Let’s have a look at the bad boys of this year. During 2022, the factions have been forming and forming again, but one thing is sure – they continue to exist. Despite all efforts, the problem of extortion programs continues to grow: a recent report by IS-Zscaler recorded an 80% increase in attacks by extortion programs compared to last year. Major trends included double extortion, supply chain attacks, extortion as a service (Ransomware-as-a-Service, RaaS) , group rebranding, and geopolitically motivated attacks.
This year, for example, a well-known group of ransomware called Conti broke up, but its members only moved forward, forming new gangs. Which groups should we beware of in 2023? We will consider some of the most important players.
LockBit
LockBit has been in existence since 2019 and operates under the RaaS model. According to GuidePoint Security, the largest group, which accounts for more than 4 out of 10 victims of ransomware programs. This group is believed to be linked to Russia, however, its creators deny any ties and claim their multi-nationality. LockBit 3.0 update was released in June and has already spread to 41 countries, according to Intel 471. The main goals are professional services, consulting and production, consumer and industrial goods, and real estate. LockBit also launched its Bug Bounty program, offering up to $1 million. This reward is offered for detecting vulnerabilities in their malware, leak sites, Tor network, or messaging service.
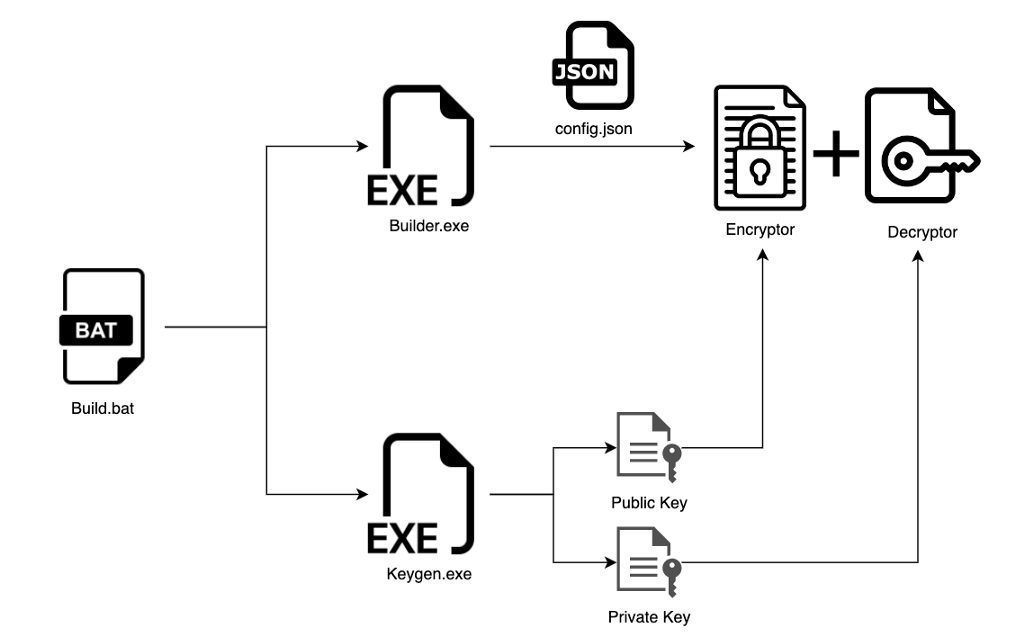
Black Basta
The Black Basta group first appeared this spring and, in the first two weeks, attacked at least 20 companies. The gang is supposed to consist of former members of Conti and REvil. Black Basta is campaigning using the malware QakBot, and a bank trojan used to steal victims’ financial data, including browser information, keystrokes, and credentials.
This ransomware is believed to have hit about 50 organizations in the United States over the last quarter, including the American Dental Association (ADA) and the Canadian food retailer Sobeys. More than half of the group’s targets were from the United States.
Hive
Hive, the third-most active group of ransomware this year, focuses on the industrial sector and health, energy, and agriculture organizations. According to the FBI, the hackers attacked 1,300 companies worldwide, especially in the health sector, and received about $100 million in ransom. It was reported that the United States Department of Homeland Security was responsible for the attack.
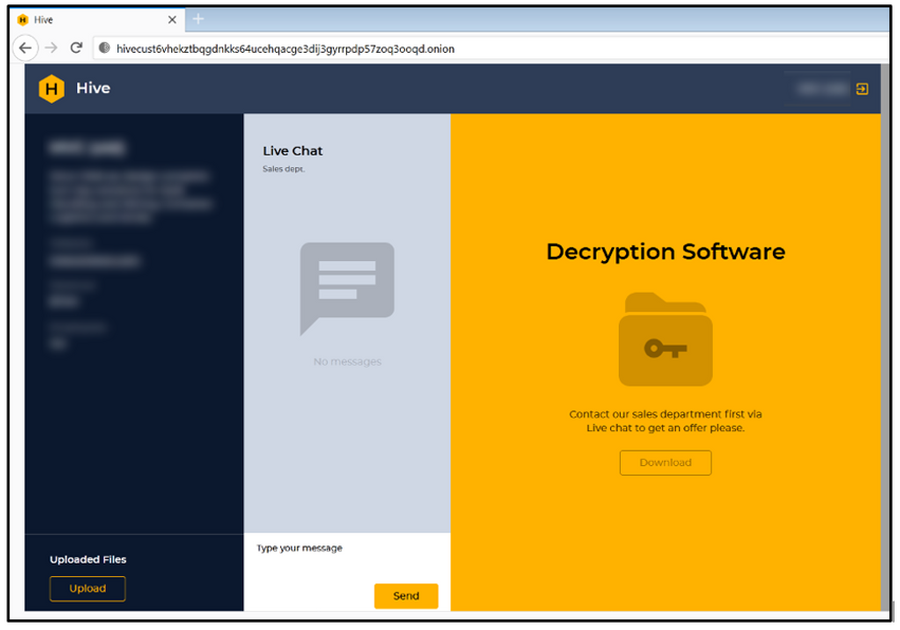
In recent weeks, the group claimed responsibility for the attack on India’s energy company Tata Power, by posting the company’s data online and at several colleges in the United States. Experts believe Hive cooperates with other ransomware groups and has its own customer support and sales departments. In addition, the group also engages in triple extortion.
ALPHV/BlackCat
ALPHV/BlackCat is one of the most complex and flexible families of extortion software based on the Rust programming language, which has existed for about a year. The band is believed to be composed of former REvil gang members and is associated with BlackMatter (DarkSide). The group also runs a RaaS model, exploiting known vulnerabilities or unprotected credentials and then launching DDoS attacks to force the victim to pay the ransom. Additionally, BlackCat hackers disclose stolen data through their own search system.
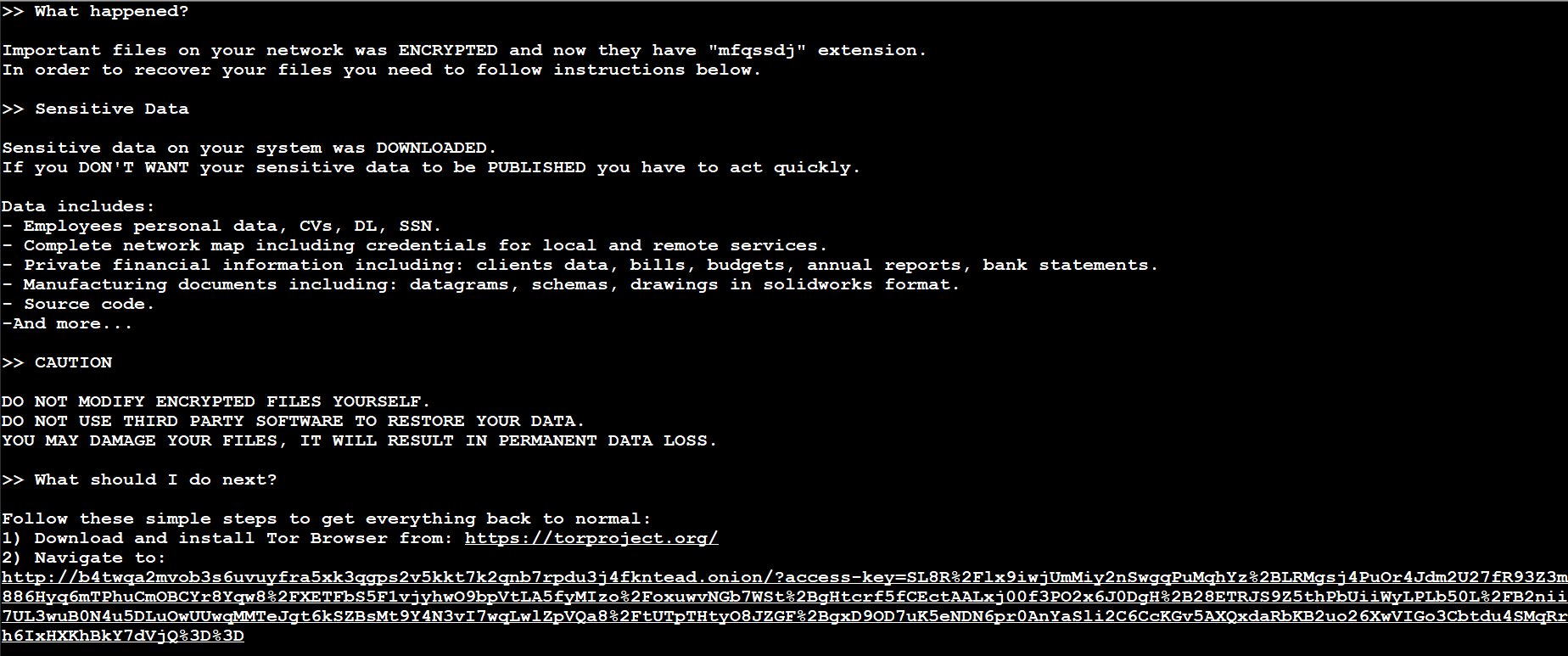
The group’s objectives are to provide critical infrastructure, including airports, fuel pipeline operators and refineries, and the United States Department of Defense. Ransom claims amount to millions; even when the victim pays, the group does not always provide the promised decryption tools.
BianLian
A relatively new player who targets organizations in Australia, North America, and the UK. The group quickly launches new Management and Control Servers (C&C) into the network, indicating that hackers plan to increase activity significantly.
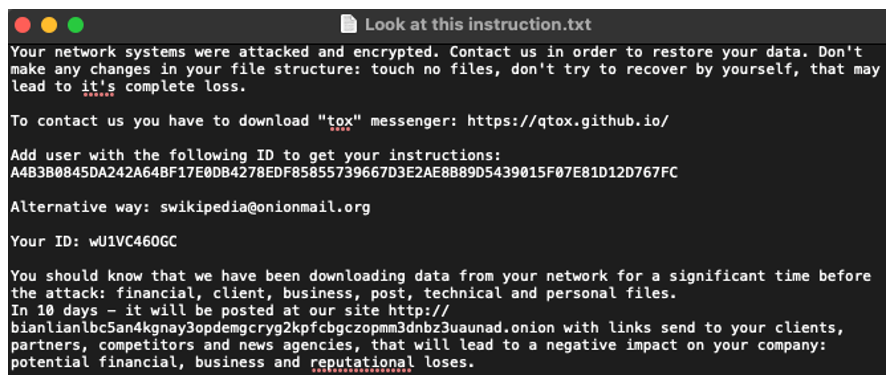
Like many other ransomware programs, BianLian is based on Go, which gives it high flexibility and cross-platform. However, according to Redacted, the group comprises relatively inexperienced cybercriminals who must be equipped with the practical business aspects of extortion programs and related logistics. In addition, the group’s wide range of victims indicates that it is motivated by money rather than political
ideas.
Other New Groups
The world of ransomware is constantly changing, and several groups have been renamed: DarkSide is now called BlackMatter, DoppelPaymer has become Grief, and Rook has been renamed to Pandora. In addition, over the past year, new groups have appeared – Mindware, Cheers, RansomHouse, and DarkAngels. We will probably hear about them next year.
How to protect yourself
Your defenses should include safeguards for each of those phases:
- Reduce the attack surface by making internal apps inaccessible to the Internet and decreasing the number of vulnerable elements.
- Prevent compromise by employing a cloud-native proxy architecture that inspects all traffic inline and at scale, enforcing consistent security policies.
- Prevent lateral movement by connecting users directly to applications rather than the network. This would reduce the attack surface and contain threats using deception and workload segregation.
- Prevent data loss by inspecting all Internet-bound traffic, including encrypted channels, to prevent data theft.




