So Redis walks into a bar and the bartender asks, “Why so bloated?” Turns out Redis has been hitting the memory buffers a bit too hard lately. The popular in-memory database now has a vulnerability that lets anyone – yes, literally anyone – crash your server by making it consume memory until it keels over. No password required. How thoughtful.
What’s the Deal with This Vulnerability?
Redis developers recently disclosed CVE-2025-21605, which is basically Redis forgetting to check how much it’s eating. The vulnerability allows unauthenticated clients to trigger unlimited growth of output buffers, eventually exhausting server memory. It’s like your teenager’s appetite, but for RAM.
The technical classification is CWE-770 (Allocation of Resources Without Limits or Throttling), which is a fancy way of saying “this program doesn’t know when to stop.” This affects all Redis versions from 2.6 to just before 7.4.3. And yes, if you’re reading that correctly, that’s practically all versions in common use.
Why Should You Care?
If you’re running Redis exposed to the internet (which hopefully you’re not), this is especially bad news. Even if you’ve set a password, the “NOAUTH” responses can still trigger buffer growth. So your password protection is about as effective as a screen door on a submarine.
For those unfamiliar, Redis is an open-source database that’s incredibly popular for caching, session management, and message brokering. It’s fast because it works in memory – which also makes this vulnerability particularly nasty. When Redis runs out of memory, it doesn’t gracefully degrade – it crashes, taking down whatever services rely on it. This can create cascade failures across your infrastructure, similar to what we see in many modern cyber attacks.
How Bad Is It Really?
On a scale of “mildly annoying” to “oh no, call the incident response team,” this is firmly in the “weekend-ruining” category. The vulnerability requires minimal skill to exploit – no elaborate hacking sequences like in the movies. An attacker just needs to find your Redis instance and send some carefully crafted requests. Even script kiddies with basic automated tools could pull this off.
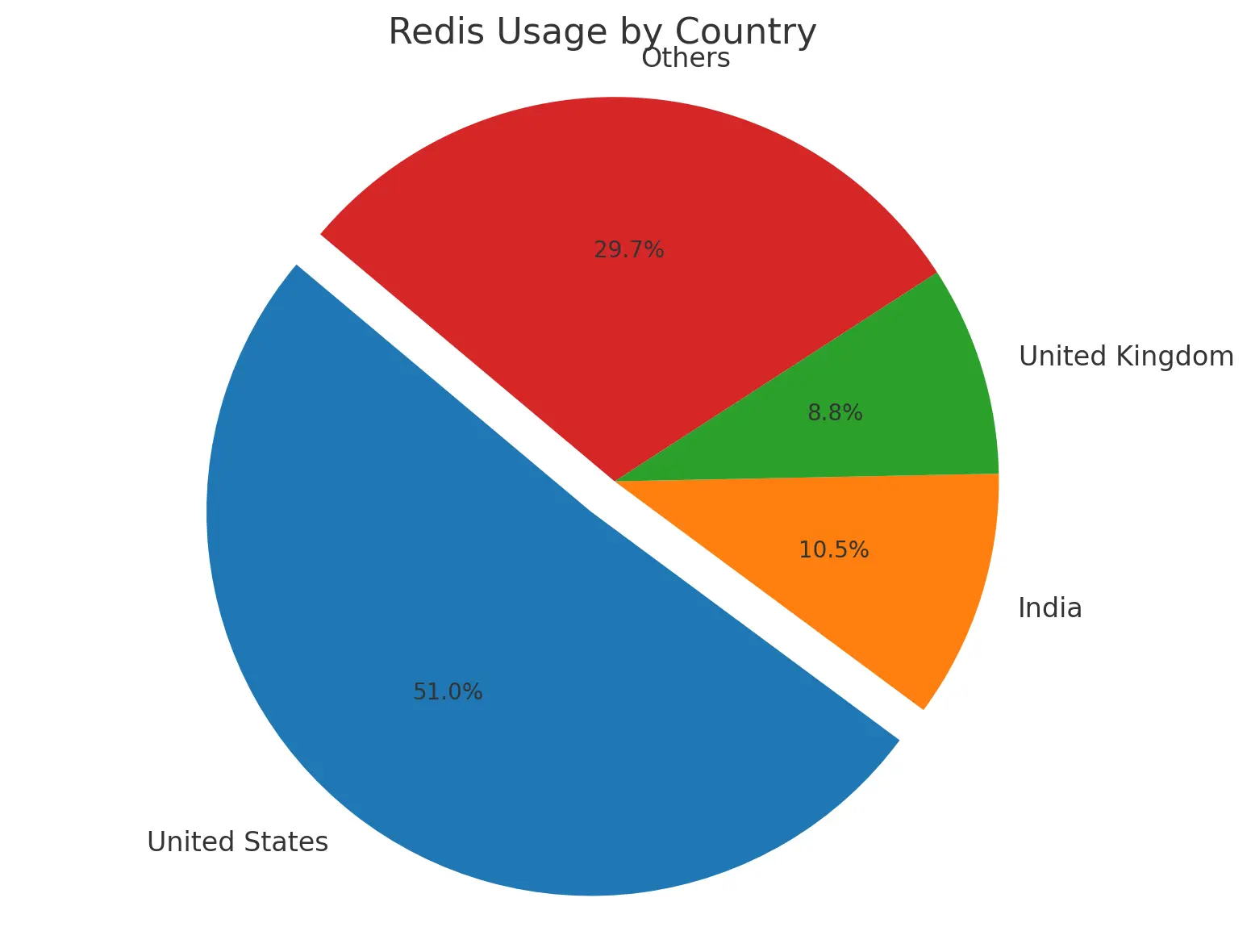
What makes this particularly concerning is that over 23,000 companies use Redis, with about half in the United States. Many are still running older versions, because upgrading databases is about as fun as a root canal. AWS and Google Cloud users are still deploying outdated Redis versions (6.x, 5.0, 4.0), so there’s a good chance many instances are vulnerable.
The real-world impact? Your e-commerce site goes down during a sales event. Your users get logged out randomly. Your metrics and monitoring disappear. All while you’re frantically trying to figure out why Redis keeps crashing. Fun times.
The sneakier concern is that attackers might use this as a distraction. While you’re busy restarting services and putting out fires, they could be exploiting other vulnerabilities elsewhere in your infrastructure. It’s a classic misdirection play that we’ve seen in sophisticated DDoS attacks before.
Fixing the Problem
The most obvious solution is to upgrade to Redis 7.4.3 or later. This version properly enforces output buffer limits, preventing the unchecked memory consumption. If you follow basic security best practices, keeping software updated should already be on your to-do list anyway.
But let’s be realistic – sometimes immediate upgrades aren’t possible. Maybe you’re running a legacy application that depends on a specific Redis version, or perhaps your change management process moves at the speed of continental drift. In that case, you have a few options:
- Block unauthenticated access using firewalls, iptables, or cloud security groups
- Enable TLS with client-side certificate authentication
- Isolate Redis instances in their own network segments
- Set up monitoring to detect unusual memory usage patterns
These mitigations aren’t perfect – they’re more like putting a band-aid on a leaky pipe. You’ll still want to plan that upgrade, but at least you won’t be completely exposed in the meantime. This vulnerability is just one example of why implementing a solid vulnerability management strategy is crucial for modern organizations.
The Bottom Line
CVE-2025-21605 is a perfect example of how even simple vulnerabilities in popular software can create significant security risks. The fact that it affects unauthenticated users makes it particularly dangerous in today’s interconnected landscape.
So check your Redis versions, plan that upgrade, and while you’re at it, maybe review what else in your infrastructure might be exposed to the internet unnecessarily. Security is rarely about big, dramatic threats – it’s usually these mundane, easily-fixable issues that end up causing the most problems.




