Fraudsters are seen to exploit a feature of Twitter publications, misleading users and endangering digital assets. This deceptive strategy hinges on Twitter’s URL structure, which allows hackers to lure folks into various scams. Primarily, such campaigns are used to promote various cryptocurrency scams.
Vulnerability in Twitter In-Post Links
The exploit involves altering the account name in a tweet’s URL to masquerade as high-profile accounts, luring users to fraudulent content. This technique has seen increasing use in recent weeks, with scammers targeting prominent crypto-related Twitter accounts with massive followings, such as Binance (11 million followers), the Ethereum Foundation (3 million), zkSync (1.3 million), and Chainlink (1 million). Users clicking these modified URLs are redirected to posts promoting crypto scams rather than the expected legitimate content. Such scams range from false crypto giveaways to deceptive websites designed to drain cryptocurrency wallets.
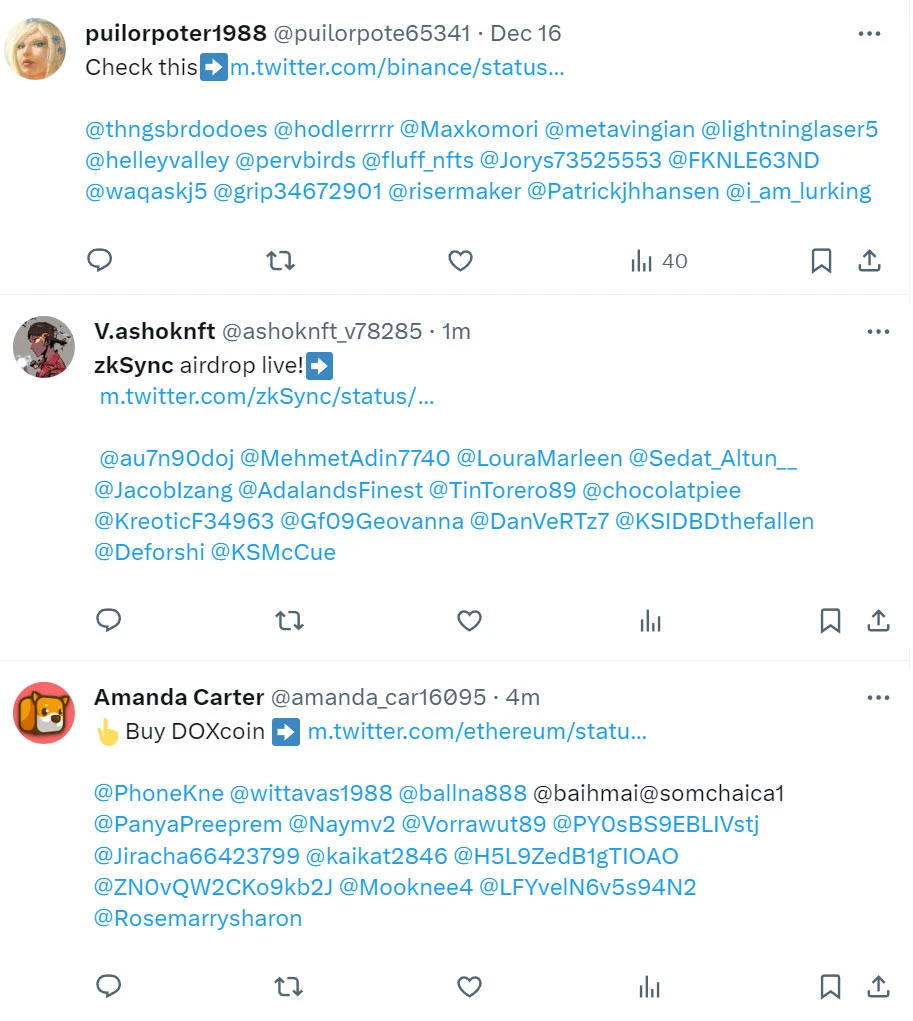
The scam tweets often appear legitimate, particularly on mobile devices, where the Twitter app lacks an address bar, masking the URL discrepancy. This lack of visibility makes it challenging for users to discern the authenticity of the tweet, especially when scammers create accounts with names mimicking legitimate organizations.
What are cryptocurrency scams?
Cryptocurrency scams are fraudulent schemes involving digital currencies like Bitcoin or Ether. These scams exploit the complexity and novelty of cryptocurrencies to deceive users. Tactics include fake giveaways, impersonating legitimate accounts, and promoting bogus investment opportunities with unrealistic returns.
Scammers often use social media, phishing emails, and fake websites to lure victims. They promise high returns, use celebrity endorsements, or offer exclusive investment opportunities, only to steal funds or personal information.
It’s just the beginning
This incident is part of a broader trend of crypto-related scams proliferating on social media platforms, leveraging legitimate features for malicious purposes. These scams not only pose a threat to individual users but also to the reputation of the organizations impersonated. Victims face substantial financial losses, with scammers draining their cryptocurrency wallets, leaving them bereft of their digital assets. Additionally, the psychological toll on victims can be significant, leading to stress, anxiety, and a profound sense of betrayal. These scams not only damage individual lives but also undermine the credibility and stability of the burgeoning crypto economy.
Twitter Cryptoscams – How to Protect?
To combat these scams, users are advised to enable Twitter’s Quality Filter, though it may inadvertently filter legitimate content. Moreover, a careful examination of the URL and the account name can help discern the authenticity of a tweet.
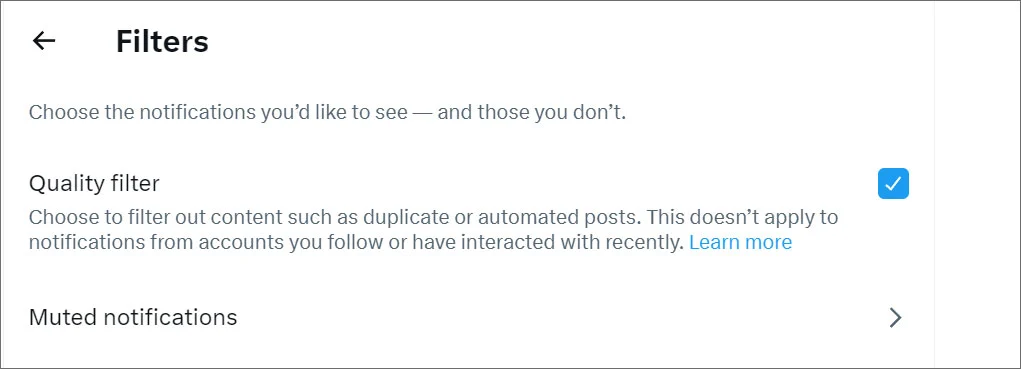
However, as this redirection is an inherent feature of Twitter, it remains a persistent threat, underscoring the need for heightened vigilance among users.
To avoid falling victim to crypto scams, consider the following tips:
- Always check the URL and domain name of the website you are visiting. Fake websites often mimic legitimate ones but may have slight variations in the URL. You can review whether the site is trustworthy by scanning it on the GridinSoft Web Scanner
- Be cautious of unsolicited offers and too-good-to-be-true promises, especially on social media. Scammers often use high-pressure tactics to create a sense of urgency and promise yet unseen profits.





