PUABundler:Win32/uTorrent_BundleInstaller is a Microsoft Defender detection that is associated with the installer of the once popular uTorrent client. It is detected by antiviruses because it contains a fair amount of additional software that is unwanted (PUA). Such programs can pose a security threat to your system. Let’s find out what’s wrong with it.
Why is uTorrent detected as uTorrent_BundleInstaller?
While being totally legitimate in its original form, uTorrent has some pitfalls to avoid. The main issue here is that it comes bundled with other software that is considered adware or potentially unwanted programs. Let’s look at what I’ve found during my research.
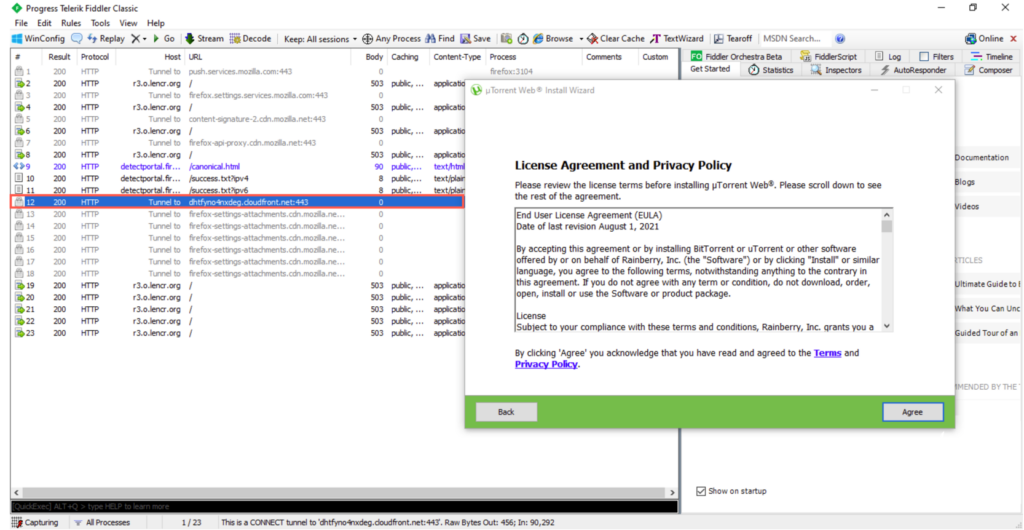
When installing the software itself, the application contacts a third-party offer provider before getting the user’s consent:
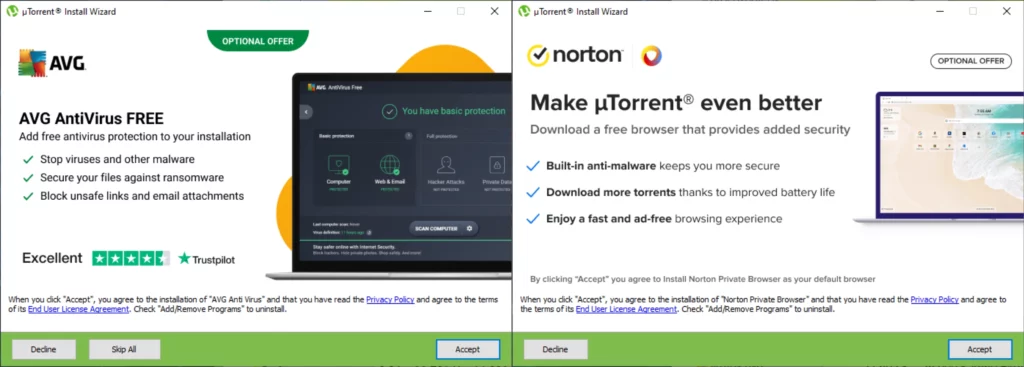
During the installation process, it offers to install several unrelated applications. Apart from being of dubious relevance, their banners do not provide a noticeable choice between installing and declining. This format is clearly intended to confuse the user and “soft coerce” the installation. Furthermore, users repeatedly complain of uncoordinated software.
In addition to the mentioned problems, there is evidence that together with uTorrent additionally installed a program such as EpicScale. It uses the idle time of your computer’s processor for its own needs. The idle capacity, according to the company, is used for solving various mathematical calculations and even mining cryptocurrencies.
Large amount of adware
Using uTorrent is often accompanied by a lot of annoying advertising windows and pop-ups. Annoying ads appear not only in the client window but also start to appear when using a PC. This is not only annoying for the user, but can also become a source of malware risk.
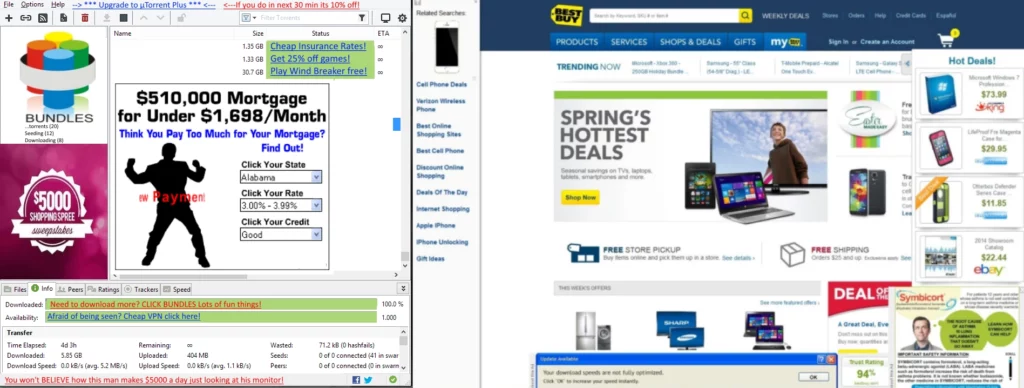
Unwanted programs like those presented by PUABundler:Win32/uTorrent_BundleInstaller can cause problems for users. They are especially known for changing browser settings, displaying advertisements or collecting data without their consent. In addition there is a user-confirmed fact that ads initiated by uTorrent uses an exploit to install malware.
Security vulnerabilities
In 2018, researchers discovered a vulnerability in uTorrent’s web interface that allowed attackers to remotely execute code on a user’s computer. This could have been used to attack users who downloaded and ran the uTorrent client with open Internet access.
$ curl -si http://localhost:19575/users.conf
HTTP/1.1 200 OK
Date: Wed, 31 Jan 2018 19:46:44 GMT
Last-Modified: Wed, 31 Jan 2018 19:37:50 GMT
Etag: "5a721b0e.92"
Content-Type: text/plain
Content-Length: 92
Connection: close
Accept-Ranges: bytes
localapi29c802274dc61fb4 bc676961df0f684b13adae450a57a91cd3d92c03 94bc897965398c8a07ff 2 1
Of course, after the wave of complaints raised by users, this vulnerability was fixed. But nobody guarantees that such an incident will happen again, especially considering uTorrent’s already dubious reputation.
Three uTorrent Installers – Why and for What?
One interesting fact: on the uTorrent website you can download not one, but three different installers, all of the same version. The difference between the web and desktop versions is obvious, but there are two desktop versions. They are downloaded from different links, and the only visible difference is smaller file size.
Perhaps the difference between the three versions of the uTorrent installation file is what additional programs or changes are included in each of them. These changes may be minimal and may touch, for example, pre-installed settings or advertising modules included in the client. Considering that their build times differ by mere seconds, they are unlikely to come from different developers. However, even such a small change may allow you to bypass detection by some antivirus vendors, or at least change the detection name.
How to remove PUABundler:Win32/uTorrent_BundleInstaller and unwanted programs?
If you have installed uTorrent and skipped the installation without paying attention to what it offers to install, it is rather probable that you have a lot of unwanted software installed in your system. Consider checking the list of installed apps and browser extensions, and remove anything you do not remember installing. This stuff may be related to PUABundler:Win32/uTorrent_BundleInstaller.
But since the unwanted programs often aim at making manual removal harder, I recommend using GridinSoft Anti-Malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.