Cloud security researchers have discovered two easily exploitable privilege escalation vulnerabilities called GameOver(lay) in the Ubuntu OverlayFS module. These vulnerabilities could affect 40% of Ubuntu users.
What is OverlayFS?
OverlayFS in Linux is a unified file system used in Docker containers. Its function – modify files without changing the base filesystem. OverlayFS allows one directory tree to be overlaid on top of another with restricted read-only access. Changes are saved to the top layer, making it ideal for Live CDs and other uses. Unlike other file systems, actions go straight to the underlying file system, resulting in a simple and efficient implementation.
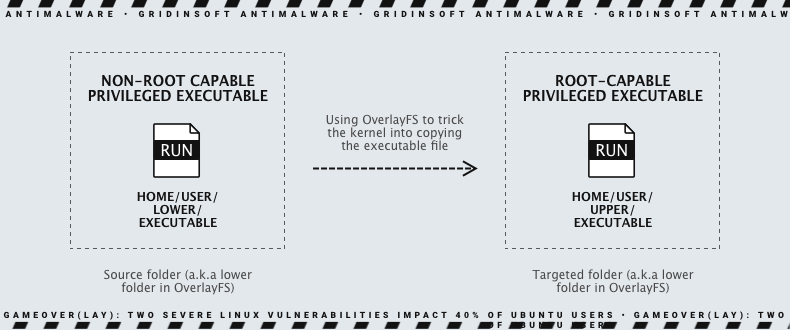
However, it can also be a security risk, allowing users to perform unintended operations on other filesystems. Multiple vulnerabilities have been found in OverlayFS, using the same primitives to bypass basic Linux security restrictions. Ubuntu’s OverlayFS has significant flaws that allow the creation of executables that can escalate privileges to root. Researchers found it possible to craft an executable file with “scoped” file capabilities and trick the Ubuntu kernel. Thus it copies it to a different location with “unscoped” capabilities, granting anyone who executes it root-like privileges. Ubuntu’s recently discovered vulnerability has the same flow as a 2020 Linux kernel vulnerability, and it’s unclear how Ubuntu became vulnerable to an already addressed issue.
GameOver(lay) Vulnerabilities Set Up Ubuntu Users
Researchers have discovered two Ubuntu Linux operating system vulnerabilities that could grant attackers elevated privileges. The two bugs affect OverlayFS, a widely used Linux file system. The vulnerabilities are named GameOver(lay) and are tracked as CVE-2023-2640 and CVE-2023-32629 and have a high CVSS score of 7.8. By the way, these issues are unique to Ubuntu, just one of the versions of Linux. They are related to Ubuntu’s changes in 2018 to its version of the OverlayFS module, specifically the setting of extended attributes that define user permissions. It’s important to note that while these vulnerabilities are easy to exploit, they require local user access, which should limit the attack surface. However, Ubuntu patched the vulnerabilities on July 24, 2023, and users are strongly encouraged to update their kernels.
About CVE-2023-2640 and CVE-2023-32629
In simple terms, GameOver(lay) enables the creation of an executable file with scoped file capabilities and tricks the Ubuntu Kernel into moving it to a different location with unscoped capabilities. It allows anyone who runs it to gain root-like privileges. Here are two vulnerabilities summarized:
CVE-2023-2640 – In Ubuntu kernels with both c914c0e27eb0 and “UBUNTU: SAUCE: overlayfs: Skip permission checking for trusted.overlayfs.* xattrs,” a non-privileged user can set privileged extended attributes on mounted files, causing them to be set on upper files without proper security checks.
CVE-2023-32629 – There is a local privilege escalation vulnerability in Ubuntu Kernels overlayfs ovl_copy_up_meta_inode_data, which skips permission checks when calling ovl_do_setxattr on Ubuntu kernels. GameOver(lay) allows an attacker to create an executable file with scoped file capabilities and trick the Ubuntu Kernel into copying it to a different location with unscoped capabilities, granting root-like privileges to anyone who executes it.




