In a recent development, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has raised alarms over an actively exploited high-severity flaw in the Service Location Protocol (SLP). Designated as CVE-2023-29552, the vulnerability poses a significant threat, allowing attackers to execute denial-of-service (DoS) attacks with a substantial amplification factor. This revelation follows the disclosure of the flaw by cybersecurity entities Bitsight and Curesec earlier this April.
Vulnerability Overview
Tracked with a CVSS score of 7.5, the vulnerability in question exposes a DoS weakness within the Service Location Protocol. The flaw allows unauthenticated remote attackers to register services and utilize spoofed UDP traffic to orchestrate a DoS attack with a notable amplification factor. SLP is a protocol facilitating communication and discovery among systems on a local area network (LAN). It becomes a potential avenue for malicious actors to exploit.
And while before this threat was mostly a paper tiger, these days it is not just about theoretical possibilities. There are real cyber crooks out there making use of CVE-2023-29552. And the less time you give them to find out that you’re using a vulnerable SLP version – the less is the possibility that it will be used for malicious purposes.
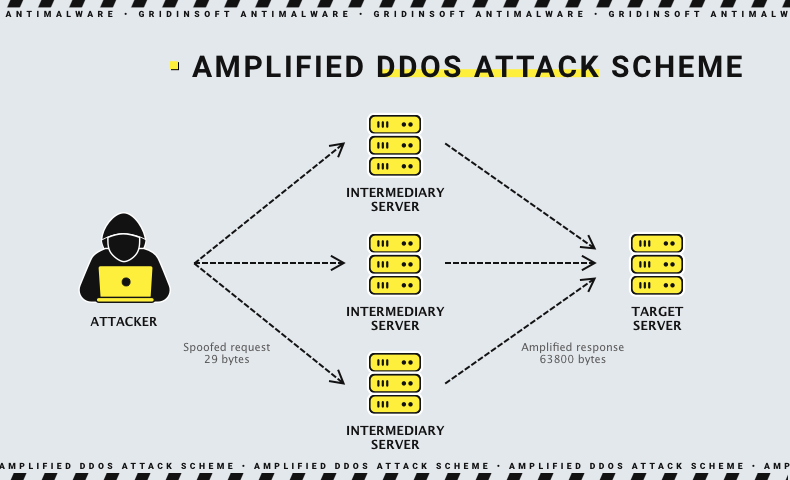
The nature of the DoS amplification attack leveraging CVE-2023-29552 is relatively straightforward yet potent. Instead of going head-on and bombarding a target server with requests, the cyber crooks take a more sly route. They send tiny requests to a middleman server, but here’s the twist – these requests are like magic spells, making the middleman server send back way bigger responses. And the key move here is faking the source of the request, making it look like it’s coming from the target’s IP. Now, here’s where it gets wild. Thanks to this trick, these bad actors can flood even the most guarded targets with traffic.
Mitigation Measures
In response to the real-world exploits of this vulnerability, federal agencies are mandated to implement mitigations promptly. CISA has set a deadline of November 29, 2023, for federal agencies to secure their networks by applying necessary measures. The recommended mitigations include disabling the SLP service on systems operating in untrusted network environments.
Unfortunately, there is no dedicated solution meant to stop the exploitation without sacrificing any functionality. However, there is the ability to make the exploitation much harder, if not entirely impossible, with the usage of modern security software.
- EDR/XDR
Think of EDR as your vigilant guardian, keeping a watchful eye on endpoint activities. It’s the first line of defense, swiftly responding to any suspicious behavior to thwart potential ransomware threats. XDR extends its vigilant reach beyond endpoints. It’s like having a superhero with enhanced senses, covering a broader spectrum of detection and response capabilities against evolving cyber threats. - SIEM/SOAR
SIEM aggregates and organizes security event logs, providing you with a comprehensive overview of your cybersecurity landscape. It’s the strategic hub for informed decision-making. SOAR steps in to automate incident responses, ensuring swift and precise actions in the face of emerging threats. It’s the sidekick that streamlines your defense mechanisms. - Back up your data and store those backups offline or on a separate network for added protection. Backups are the ransomware attacks’ kryptonite, as they can do nothing if you just recover everything back.
- Staying informed through reading the news and studying current material on cybersecurity and related topics is paramount in today’s dynamic and interconnected digital landscape. Reading the news and studying current material on cybersecurity is not just a habit. It’s a proactive approach to staying ahead in the ever-evolving world of digital security.