DNS Cache Poisoning is a pretty old attack type in which a malicious actor redirects a victim’s traffic to a harmful site instead of a legitimate IP address. It is done by replacing cached IP addresses on the DNS server. Attackers also use the method of “poisoning” the DNS cache to steal credentials or sensitive information. But how dangerous is it? And how can we protect against such attacks? Let’s find out.
DNS Cache Poisoning Overview
DNS cache poisoning is a type of attack where hackers impersonate another device, client, or user. To do this, hackers alter the cached IP addresses stored locally on the device. As a result, when a user tries to visit a website, they end up on a fake site that the modified DNS cache returns, instead of the legitimate one they intended to reach. This trick is hard to notice on the final stage, as fake sites are typically designed to look like the real ones. The result of a successful cache poisoning is similar to a “man-in-the-middle” attack: it allows an attacker to intercept data that goes from the user machine to a website.
By poisoning a DNS server, attackers can redirect all your traffic to their own servers. For instance, if you type “amazon.com,” a poisoned DNS server can redirect you to a fake version of Amazon. Attackers can poison the DNS cache by filling it with false data. They do this by making a request to the DNS resolver and then spoofing the response when the resolver queries the name server. When the DNS resolver receives a fake response it accepts and caches the data. This is because cached info is considered trustworthy, and it is hard to prove this wrong without additional actions. The reason hides in the very idea of DNS as a system: it appeared back in the days when no one thought of such an attack vector.
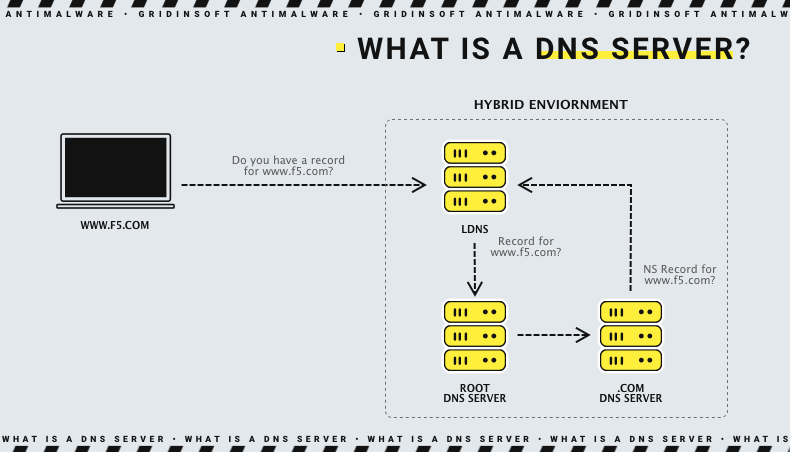
DNS Cache Poisoning Mechanism
Since IP addresses don’t change often (if at all), a computer saves the association between an IP address and a URL. For example, www.gridinsoft.com will get the association to the IP address 104.26.15.79. If an attacker can get the targeted system to receive falsified information from DNS, the client will send data to a fake IP address. In the best-case scenario, this results in a denial of service. In the worst case, the attacker can intercept traffic, leading to severe consequences.
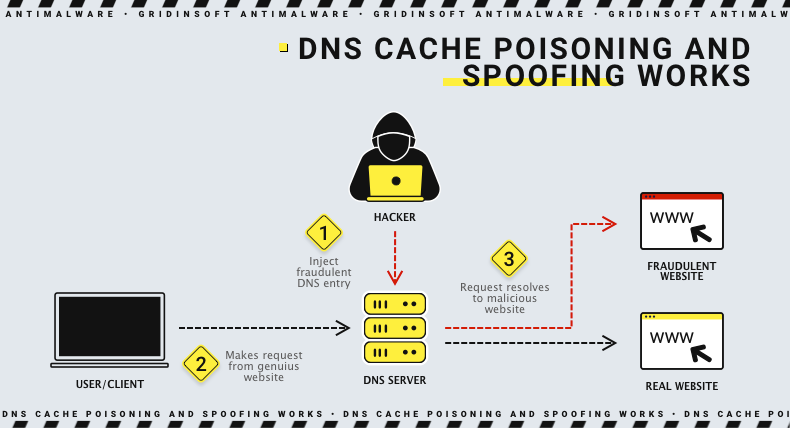
A successful attack expectedly makes the user think they are visiting a legit site. Therefore, the user doubtlessly enters confidential account information, which immediately goes to the attacker. A “successful” attack means the user doesn’t notice the deception and calmly enters their login and password. This hands over their credentials to the attacker.
As a result of such an attack, an attacker can redirect a user to fake or malicious websites, leading to malware deployment. For example, a fake online banking site might prompt the user to update an application. Instead of the legitimate application, the user receives a malicious file. Additionally, a compromised website can initiate malware downloading.
On the other hand, attackers can also disrupt legitimate software updates by poisoning the DNS cache. For example, an attacker could block updates to antivirus software signature databases. Besides DNS cache poisoning, there is also the direct hacking of DNS servers, which I covered in a separate article.
DNS Cache Poisoning Application
Reading through technical details of the cache poisoning makes it clear that using such a complicated technique is not about massive attacks. The majority of DNS cache poisoning attacks happen in targeted cyberattacks, particularly on corporations. Since the attack supposes localized changes, it may be harder to detect proactively, especially without special software.
By altering DNS cache on a selection of corporate workstations, hackers can gather login credentials to pretty much any web resource. The ability to select which site is spoofed in a poisoning attack once again makes it harder to detect, and also prevents login data from other sites from flooding the resulting log. In the hands of a skilled adversary, DNS cache poisoning may be an outstandingly effective and dangerous tool.
DNS Cache Poisoning and Censorship
Some governments have intentionally poisoned DNS caches in their countries to block access to certain websites or web resources. For example, the Great Firewall of China uses DNS filtering and fake responses for geoblocking, censorship, and restricting access to specific websites. Additionally, some internet service providers (ISPs) use DNS interception to display advertisements or block access to illegal websites.
Malware in Cache Poisoning Attacks
Technical execution aside, there is one question remaining: how can cybercriminals do this? Getting to the system files, and DNS cache in particular, requires accessing the environment remotely. There are several malware types that can provide such access, namely backdoors and remote access trojans. Following their injection into the network, hackers can control pretty much any element of the system, both through commands and direct access.
As DNS cache poisoning attacks are pretty rare and require thorough planning and targeting, the corresponding actions are often embedded into the malware sample. In addition to this, malware may be able to undo these changes, to cover the tracks after the successful attack.
Preventing DNS Poisoning Attacks
The best way to prevent DNS resolver cache poisoning is to implement secure cryptographic and authentication methods. Replacing DNS globally with DNSSEC (Domain Name System Security Extensions) would address this issue, as DNSSEC creates a unique cryptographic signature stored with the DNS records. This signature is then used by the DNS resolver to verify the authenticity of the response and record. Additionally, this scheme helps establish a trusted chain from the top-level domain (TLD) to the authoritative domain zone, ensuring the security of DNS name resolution.