You may have come across a Web Application Firewall (WAF) concept but have yet to give it much thought. However, it is essential to understand what a WAF is to decide if it is right for you. Now we will take a closer look at web application firewalls and give you a definition, explain their benefits, and the different types available.
What is a Web Application Firewall (WAF)?
The WAF or web application firewall is a tool that helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It can be cross-site scripting (XSS), cross-site spoofing, file inclusion, and SQL injections. WAF is a Layer 7 protection (in the OSI model) and is not designed to protect against all attacks. Instead, it is an attack mitigation method typically part of a set of tools that create a holistic defense against a range of attack vectors.
How Does Web Application Firewall Work?
WAF works using a set of rules, often called policies. These policies aim to protect against application vulnerabilities by filtering malicious traffic. The value of a WAF comes from the speed and ease of implementing policy modifications, which allows you to respond more quickly to different attack directions. So you can modify WAF policies during a DDoS attack and quickly implement rate limiting. In addition, it prevents incoming attacks by analyzing incoming network traffic to the web server/web application according to rules and policies. According to recommendations, WAF should be able to detect types of attacks on the OWASP list:
- SQL injection
- Cross-site scripting
- Command injection
- Local file inclusion
- Enabling remote file
- Buffer overflow, brute force attacks
- Parameter tampering and file upload vulnerabilities.
- Poisoning
- Session hijacking
- Sensitive data leakage
- Improper server configuration
- Commonly known vulnerabilities
- Manipulation of forms and hidden fields
- Cookie session
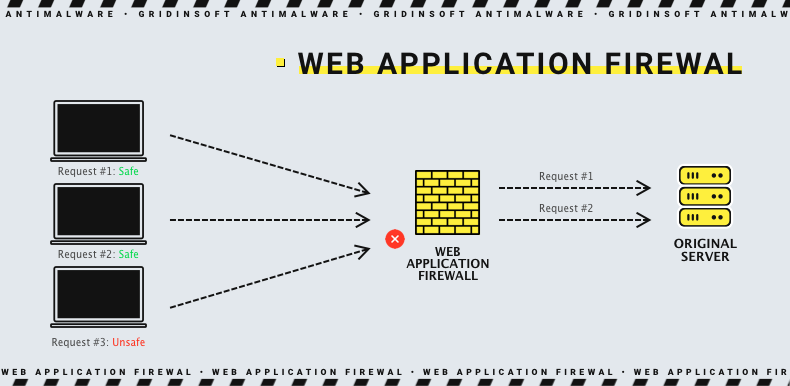
When a WAF is deploying in front of a web application, a screen is placed between the web application and the Internet, meaning the WAF acts as a reverse proxy server, protecting the application from unwanted requests before they reach the web application.
WAF deployment options
You can deploy WAF in some ways – it all depends on where your applications are deployed, what services you need, how you want to manage them, and the architectural flexibility and performance level you require. For example, do you want to work it yourself, or do you want to outsource that management? Is it better to have a cloud-based option, or do you want your WAF to be hosted locally? How you want to deploy will help determine which WAF suits you. Below are your choices, each with its advantages and disadvantages:
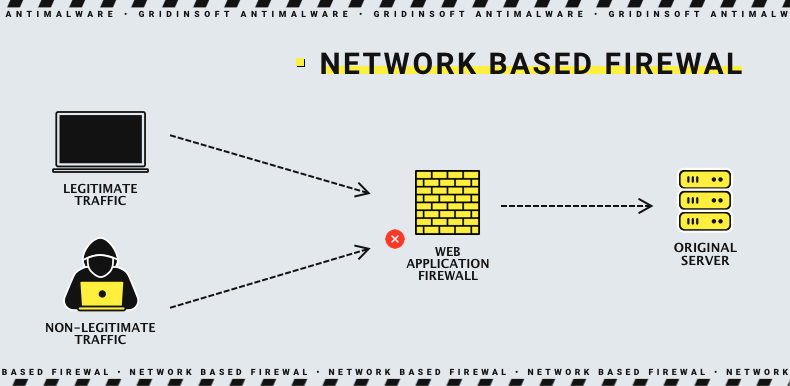
Network-based WAF
Network WAF is a hardware solution installed local network, so it has low latency. The network-based WAF has a WAF engine that handles traffic in proxy mode. All incoming (and outgoing) traffic goes through it and is inspected, and dangerous traffic is blocked. However, this option requires storage and maintenance of physical equipment despite its effectiveness. As a result, it is typically associated with high maintenance costs, making it one of the most expensive deployment options. But its flexibility and ability to control every element makes it attention-worthy.
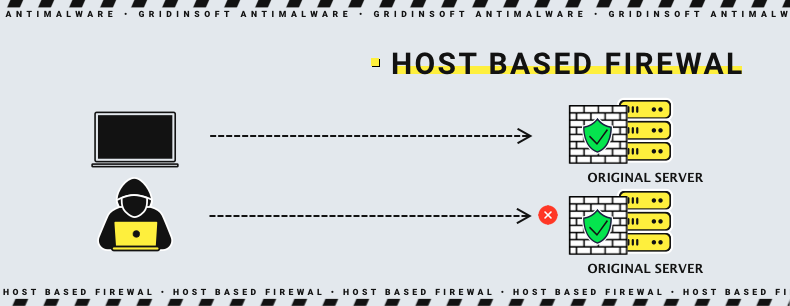
Host-based WAF
Host-based WAF provides protection through software installed on the web server itself. Like the previous option, host-based WAFs are in place and thus minimize latency. However, host-based WAFs consume web server resources to perform their security function because they do not reside on a separate physical device, unlike the previous variant. Thus, host-based WAFs can also be costly because of the need to optimize the web server so that its performance is not degraded by deploying it on the server itself.
Cloud-based WAF
Cloud-based WAFs are the most affordable option and are very easy to implement. Companies that provide this service offer a turnkey installation that is as simple as changing DNS to redirect traffic. In addition, cloud WAFs have minimal upfront costs because the service is subscription-based, and users pay a monthly or annual security fee as a service. Cloud WAF security is continually updated to protect against the latest threats without any action or expense on the user’s part. The only disadvantage of a cloud WAF is that users delegate responsibility to a third party so that some WAF features can be a black box for them.
Types of web application firewalls
As described above, a WAF works according to a set of rules or policies defined by the network administrator. Each WAF policy or practice is designed to address a threat or known vulnerability at the application level. Together, these policies allow malicious traffic to be detected and isolated before it reaches the user or application. There are three types of security models used for Web application firewalls:
Positive Security Model
A positive security model identifies what is allowed and rejects everything else, moving away from the “blocked” end of the spectrum, following the “allow only what I know” methodology. The positive security model only trusts allowed requests or inputs and rejects the rest. In this case, an allowlist is created, permission statements are added to the firewall with packet filtering, and allowed inputs or requests are considered based on it.
Negative Security Model
The negative security model is the exact opposite of the positive security model and assumes that:
- Most web traffic is benign.
- Web traffic that is not benign can be identified.
The negative security model allows all HTTP/S requests by default. Requests are not rejected unless they are identified as hostile. The negative security model is sometimes called the “blacklist” model. This is because you need to blocklist unwanted traffic and define threat signatures and other means of identifying malicious traffic before that traffic can be blocked.
Mixed Security Model
As the name suggests, the mixed security model uses allowlists and blocklists. Since the model combines the advantages of both models, it is the most common. So, most modern firewalls use this model.
Difference Between Blocklist and Allowlist WAFs
The WAF, which operates on a blocklist, protects against known attacks. Let’s compare it to a club bouncer who denies entry to guests who don’t conform to the dress code. The WAF, based on an allowlist, in turn, allows only pre-approved traffic. It’s like a bouncer at an exclusive party who lets in only those on the guest list. Since both options have advantages and disadvantages, many WAFs offer a hybrid security model that implements both.

Why is it essential to use the web application firewall
Protecting corporate data and services is the first and most compelling reason to implement WAF. Thousands of businesses, from minor to giant corporations, make money using the Internet. If this income source is compromised, the company risks being hit hard. Here are the main risks:
Loss of Direct Revenue. Suppose the firm uses an Internet resource for online commerce, which has become unavailable. In this case, customers can not make purchases, and the firm loses a significant amount of money.
Loss of Customer Confidence. A good reputation is essential for a self-respecting company. Many customers pay attention to news about break-ins of specific companies and make a note to themselves so that they do not do business with this company in the future.
Loss of Sensitive Data. Unfortunately, cases where hackers have gained access to sensitive information, are not uncommon. After hacking websites, information such as names, addresses, credit card numbers, medical records, and social security numbers will most likely find their way into the Darknet (and sometimes into the public domain). In addition, private information, trade secrets, and even classified government data are tidbits for hackers. While the mere fact of being hacked is already a nuisance, the fines and disaster recovery/forensic costs can exceed any other financial impact.