The digital world is seeing a surge in remote encryption attacks – a sophisticated ransomware attack. Although there is nothing new in this technology, it looks like a YouTube video uploaded ten years ago that is gaining recommendations just now. In this article, we’ll look at the intricacies, evolution, and effective countermeasures of these attacks.
What Are Remote Encryption Attacks?
If you follow cybersecurity, you probably know that ransomware is one of the most severe threats facing organizations today. Beyond the apparent damage, this kind of malware has the potential to paralyze a business and, in the absence of backups, irretrievably destroy all information. The 2020 pandemic contributed to the transition to the era of remote jobs. Companies worldwide have been transitioning their employees to work from home, adapting processes to efficiently complete tasks without the need to be physically present in the office.
Attackers have interpreted this concept in their way and are increasingly using the remote encryption model in their attacks. In a nutshell, remote ransomware attacks occur when attackers use one compromised device to encrypt data on other devices on the same network. This method’s peculiarity is that they can bypass most of the common security solutions in a rather straightforward way: by using a device that is not under their control.
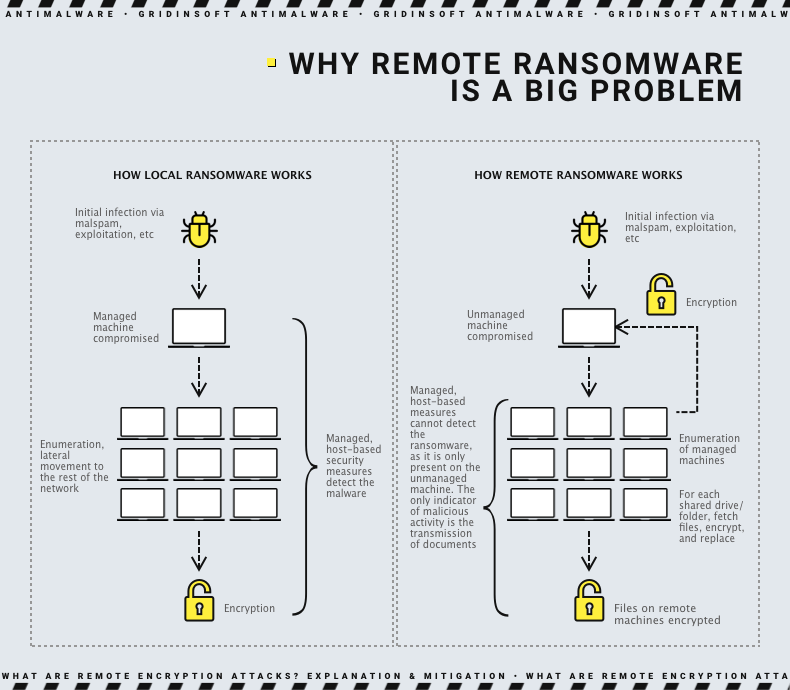
It is quite common to see the employees accessing their workstations from home using remote connections. This, exactly, is what gives the hackers such a huge advantage: home computers or laptops are rarely supervised by EDR/XDR or other security solutions. By running malware on this machine, adversaries can encrypt all they can reach in the corporate network, and remain undetected. Want to cipher more files? Find another remote connection, compromise the outstanding system, rinse and repeat.
Remote Encryption Attacks on the Rise
According to the report, about 60% of ransomware attacks involve remote encryption. Moreover, 80% of all compromises came from unmanaged devices. In particular, it is used by ransomware families such as Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal. By the way, this technology is not new, as there was already CryptoLocker in 2013, which targeted network shares.
Another point contributing to the difficulty of combating ransomware is the use of non-traditional programming languages, the ransomware-as-a-service (RaaS) model, and the choice of systems other than Windows as targets. In addition, in most cases, operators launch attacks after hours or on weekends. This severely hampers detection and incident response efforts.
Anti-ransomware methods
While no method guarantees 100% protection against ransomware, some methods can help. Corps should use a layered approach to security to reduce the risk of remote encryption attacks. This includes basic measures, such as regular software updates, employee training, strict password policies, and regular data backups, as well as more specific measures. Here’s a breakdown of more specific cybersecurity concepts and tools:
EDR/XDR
Endpoint Detection and Response is a solution focused on detecting, investigating, and mitigating suspicious activities on hosts and endpoints. It is primarily used for continuous monitoring and response to advanced threats. As the management takes place from a remote position, timely action can be taken even on weekends or outside of working hours.
Extended Detection and Response extends beyond traditional EDR. It aggregates and correlates data across multiple security layers (email, endpoints, servers, cloud workloads, and networks). This also can automate responses across various security layers, increasing speed and efficiency in mitigating ransomware threats.
Honeypots
Honeypots are decoy systems or servers set up to attract cyber attackers. They are designed to mimic natural systems with vulnerabilities to study attackers’ attack techniques and behaviors. Usually, these are inconspicuous files that trigger an alert if accessed or changed. They help detect ransomware attacks but require quick action and strategic placement to be effective. It’s worth noting that this assumes that the encryption process is already underway.
Security Information and Event Management
SIEM technology analyzes security alerts generated by applications and network hardware. These systems can ingest and process the detailed endpoint data provided by EDR solutions, enriching the overall security data set. In addition, SIEM’s powerful analytics can examine XDR-provided data in the context of broader organizational security, identifying complex attack patterns that might span across different domains. This integration provides a holistic view of security events, leading to more effective remote encryption detection and response.
Security Orchestration, Automation, and Response
SOAR technologies allow security teams to collect and monitor inputs. These include threat and vulnerability data from various sources. SOAR aims to enable companies to respond to incidents more efficiently and effectively by automating responses and reducing the complexity of managing numerous security tools.
Access Restrictions
Access Restrictions involve controlling who can access what resources within a network. By restricting access, the ability of ransomware to move laterally across a network is significantly hindered. For example, if ransomware infects one part of the network, access controls can prevent it from spreading to other parts.





