Virus and malware threats are constantly evolving and become more sophisticated and more dangerous over time; this makes it extremely difficult to maintain your data’s security. Unless you’re adequately protected, you risk to become a victim of the latest computer viruses and malware attacks. In addition, cybercriminals are relentless. They will stop at nothing to access your computer or phone and steal your most valuable data, including bank information, personal photos, and sensitive identification information. This is why it’s important to have an effective antivirus installed on your computer, mobile device, or Android, iOS, or Windows device.
1. Ransomware threats
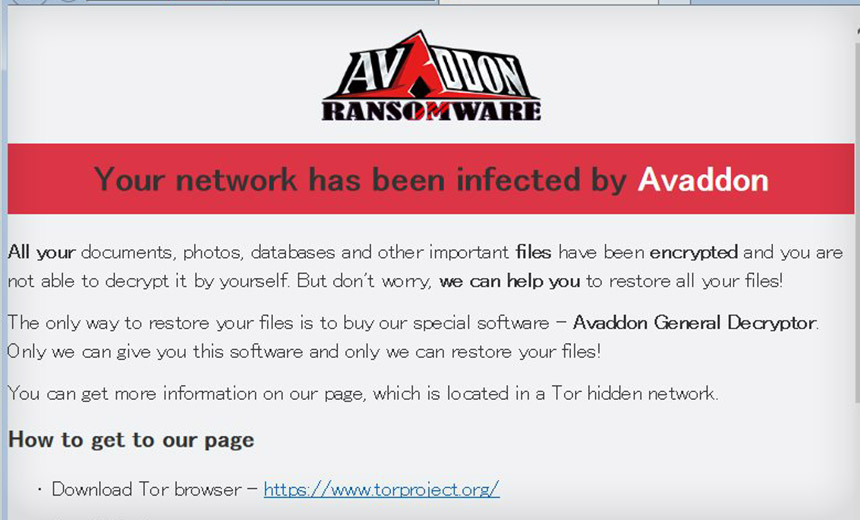
Ransomware is the worst threat, which is unlikely to be avoided if an attack does occur. It encrypts files using unique cryptographic algorithms that are almost impossible to decrypt. Ransomware targets both single users and corporations. Ransoms range from a hundred dollars (for users) to $50 million (the enormous ransom ever paid by Acer Corporation in March 2021). There is also the practice of blackmail by disclosure, called triple extortion. Another widely used method is spamming emails. A file attached to an email – most often an MS Office document – contains a malicious macro. The macro in an office suite was initially used to increase the interactivity of the paper. Still, the large number of vulnerabilities in its mechanism makes it an excellent carrier of malware.
2. New Disguises for Malware threats
Criminals use news stories and global events to target people with malware. During the COVID-19 outbreak, scammers used the confusion and virus theme to target victims with malware. By disguising emails as important information, they trick victims into clicking a link that pushes malicious software onto their devices. In 2022, Russia-Ukraine war became a disguise for such mailing. Who knows what may appear in the future?
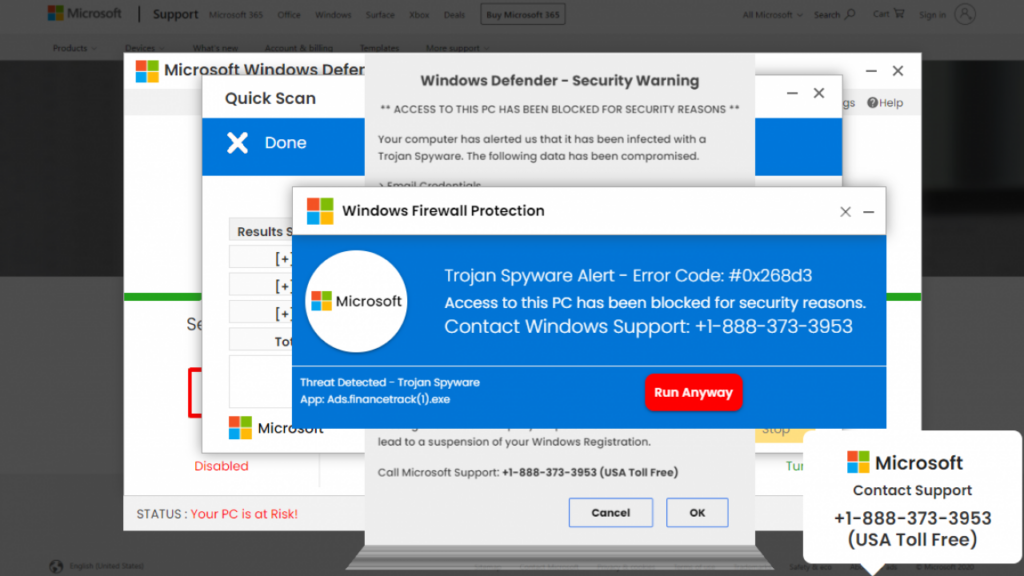
With time, malware authors have developed hundreds of methods to make their malware appear “new again” to evade security measures. The old methods of disguising the malware are not going anywhere, and scary banners like PORNOGRAPHIC VIRUS ALERT FROM MICROSOFT or URGENT WINDOWS UPDATE have been used for years. It should also be noted that the old disguise also fits the new infestation, so do not assume that the old only mates with the old.
3. Fleeceware
Fleeceware continues to charge users significant amounts of money despite users deleting the apps. Recent studies have documented that over 600 million Android users have downloaded “Fleeceware” on their devices in the past few years. Fleeceware is not a significant security threat to a user’s device or data. However, it is still common, and it’s a questionable practice by app developers who want to take advantage of unsuspecting users.
4. IoT Device Attacks
IoT is a large number of Internet-connected devices. This is the process of transferring data between different devices. This feature facilitates organizations’ growth and even serves customers. Organizations that want to safeguard the transmission of their data and the device through which it occurs must understand the importance of IoT cybersecurity, as most attacks are directed at this. The number of attacks on IoT devices is increasing annually, which should be considered, and a solution developed to counter this.

Additionally, many IoT devices need more storage capacity to implement proper security measures. These devices often have readily available data, including passwords and usernames, which hackers can use to access user accounts and steal sensitive information, such as banking information. Hackers can also utilize internet-based cameras and microphones to observe and communicate with people, including children, via intelligent baby monitors.
5. Social Engineering
Social engineering is one of the famous methods through which fraudsters deceive the user, manipulate him, and instill fear and urgency. Once the victim is emotionally invested, the fraudsters distort her perception. Therefore, any human error is a vulnerability that facilitates social engineering.
In this case, the hacker will begin by contacting a company or service provider and pretending to be a specific individual. Next, they’ll inquire about the victim’s story and deceive the customer support staff into divulging sensitive information. Then, they’ll utilize that information to access a person’s account and data, including payment information. This isn’t malware per se, but social engineering is a concerning trend, as it doesn’t require hackers to know coding or malware creation. Instead, all the attacker needs to do is be convincing and allow human error and complacency to benefit them with the information they need.
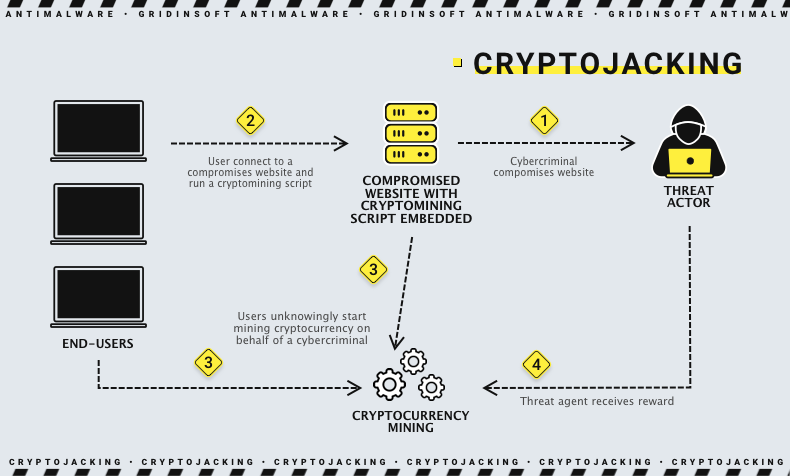
6. Cryptojacking
Hackers try to sneak cryptojacking malware onto a computer or mobile device by hiding it inside malicious files. This malware uses a person’s resources to “mine” cryptocurrencies like Bitcoin: it slows down the device’s performance, which prevents them from mining new coins. Because of the rising value of cryptocurrencies — specifically Bitcoin — the threat of cryptojacking malware hasn’t decreased. In January 2018, Bitcoin, valued at $39,200, was recorded. Since many cryptojacking malware attacks are profitable, cybercriminals will continue to use this malware to make significant money.
7. Artificial Intelligence (AI) Attacks
As more tools become available to developers who want to program AI scripts and software, hackers will have access to this same technology, allowing them to conduct devastating cyberattacks. Cybersecurity companies employ artificial intelligence and machine learning algorithms to help combat virus and malware threats. However, these technologies can also be used to hack devices and networks on a massive scale. In addition, cyberattacks are often costly to cybercriminals in terms of time and resources. With the increased adoption of artificial intelligence and machine learning, hackers will likely develop highly advanced and destructive AI-based malware in 2023 and beyond.
Defending Yourself from Cybercrime
Your private information, sensitive data, sentimental photos, and private messages — what’s the value to you? They’re irreplaceable. How are you combating new virus and malware threats? Many people only have essential antivirus software and possibly other cybersecurity tools to safeguard themselves. However, the truth is that most antivirus programs do not provide complete protection against new virus and malware threats; you are still susceptible to the latest threats. To ensure your device and all your data are protected, you must utilize the best antivirus software for your PC, Mac, Android, and iOS device.