The Dutch National Police, together with information security specialists from RespondersNU, tricked the operators of the DeadBolt encryptor into giving them 155 keys to decrypt data. For this, the experts had to fake payments of ransoms.
Let me remind you that the DeadBolt ransomware has been active since the beginning of 2022 and attacks NAS from various manufacturers. Basically, the ransomware “specializes” on Qnap devices, but attacks on ASUSTOR NAS have also been detected.
According to the Dutch police, ransomware attacks have already compromised over 20,000 devices worldwide and at least 1,000 in the Netherlands. Attackers demand 0.03 bitcoin (about $575) from the owners of the hacked NAS to decrypt the data.
Experts say that after paying the ransom, DeadBolt sends a bitcoin transaction to the same address that is used to pay the ransom. As a result, the transaction contains the key for decrypting the data for the victim, which can be found in OP_RETURN.
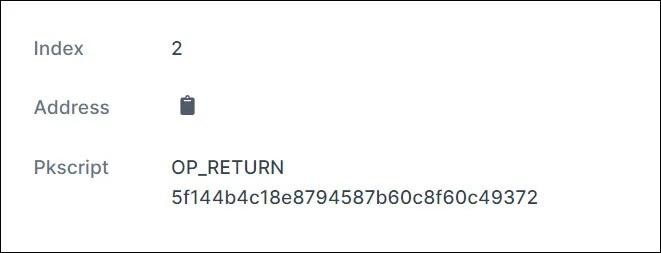
When the victim provides this key to the malware, it is converted to a SHA256 hash, compared with the SHA256 hash of the victim’s decryption key and the SHA256 hash of the DeadBolt master decryption key. If the decryption key matches one of the SHA256 hashes, the encrypted files on the affected NAS will be decrypted.
Bleeping Computer found out the details of this operation from an RespondersNU information security expert Rickey Gevers. He confirmed that the police tricked the ransomware into creating decryption keys and canceled his transactions before they were included in the block.
The fact is that victims have sent the decryption key immediately without waiting for confirmation of the legitimacy of the transaction. This allowed law enforcement and experts to fake low-fee ransom payments when the blockchain was heavily congested. Since the blockchain needed time to confirm transactions, the police completed the transactions, got the keys, and immediately canceled the payments.

Unfortunately, the ransomware operators have figured out exactly how they were scammed. This is why the hackers behind DeadBold require double confirmation before handing over keys to decrypt data to victims.
RespondersNU, in cooperation with the Dutch police and Europol, has created a special site where DeadBolt victims who have not contacted the police or have not been identified can check if, among the keys fraudulently obtained from the attackers, there is a key for their affected device.


