We used to think of anti-malware software as a program that features all kinds of supplementary services. VPN plan, disk encryption tool, guest mode and parental control – all of them are installed along with the exact antivirus, and that’s no way to get rid of them. And the users are forced to pay for that functionality even if they will use only several of them, or didn’t use them at all. All of these functions are offered as a standalone program, issued by the other developer, so the user can apply them of their own will. Besides overpayment, there are also performance issues. A bunch of processes running in the background of your PC is not great when you want to have full power from your hardware.
Trojan Killer offers you the essential antimalware software functionality, together with the system recovery abilities. It will perfectly fit your PC regardless of its configuration and modernity. Let me show you the key advantages of Trojan Killer.
1. Portability
Most antivirus software is not capable of curing other PCs, unless you purchase a licence that suits several computers. With Trojan Killer, it is possible to scan&clean all computers you need. The program can be mounted on a USB drive, giving you the ability to carry all benefits in your pocket. It has the same efficiency and same amount of features as the static version.
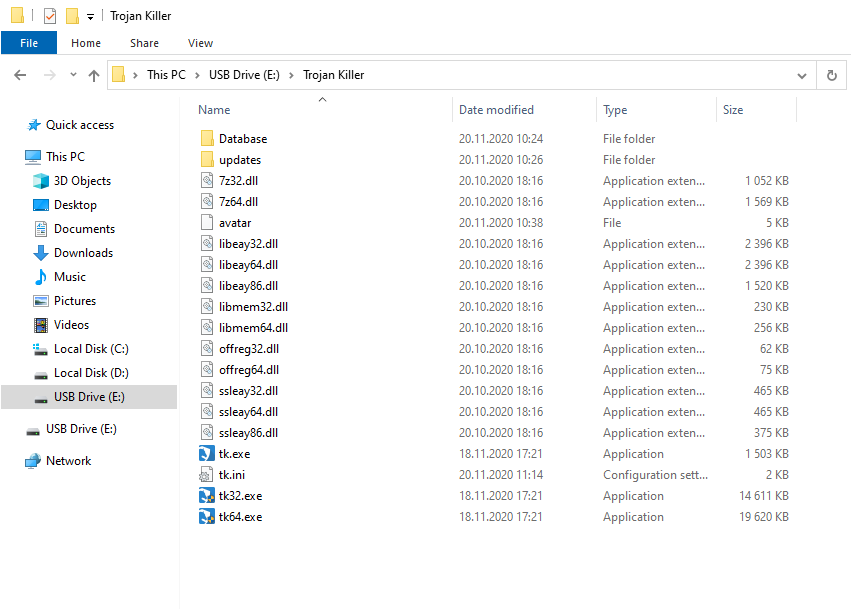
Another advantage of the portable version is that it can easily circumvent the blockages from the malware running in the infected system. The latter usually prevents the launching of installation files of antimalware programs. Since Trojan Killer Portable is about to be installed on the other PC, nothing can stop you from wiping out malware.
2. Perfect detection capabilities
Trojan Killer has a triune detection system that is capable of successfully spotting malware of any sort. Regardless of how new the malware is, or if it is masked through various methods, Trojan Killer will be capable of its detection. Let’s review each part of this system to understand what we are talking about.
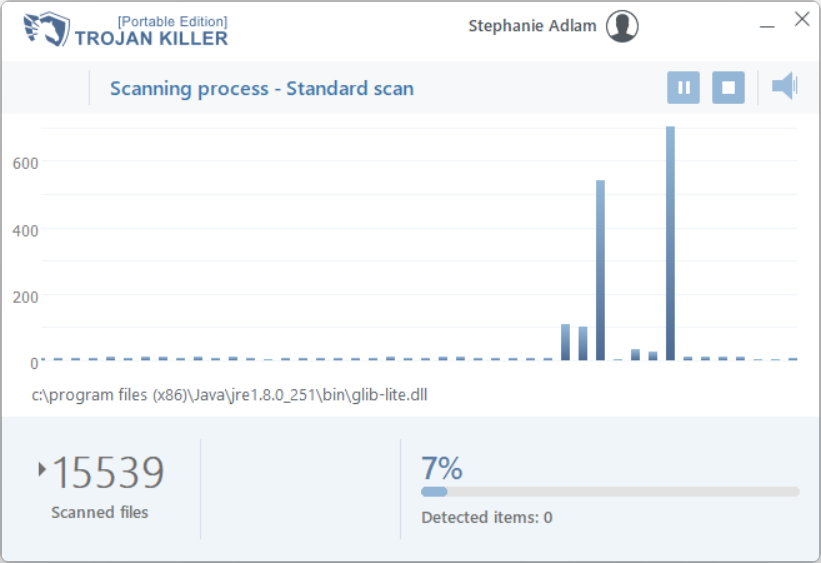
Database-backed detection is what all antivirus software began from and still relies upon. The hashes of files on the disk are compared with a database of malware hashes, so the match means that there is malware. It is great for detecting past threats that were already recognised. However, to spot and remove novice hazards, or ones obfuscated for stealthiness, database detection is less than great.
Heuristic detection is what helps the anti-malware program to detect what is out of databases’ sight. This mechanism analyses the behaviour of the apps and can detect the malicious thing by the actions it does. Calls to the hardware drivers, unusual network connections, commands executed in the console – all these things are the point of increased concern. And heuristic engines analyse them precisely, to allow Trojan Killer to spot and stop all possible hazards.
The neural network is a novel way of malware detection. The ability of neural networks to detect impossibly small signatures makes it perfect for malware detection. Even the most concealed malware that may pass through the previous two systems will likely be distinguished and marked by a neural network. It is a very long and uneven process to study the neural network properly. It is also worth noting that they show the best efficiency only when applied together with database and heuristic systems.
3.Browser reset functionality
Certain species of malware, generally the ones that manipulate the contents in your browser, have very unpleasant remnants. Even after their removal, you’d possibly face issues with opening some pages and general browser malfunctions. That happens because the malware we mentioned above changes the settings of your browser for its own purposes. Fortunately, Trojan Killer is able to wipe these changes by resetting your browser settings. Just several clicks – and you will not see the effects of malware activity anymore.
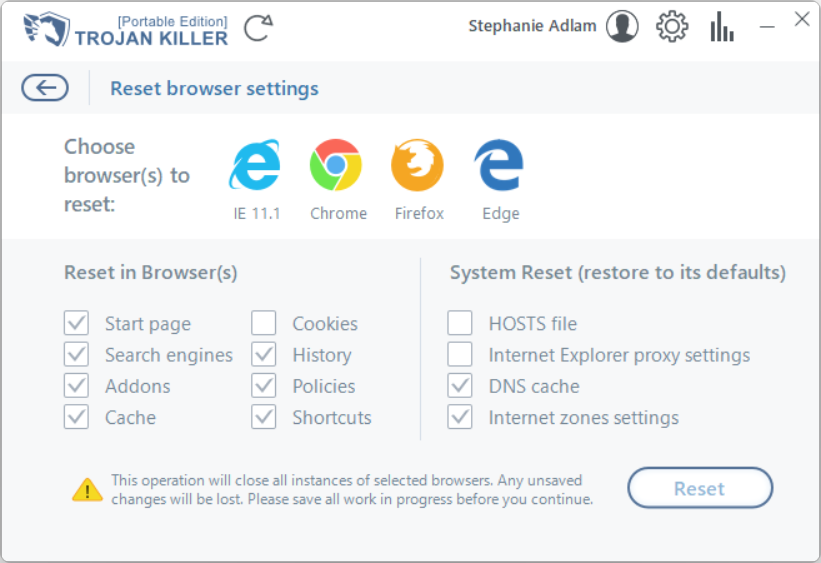
4. System recovery capabilities
Aside from the damage to networking facilities, malware almost always deals significant damage to the operating system. In particular, it often touches HOSTS files, registry, Group Policies, and Task Scheduler. When a malicious thing is gone, it is essential to get rid of all of the junk it left after itself. Trojan Killer is able to fix the system parts automatically when it detects malware-related changes. Additionally, you can reset HOSTS files on demand, by pressing just a single button in a Reset Browser Settings window.
5. High resource efficiency
“Big” antivirus software is similar to a system in the system. They are huge, with a large number of modules and high integration into the system. Moreover, each of these modules requires CPU time and RAM amount. In total, that results in a constant load of your hardware. It is an exceptionally unpleasant case for laptops, which can have their battery drained pretty fast.
Trojan Killer is tiny and does not make any serious impact on the PC performance. Even during the scans, it does not take a lot – you will be able to use the system as nothing happens. Regardless of such an economy, it remains fast and effective in its scanning.
6. Often database updates
Even the sharpest knife becomes dull with time. The same story is about detection databases – and two other detection modules present in Trojan Killer. To retain the program’s efficiency, the automated system collects the most modern malware samples and updates the database each hour. The analysts’ team, on the other hand, is doing its best to bring qualitative updates for the heuristic detection system and neural network functionality.
7. Easy interface
Antivirus programs should be easy to use for everyone, regardless of the level of computer knowledge. That rule is relevant for any “essential” application. Trojan Killer offers an extremely simple interface that is pretty easy to deal with even for a beginner. Main and the most demanded functions are placed on the main screen; the settings tab is not overloaded and easy to browse through. The Reset Browser Settings window is available as an internal window, and also as a separate application.
8. Full-time tech support
Sometimes, even the most skilled users struggle to make a proper decision. The support team of Trojan Killer will help you to solve the issue. Problems with PC, suspicious activity, or any questions about the program functionality – you are welcome to ask the support team. They will gladly help you any time, until the problem is solved.
9. 15-day free trial
To test the program capabilities and ensure that Trojan Killer is what you are looking for, you can get a 15-day trial period with full program functionality. You will be able to repair your system, reset browsers, and perform 4 different types of system scans just as with a paid licence. Over two weeks of testing is more than enough to get all benefits of the program and make a decision.
10. Affordable price
There are several different licence types for Trojan Killer, but all of them are way cheaper than their counterparts. For half a year, you need to pay only $24, and the annual licence will cost you $36. Two years of Trojan Killer usage cost $47 – making the monthly price twice as cheap compared to the half-a-year licence. Additionally, you can get a discount on certain notable dates – and make the program even cheaper for you. Try it out and see how the original antivirus looks like.