
What Is CDN SSL/TLS Security?
CDN SSL/TLS security is a layer of protection at the intermediary server between servers and user content. Besides providing the continuity of access, this protection also ensures that no counterfeits and spoofs appear on the way from a client to the server. Its importance is quite hard to see without the detailed explanation of each of its elements.
What is CDN?
CDN, or content delivery network, is a part of network infrastructure that is responsible for increasing the speed of access to the target website. Not all clients are located close enough to the server, which may lead to response speed drops and long page loading – a pretty unpleasant experience. Such a situation may also appear when the hosting used to maintain a site does not give the proper performance – and moving to the other hosting may be cost-extensive or ineffective. CDN aims at solving this problem by offering a local intermediary server that contains parts of the required content, and has a shorter path of connection to the target server.
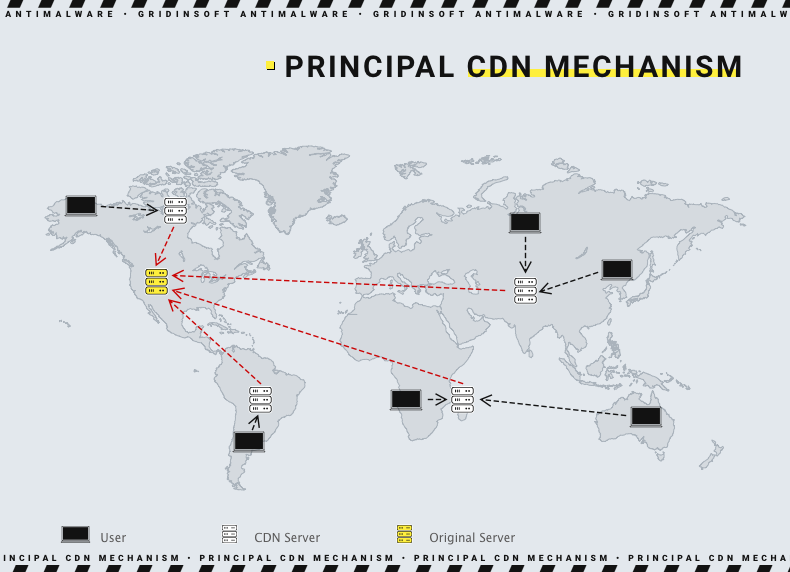
Instead of having a long way through the providers on both sides of the connection, the user connects to a content delivery network, which is ready to give a part of a response. For the other part, it communicates with the end server through a much shorter channel than a regular request will routinely go. To achieve such a boost, CDN servers should have certain content cached – for example, main pages of connected websites. As the model of content delivery network relies upon being globally distributed, applying it will make the overall performance of the site for any client way better.
Besides the profits for an ordinary user, there are also sensible benefits for server maintainers. Decreasing the costs for bandwidth – a primary expense paid to any hosting provider – is the smaller one. A bigger benefit is increasing the server capacity and the ability to counteract the DDoS attacks. Well then, this is a topic of the next paragraphs.
What is SSL/TLS security?
SSL, or Secure Sockets Layer, is a network security protocol that provides a basic data protection for the process of client-server communication. Initially designed in ‘90s, it was projected to fit its contemporary hardware technologies. The developer – Netscape Communications – was intended to implement it in their browser, Netscape Navigator. Later, it was republished as well-known Mozilla Firefox. However, the protocol was considered effective enough to be used globally, as a standard for network communications protection. Since 1996, it is used in a wide range of web browsers, and it served as a basis for creating the HTTPS protocol we use today.
TLS, or Transport Layer Security, was released as an ideological successor to the SSL. It featured some changes that were aimed at fixing the issues present in contemporary SSL versions. They were used along, as equivalent protection measures, since the TLS release in 1999. However, due to the SSL upgrade capacity draining, it was considered unsafe in 2016, and the regulators recommended to use TLS 1.3 instead. This led to the gradual SSL substitution – these days, in 2022, most of the connections you use every day are protected with TLS. However, SSL is still applied at the places that do not contain any sensitive information – for example, for some technical data exchange, that does not involve user-related information. Additionally, certificates remain in use, and are required to establish a TLS-protected connection.
TLS protocol in its latest version – 1.3 – features the most completed measures against any connection eavesdropping. To ensure the impossibility of traffic decryption, it has additional check-ups of a used encryption. “Weak” hashes like SHA-224 and MD5 are also forbidden. Additionally, this version of the protocol stopped using vulnerable methods of session key retrieval and implemented an obligatory digital signature. All this provides best protection against currently existing threats, and seems to be good enough even for possible dangers in future. For example, elliptic encryption will be hard to hack even with quantum PCs – which are capable of fast decryption of more common symmetric keys.
How SSL/TLS security influences CDNs?
As it was mentioned above, content delivery networks do not contain a lot of sensitive information. All really sensitive data, like databases of users’ profiles, are stored on the main server. However, cookies, users’ requests information and other minor data are still located on the CDN storage. Moreover, even personal information we’ve noted above is still transferred through these intermediary servers. And the more elements are in the chain – the bigger is the probability of a breakdown.
CDN SSL/TLS security configurations are responsible for isolating an entire traffic flow from interception and decryption attempts. Man-in-the-middle attacks are rare these days, but attacks targeted on a certain person may still involve this technique in combination with other approaches. CDN maintainers, especially ones that try to increase their margin, may simply ignore the encryption recommendations, as they usually require additional hardware. Additionally, web browsers still support most of the outdated protection standards, such as SSL and TLS 1.0-1.2. You can sometimes establish the connection with less secure encryption without knowing it – still not completely naught on protection, but with way more dangers to your security measures.
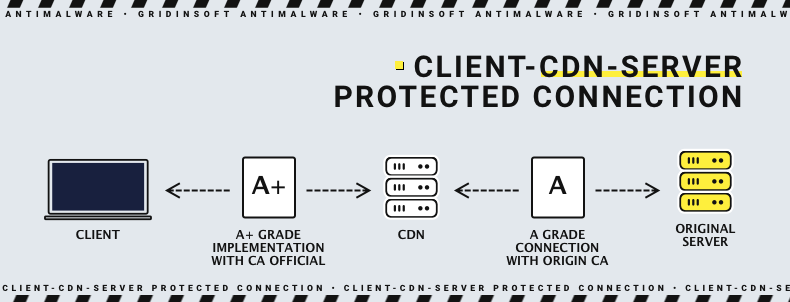
Meanwhile, the increased secureness of a Client-CDN connection allows the endpoints to use less beefy protection. Still, we does not mean no protection or obsolete standards, but in some situations a protection of a lesser grade may be applied. This can be used by companies that control both endpoints and CDNs, or the latter is highly-trusted. For example, a Client-CDN chain may have the most robust protection (A+ grade), while CDN-Endpoint connection uses weaker encryption – B- or even C-grade (but still usually A). Such a trick allows the host to once again decrease the maintenance costs even more, although it may be a security concern. Using a weak cipher or a vulnerable technology may lead to data breaches, if the endpoint is attacked with APT.
CDN protection from DDoS attacks
DDoS attacks have always been a real mess, regardless of their nature. Generally, they are targeted and performed by a botnet – a huge chain of computers infected with a backdoor malware that guides them to send requests to the server. A more rare case is when the site experiences troubles with servicing each client due to their enormous, but natural flow. For example, the pages that stream some breaking news or the info about the latest football event or song contest may just be overwhelmed with the amount of users who try to check their content. CDNs act as a shield for excessive traffic, as they are taking a great share of calculations on their part. Simultaneously, they are located in a lot of countries around the world, hence traffic will disperse among them rather than ringing a single servers array. Both botnet attacks and crowds of interested individuals will likely be served with a way less load upon the endpoint.
However, exact CDNs may also be the target of a DDoS attack. In this way, crooks will not disable the connection to the server as is – the requests will go directly to the endpoint as they cannot reach the intermediary server. That will barely create enough traffic to disrupt the server functionality, but when CDNs are attacked for a long period of time, it may create an unpleasant waiting time for the user. Additionally, long page loading time is a common reason for search engines to decrease the page rating in the ranking. Fortunately, the classic protection methods against DDoS attacks work well with content delivery networks as well.
