victim’s environment. In essence, this malware sets the stage for credential theft, creates new admin users on the host, and installs a reverse shell to communicate with the command and control server and download plugins that extend its functionality.
In another case, after gaining initial access and conducting reconnaissance, the hackers used not only VSingle, but also MagicRAT, to which the researchers paid special attention and devoted a separate post.
The Trojan is able to fix itself in the victim’s system by executing hard-coded commands and creating scheduled tasks, conduct reconnaissance and extract additional malware from the command-and-control server (such as TigerRAT).
In the third case, Lazarus deployed the YamaBot malware to the affected systems, written in Go and having standard RAT features:
- listing files and directories;
- transferring information about processes to the control server;
- downloading remote files;
- execution of arbitrary commands and self-destruction.
It is also noted that the group often used not only its own tools, but also collected credentials in the victim’s networks using such well-known solutions as Mimikatz and Procdump, disabled anti-virus components and Active Directory services, and also took measures to cover up traces after backdoors were activated.





What about the safety of transformers???