Intruders are developing more and more methods to get what they want. Social engineering is one of the most common methods through which fraudsters manage to deceive the user, manipulate him, and instill his fear and urgency. Once the victim is emotional, the fraudsters begin to cloud her judgment. Any human error is a vulnerability that makes social engineering work. This article will present the top most common types of social engineering. Along with it, you’ll see the guidance on how to avoid becoming a victim of such attacks.
1. Phishing attacks
According to FBI statistics, phishing is the most common form of social engineering. This is when fraudsters use any form of communication, usually email, to get personal information. Phishing typically exploits the trust of companies’ employees or family members. These attacks are ten times more successful than any other form of social engineering. The fraudster may send you an email stating that it is from your bank – that’s what is called banking phishing. Crooks claim that your account password has been compromised, and requires that you immediately click the link or scan the QR code. Then you enter your personal information, which is immediately passed on to the fraudster. If you doubt the legitimacy of the site,you can check whether the site is secure by checking that their URL uses HTTPS instead of HTTP.
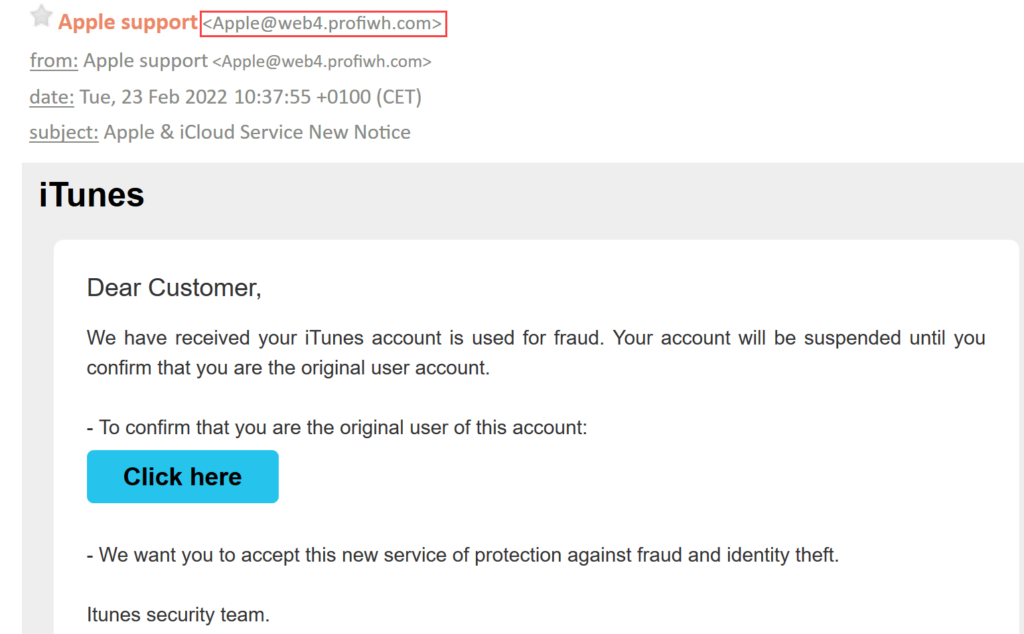
2. Whaling
The term whaling refers to an attack that targets a specific celebrity, executive, or government employee. Typically, these individuals are targeted by a phishing scam. When it comes to scams involving victims of whaling attacks, financial incentives or access to valuable data are typically big deals for criminals. They consider these victims of big fish – because of the large monetary and data payoff they offer – perfect targets.
Scammers seek compromising photos of celebrities they can use to extortionate high ransoms. Criminals use fake emails to fool senior employees into thinking they come from the organization. The messages detail information about a colleague and claim the creator is afraid to report the situation to a supervisor. They share their evidence as a spreadsheet, PDF, or slide deck.
Victims clicking the provided link are redirected to a malicious website that tells them to visit the link again. If they try to open the attached file, malware resides on their computer and gains access to their network.
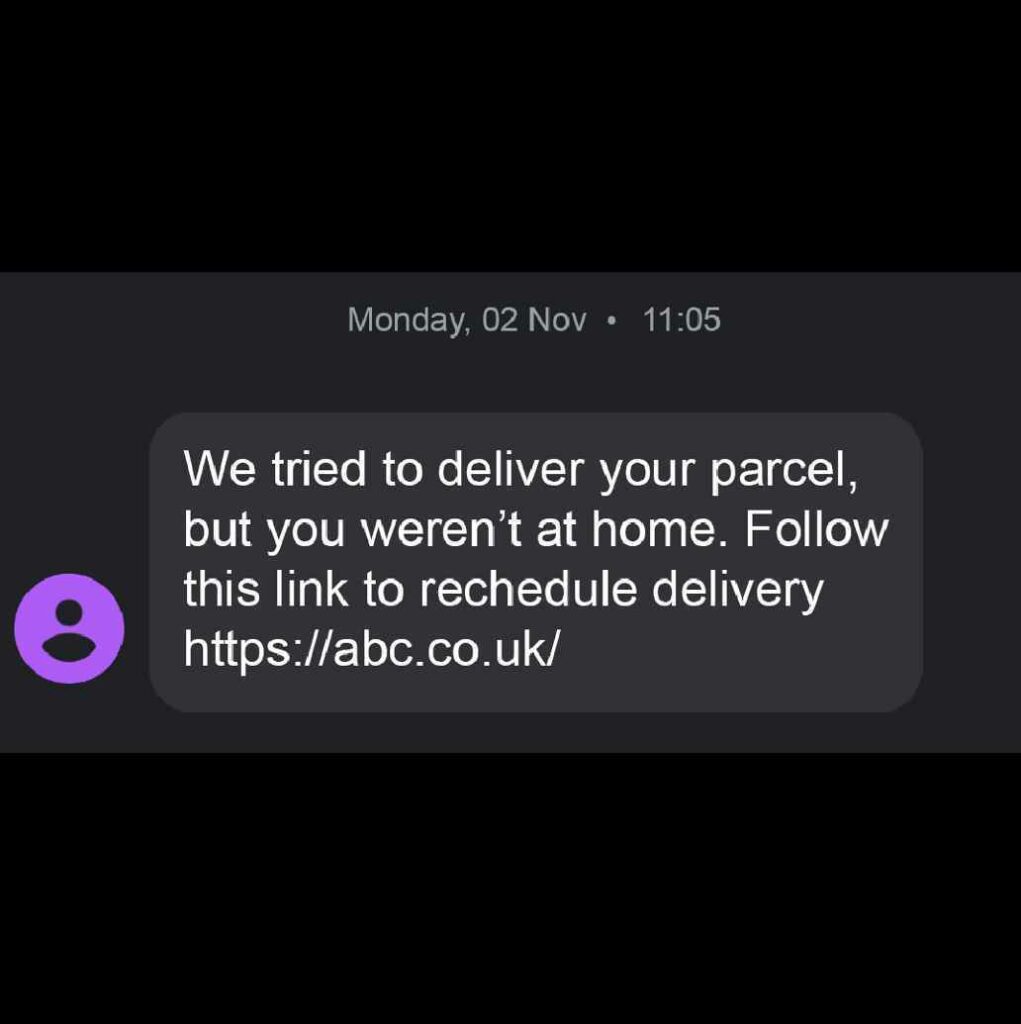
3. Smishing (SMS phishing) and vishing (voice phishing)
Under this term, people refer to phishing via text messages. Crooks buy the branded number from a cellular operator and use it to send out messages containing malicious links.
Phone phishing is called vishing, and it’s the same as phishing done over the phone. Vishing is a scam that affects businesses more than any other type of organization. In this scam, an impostor will contact the front desk, human resources, IT or a company’s customer service. They will lie about needing personal information about an employee and claim to have information on mortgages or executive assistants.
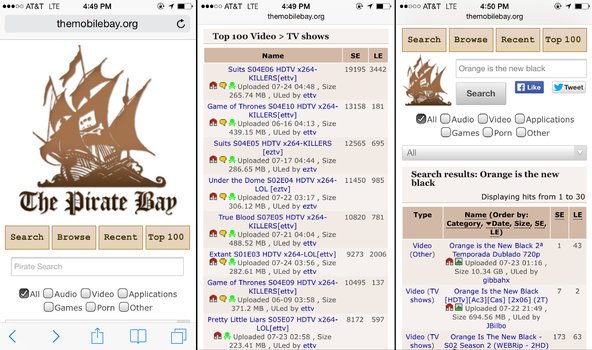
4. Baiting
It’s a kind of social engineering that’s a lot like phishing. The only difference is that the attackers lure their victim with a product or an object during the attack. This happens as follows: the attacker offers the victim a free download of a popular movie or a new game. With such a disguise, the criminal installs malware into the victim’s system. Attackers can also use the opportunity to spread malware on the victim’s device. If we talk about the physical distribution of malware, here, the crooks do it through a USB drive with a tempting label. After the curious employee sticks this USB into his device, he infects his PC or other devices.
5. Pretexting
Whenever someone creates a false ID or abuses their current position, this is closely related to the data leak from within. Because people trust their work, these scammers trick victims into sharing personal information. They build this trust by using titles and gaining access to victims through their legitimacy. Because of the victim’s over-reliance on the authorities, they are unlikely to question suspicious activities or put pressure on impostors.
6. Watering hole attacks
This attack works by identifying the website the victim visits most. In this case, the victim may be not only a single user but an entire sector, such as government or health care, where the same sources of use are used during work. Here, intruders seek vulnerabilities in cyber security, through which they can infiltrate the system and distribute their malware. Although the case is small, the fraudsters continue to infect users’ devices through already infected sites.
How to prevent Social Engineering Attacks
The following tips will help you warn yourself against attacks. But this is only possible if you use it in practice.
- Carefully check emails, including names, addresses, and copy.
- Do not believe everything you see in the letter, especially if it causes you violent emotions.
- Verify the identity of the sender before providing him with any information.
- Do not pay ransom to strangers. Instead, it is best to contact law enforcement.
- Use the password manager.
- Set two-factor authentication, which will double-check who is trying to log in to your account.
- Install reliable GridinSoft Anti-Malware Protection, which will protect you from malware.