Latin America has been hit by cyberattacks using malicious Google Chrome extensions. Attackers targeted financial institutions, booking sites, and instant messaging. Malware used in this attacks was dubbed Predasus.
Predasus Malware Targets Chromium-based Browsers in Latin America
Threat analysts have discovered a new malware called “Predasus”. Attackers use this malware to insert harmful code through a Chrome extension and employ this method to attack various sites, including WhatsApp’s web version. The attackers enter and exploit the targeted websites through legitimate channels to deploy Predasus malware, enabling them to steal users’ confidential and financial data. Predasus engages in several malicious activities, such as obtaining sensitive information like login details, financial data, and personal information.
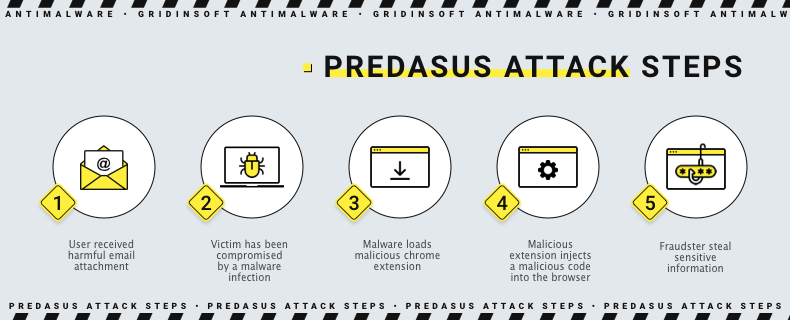
Predasus Infection Chain
Browser extensions can infect your device in various ways. They exploit browser or operating system vulnerabilities, including social engineering, to trick users into downloading them. The scenario is classic – a user opens an email attachment, a PDF, Word, or Excel file. The attachment contains malware that stealthily infects the user’s computer and is automatically deployed once downloaded. The malware then connects to the first command and control (C&C) server and downloads several files written to a folder named “extension_chrome” in the %APPDATA% folder. It terminates any process associated with Google Chrome and creates malicious .LNK files in several locations, replacing legitimate ones. In addition, the extension gains some permissions:
- “tabs”: Allows the extension to access and modify browser tabs and their content.
- “background”: Allows the extension to run in the background, even when the extension’s popup window is closed.
- “storage”: Allows the extension to store and retrieve data from the browser’s local storage.
- “alarms”: Allows the extension to schedule tasks or reminders at specific times.
- “cookies”: Allows the extension to access and modify cookies for any website the user visits.
- “idle”: Allows the extension to detect when the user’s system is idle (i.e., not being actively used).
- “webRequest”: Allows the extension to monitor, block, or modify network requests made by the browser.
- “webRequestBlocking”: Allows the extension to block network requests made by the browser.
- “system.display”: Allows the extension to detect and adjust display settings on the user’s system.
- “http://*/*”: Allows the extension to access any HTTP website.
- “https://*/*”: Allows the extension to access any HTTPS website.
- “browsingData”: Allows the extension to clear the user’s browsing data (such as history and cache) for specific websites.
Some of these permissions pose a risk because they allow an extension to access or modify sensitive user data.
What data is at risk?
According to IBM Security Lab, Predasus has been seen in many malicious activities, including modifying browser behavior and stealing sensitive data such as login credentials, financial information, and personal data. In addition, this attack uses WhatsApp Web. Since WhatsApp is popular in some countries such as Brazil, Mexico, and India, attackers can get enough potentially valuable information. Using a phishing payment site, scammers steal payment information from the victim under the guise of paying for a subscription. In addition, the phishing site asks for a confirmation code that the victim received via text message. In this way, the fraudsters access the victim’s bank account. Ultimately, the attackers sell the obtained data on the Darknet.
Safety Tips
To avoid unpleasant consequences, you must be cyber hygienic and watch what you install. Hackers always seek for new ways of malware spreading, and your attentiveness can effectively repel all their attempts.
- Be careful with emails you receive. This advice repeats again and again, as hackers keep using spoofed emails to spread malware. Strange topic, unknown sender, typos – all such things should raise suspicion.
- Only download extensions you’re sure about. Even using Chrome Web Store as a source does not mean you’re safe. Hackers have their ways to upload malicious plugins even to this marketplace – leave alone third-party sources.
- Use two-factor authentication and regularly update your browser and extensions to stay safe.
- Use effective anti-malware software. When it comes to protecting from malware attacks from different vectors, it is quite easy to whiff at some point. To avoid problems, a backup protection option is essential. GridinSoft Anti-Malware can offer you great protection, both reactive and proactive.
The increase in harmful Chrome extensions is concerning and emphasizes the importance of being cautious while browsing the web. There are concerns that this malware campaign may spread to North America and Europe.





