Malware operators and other hackers are increasingly abusing Google Ads to distribute malware to users who are looking for popular software. So, you can encounter malicious ads when searching for Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird, and Brave.
Let me remind you that we also wrote that Fraudsters Are Running a Malicious Advertising Campaign through Google Search.
Specialists from Trend Micro and Guardio Labs described the problem in detail. According to them, hackers are increasingly using typesquatting, cloning the official websites of the above programs and manufacturers, and then distributing trojanized versions of software through them, which users eventually download.
Among the malware delivered in this way, there are versions of the Raccoon stealer, a custom version of the Vidar stealer, as well as the IcedID malware loader. For example, we recently wrote about one of these campaigns, in which attackers distributed miners and the RedLine infostealer using fake MSI Afterburner utility sites.
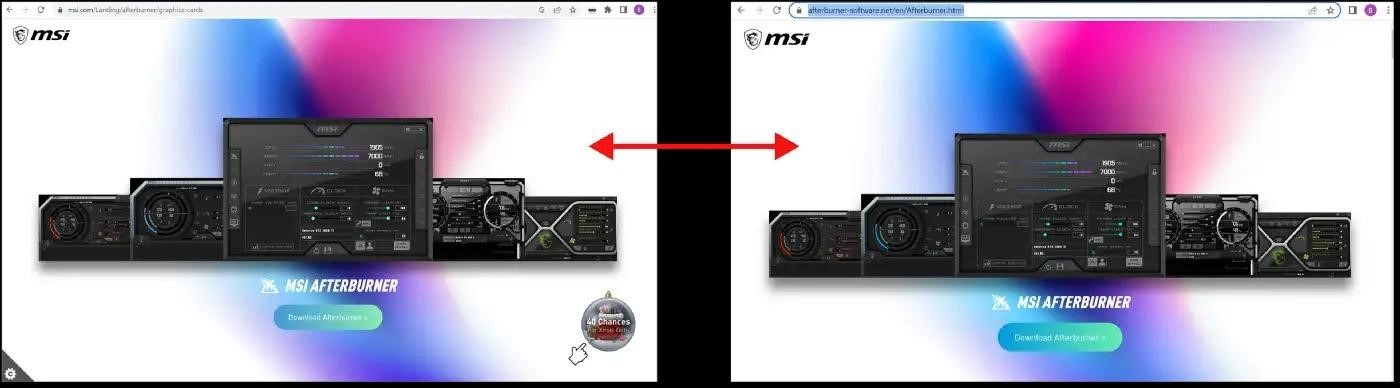
Fake and real site
However, until recently, it was not clear exactly how users get to such malicious sites. It turned out that the key is in the abuse of advertising in Google.
Trend Micro and Guardio Labs experts say that Google, of course, has protective mechanisms for such a case, but attackers have learned how to bypass them. The thing is, if Google detects that the landing page behind the ad is malicious, the campaign will be immediately blocked and the ad removed.
Therefore, attackers act cautiously: first, users who click on ads are redirected to an irrelevant but safe site, also prepared by hackers. Only from there will the victim be redirected directly to a malicious resource masquerading as the official website of some kind of software.
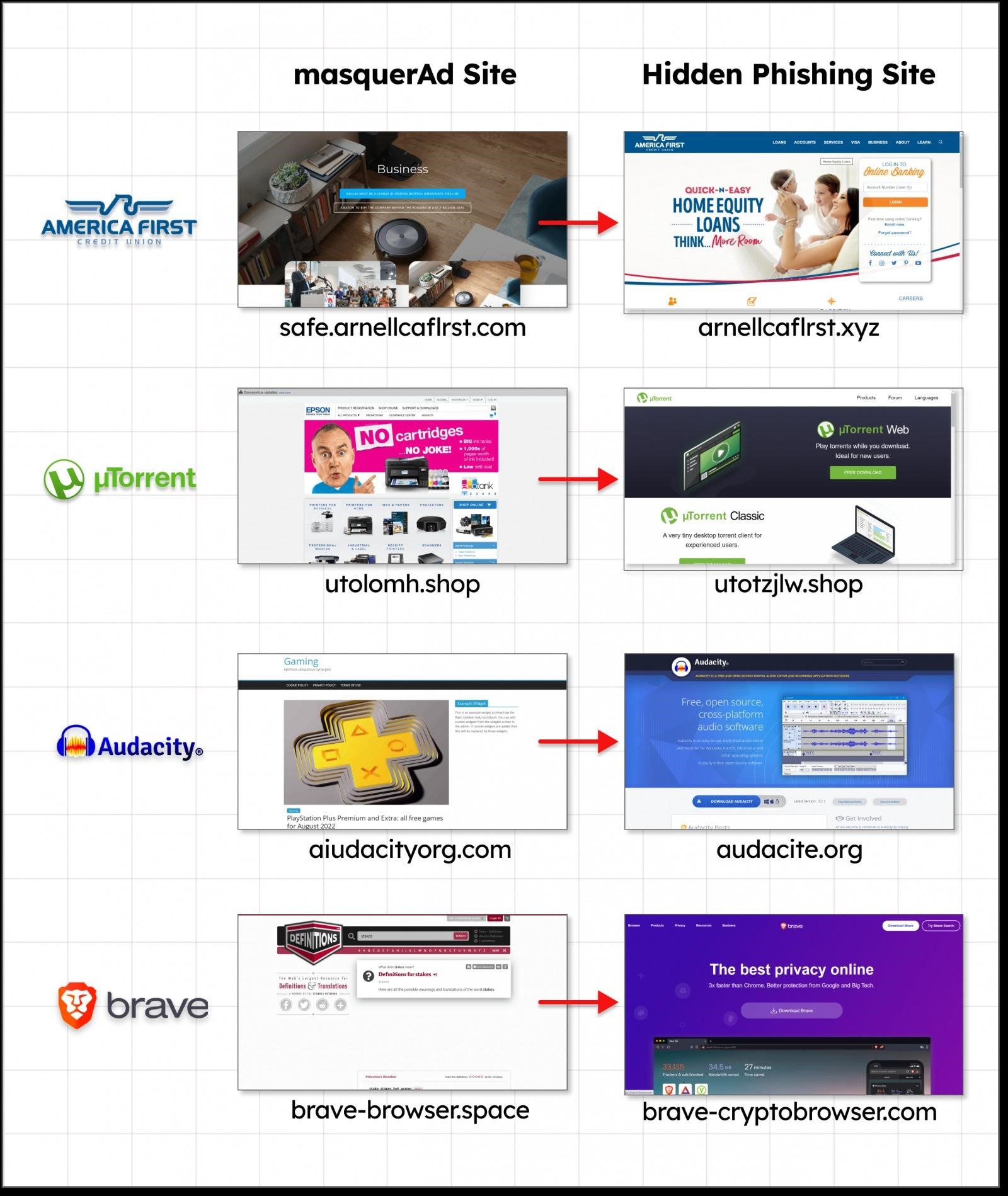
How redirects work
As for payloads, they are usually in ZIP or MSI formats and are downloaded from reputable file sharing and code hosting services, including GitHub, Dropbox, or CDN Discord. Due to this, the anti-virus programs running on the victim’s computer are unlikely to object to such downloads.
Guardio Labs experts say that during one campaign they observed in November of this year, attackers distributed a trojanized version of Grammarly to users, which contained the Raccoon stealer. At the same time, the malware was “bundled” with legitimate software, that is, the user received the program that he was looking for, and the malware was installed “in the appendage”, automatically.
Guardio Labs, which has named these attacks MasquerAds, attributes most of this malicious activity to the Vermux group, noting that the hackers “abuse a lot of brands and continue to evolve.” According to them, Vermux mainly attacks users in Canada and the United States, using fake sites to distribute malicious versions of AnyDesk and MSI Afterburner infected with cryptocurrency miners and the Vidar stealer.
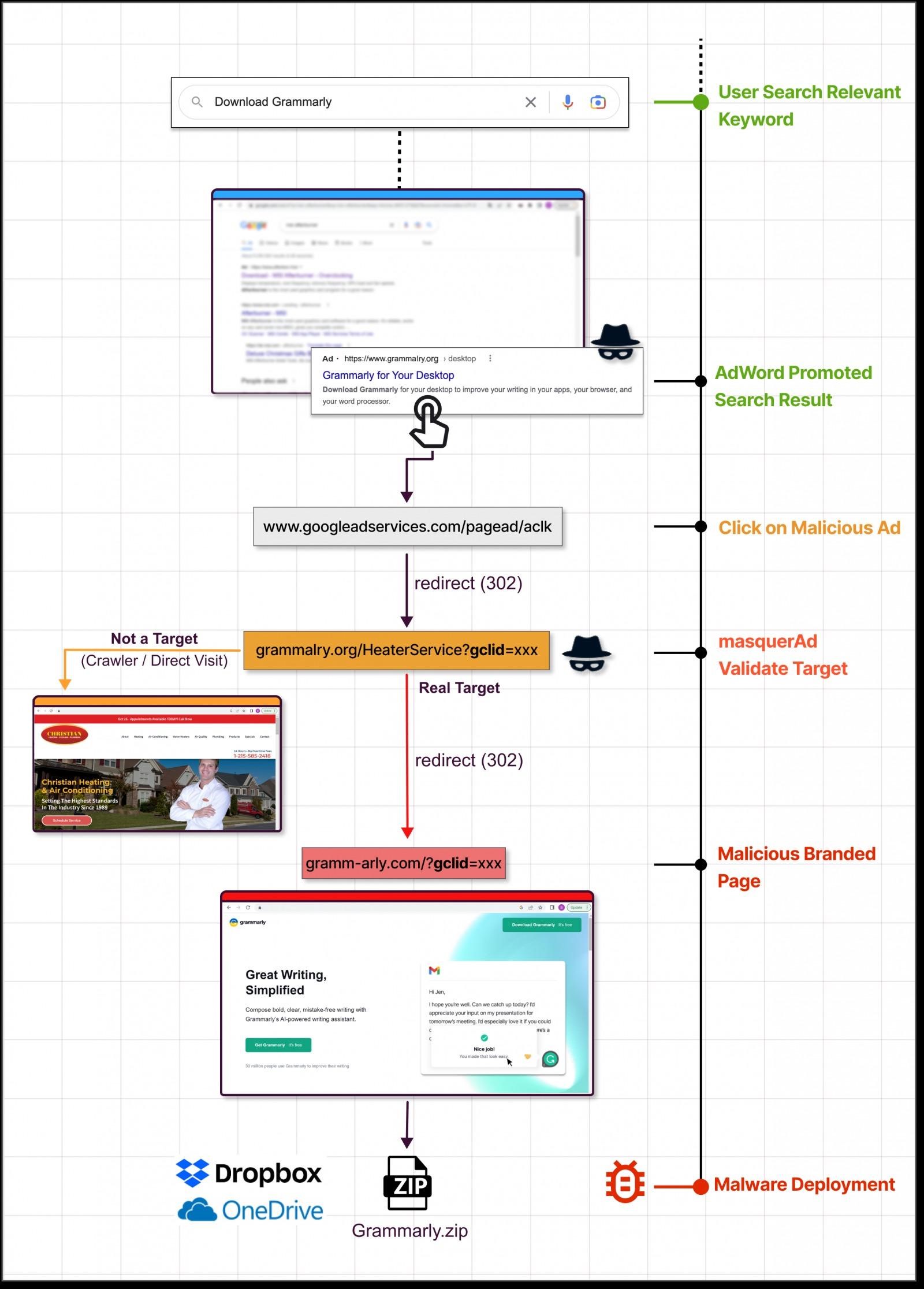
Attack scheme
Interestingly, activity of hackers, which experts have now described in detail, recently forced the FBI to publish a warning and recommendation on the use of ad blockers (so as not to see potentially dangerous ads in search engines at all).




