Facial Recognition
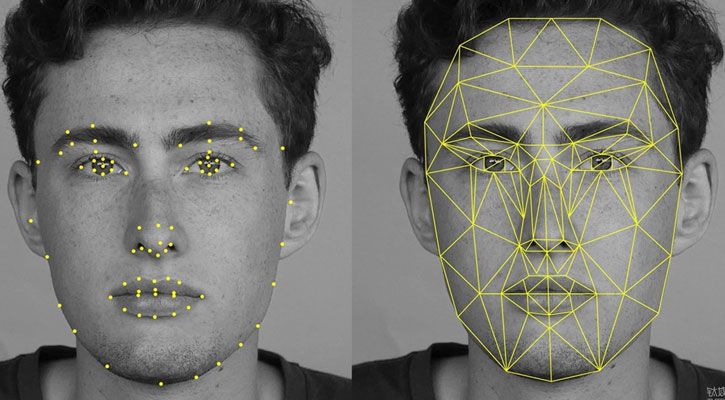
First, let’s refer to the technical details. Facial recognition is a system of personal identification or authorization by the face. We will review the purposes in a separate part of the article, so let’s concentrate on how it is done. There are several ways to recognize the face - depending on the hardware and software used in that procedure. Initially, face recognition technologies were based on a simple comparison of the visual data from CCTV with the data in recognition databases. Such a technique is not effective, as it is susceptible to changes. Beard, new haircut, weight gain - these things may nail the attempts to recognize the person.
The second generation of facial recognition systems started in the ‘10s. Different mobile device vendors offered their face recognition mechanism built into the front camera. It used the same systems as the “old” system - just a comparison. But since the device has one, or rarely two owners, it is feasible to create and remember multiple projections of the same face. Meanwhile, the “industrial-scale” facial recognition was oriented at more precise 3D face scanning and the newcomer of technological space - neural networks.
In 2017, Apple presented a mass-market solution for facial recognition. It was based on the 3D scanning using IR-cameras. The latter allowed to increase the quality of the recognition and its stability by orders of magnitude. 3D scanning creates a net of infrared dots on the user’s face during the image setup, creating a volumetric image of the face. In that way, the device can recognize its user from different angles, at any lightning and even after some changes in appearance.
But what do we have as of now? Top-tier systems rely on three technologies - neural networks, IR-scanning and visual recognition. The latter has changed since the first attempts to use it in the XX century - now it operates with the most actual pictures, and the databases are updated automatically and quite often - thanks to social networks. Moreover, some analysts predict the merge of neural network-based recognition with visual signatures. That will surely increase the efficiency of this method, which is extremely desired since it does not require any specific hardware updates and does not have distance restrictions. IR-scanning, which you can find in some flagman smartphones, is not very effective in crowded environments, and its efficiency is shed sharply with distance.
The use of Facial Recognition
The system that may recognise a person without any notification to the latter caused massive perturbations related to privacy. Therefore, after a short period when facial recognition systems were available on the broad market, they were banned for civil use - first by several US states and then by several governments of European countries. That severely struck the massive spreading of this technology. However, governments still have legal access to recognition systems and do not hesitate to use them when needed. Even some large companies did their “research” on this topic - but then ceased any activity in that direction because of privacy concerns.
In particular, Facebook was trying to create a facial recognition system based on the visual signature of its users. The data about over a billion users were collected - but then deleted after concerns that the U.S. government would consider banning facial recognition usage on the whole territory of the country. Meanwhile, some countries think about using this technology in law enforcement or public behavior control - primarily, those are South Asian countries.
Facial Recognition Is Everywhere
There are dozens of possible places where facial recognition may be applied. Most of them are already in use, some - without your knowledge. Let’s check them out.
Personal security
Most modern smartphones are equipped with a face recognition system. Depending on the price and manufacturer, it can rely on visual recognition and infrared scanning. Such an authentication system provides a pretty high security - it is hard or even impossible to hack it without the use of some sophisticated techniques.
The other place anyone can use face recognition for data/identity security is healthcare. In the majority of countries, medical secrecy is a point of concern for many hospital visitors. Despite the facts about the term you spent on the hospital bed, someone who managed to get your papers can also see the info about your chronic illnesses, the amount of money you paid, and so on. If you are a well-known person, it may be the basis for blackmailing. And the protection with face identification is what can save you from such an unpleasant case.
Banking operations authentication
Along with personal security, banking apps that became widespread over the past decade rely on facial recognition for client authentication. Logging in with the use of face authorization or possibly with the additional single-use passkey makes it impossible to hijack the online banking account. Approving the transactions bypassing facial recognition is in wide use - open “Wallet” or “Google Pay” apps. Such a progression can make the plastic cards and PIN codes elements of historical heritage. Apparently, together with banking trojans.
Law enforcement activity
The previous attempts of certain countries to apply facial recognition as a way to track certain persons and control the crowd first appeared in “the 80s. Nowadays, something that looks-like-working is implemented in China, India, and Russia. Still, those systems are working only “on paper” - there was no real evidence of their activity, as well as any success in counteraction to offenses.
Another edge for using facial recognition in law enforcement is road traffic control. Speed control cameras are already widely used in different countries, and car number plates can give complete information about their owner. However, identifying the driver is even more critical, especially when looking for a wanted criminal. Another case where driver identification may be essential is car hijacking.
Improved CCTV
The “softer” variant of a previous way of facial recognition usage. CCTV is used in many places and controlled not only by governments. Hence, the ability to recognize the person on the camera is important not only for law enforcement representatives but also for civilians. It may also be a great step towards increasing the accessibility for blind people - cameras will be able to recognize the person/animal near the door and notify about it.
Facial recognition may also play a great role in the CCTVs used in companies and gambling establishments. Controlling the personnel - exactly, the time they spend away from the workplace, is pretty hard without the ability to track their movements. Face recognition systems will make that process much easier and more effective. It is the same thing with gamers - cameras can control how much time a certain person has spent in the gambling establishment and notify the staff if it is better to give that person a portion of fresh air.
Metaverses
This appliance vector is as unique as others and is more related to personal security. While the latter was about using facial recognition to protect your info in real life, the first is more about protecting your identity. Since metaverses are likely the future of social networking, it is essential to keep the user profile (i.e., your virtual avatar) secured. And facial recognition is a much more reliable way of authentication than “classic” passwords, even with the use of 2FA.
How do corporations use Facial Recognition?
We named a big list of possible applications for facial recognition technologies. It is great to discuss that, but how about real-world use? Besides the named cases of face recognition used by governments, quite a few companies use it in their products and services.
Coca-Cola. The famous fizzy drink brand uses facial recognition in different corners of the world, primarily - in vending machines. The latter identifies the person in front of the box, matches it with the database, and shows personalized ads. Such a system was launched in Israel, China, and Australia.
British Airways. Passing the controls before boarding the plane never was a pleasant experience. One of the biggest airline carriers fixed it fairly progressively - by authenticating the passengers with facial recognition. That step decreased the time of boarding document check-ups by orders of magnitude. British Airways implemented that technology only at their home base - Heathrow Airport.
Cigna. Healthcare insurance company from the USA use facial recognition to secure the data about their clients. We mentioned that application way before - medical data protection is highly demanding. Possibly the further implementation of this technology can make cyberattacks on hospitals and healthcare companies useless - as all the data will be encrypted, and the only way to decrypt it is through a face recognition system.
That is not a full list of the companies that use face recognition technology as a complementary thing to their main products. But those are the best known and most potent ones - at least at the current stage of data protection measures. Maybe the release of more powerful quantum computers will set cybersecurity, and in particular data encryption upside down - who knows?