Mobile Security
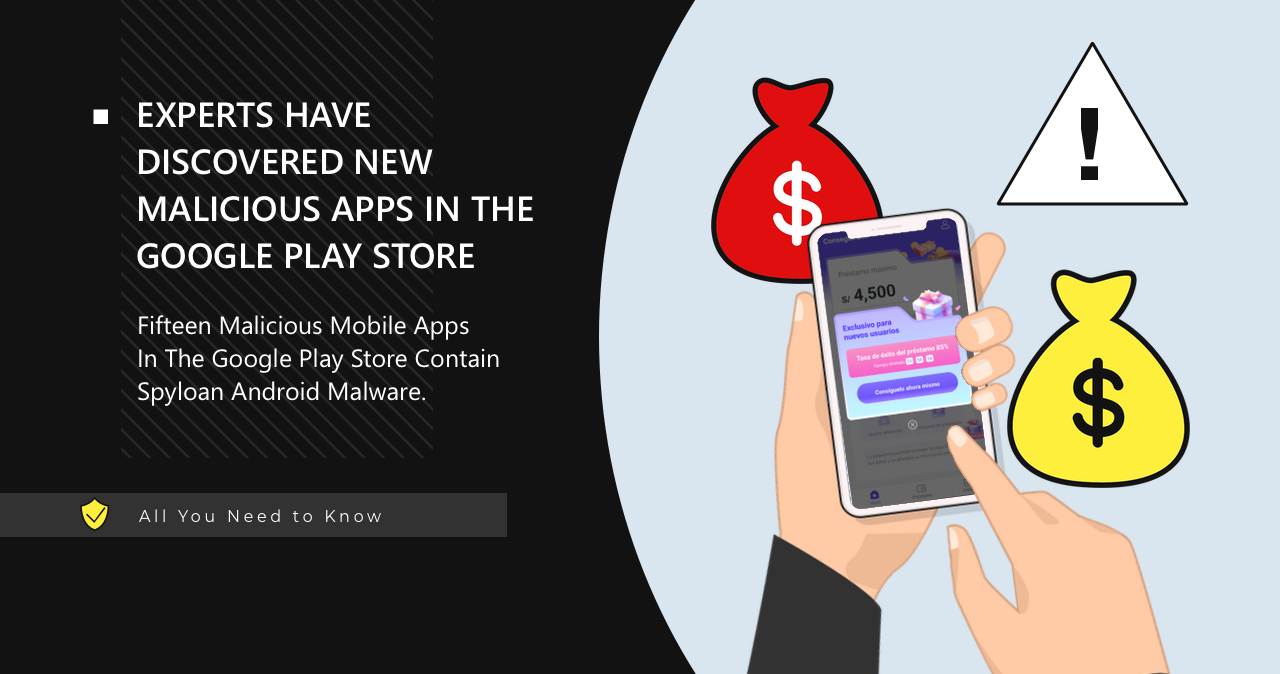
SpyLoan Virus Found in Loan Apps on Google Play Store
Experts reported the discovery of a new set of 15 malicious mobile apps in the Google Play store that contain…
Two Android Zero-Day Flaws in Google Pixel Exploited
Google has disclosed that two Android zero-day security vulnerabilities have been detected in its Pixel smartphones. The patch is already…
SecuriDropper Bypasses Google Play & Android Defenses
SecuriDropper is a rare example of the Android dropper malware that operates under the dropper-as-a-service (DaaS) model. This malware is…
Malicious WhatsApp Mods Spread Through Telegram
Some WhatsApp mods, which are unofficial versions of the app, have been found to contain hidden spyware. This spyware is…
What is Android:TrojanSMS-PA detection?
Android:TrojanSMS-PA is a detection name from a built-in Huawei security tool. This particular name recently appeared as a detection of…
Ukrainian law enforcement officers arrested members of the hacker group Phoenix
The Security Service of Ukraine (SBU) announced the arrest of…
NUCLEUS: 13 Problems Threat to Medical Devices, Automobiles and Industrial Systems
Forescout and Medigate Labs issued a report on NUCLEUS:13 problems…
Expert hacked 70% of Wi-Fi networks in Tel Aviv for research
CyberArk specialist Ido Hoorvitch hacked 70% of Wi-Fi networks in…
Microsoft warns of dangerous vulnerability in Surface Pro 3 devices
Microsoft engineers have published a security bulletin on a new…
Ukrainian cyber police arrested ransomware operators who “earned” $150 million
Ukrainian Cyber Police have arrested two operators of an unnamed…
Experts showed fraudulent payments from a locked iPhone with Apple Pay and a Visa card
Scientists talked about how to make fraudulent payments using Apple…
Encryption algorithms for 2G networks have been intentionally weakened
A group of scientists from several European universities published a…
Google stopped trying to shorten URLs in the address bar
Google’s experiment with attempt to shorten URLs (hiding parts of…
Quantum computers will be able to hack bitcoin wallets
Experts argue that quantum computers will be able to hack…
Six 0-day vulnerabilities fixed in Windows, including a commercial exploit issue
As part of June Patch Tuesday, 50 vulnerabilities in Microsoft…
NASA has faced 6000 cyberattacks in the past four years
NASA has identified more than 6000 different cyberattacks over the…
Qualcomm Mobile Station Modem vulnerability threatens 40% of smartphones
More than a third of all smartphones in the world…