
What Is DNS Tunneling
The DNS is essentially the vast phone book of the Internet. And DNS is also the underlying protocol that allows administrators to query the DNS server database. DNS Tunneling attack turns the domain name system into a weapon for cybercriminals. Because DNS is a highly trusted and widely used system on the Internet, this attack takes advantage of this protocol. It allows malicious traffic to penetrate the organization's protection (the victim). Cybercriminals use malicious domain names and DNS servers to bypass protections and completely steal data. However, before we get to the attack, let's uncover the DNS mechanism in more detail.
What is DNS?
DNS (Domain Name System) is a global database of website addresses. Its job is to translate human-friendly domain names such as example.com into their corresponding machine-friendly IP addresses such as 123.45.67.89. This way, we don't have to memorize long and complicated numbers to get to the right site. Instead, we quickly remember domain names and can access our favorite news, sports, or elsewhere.
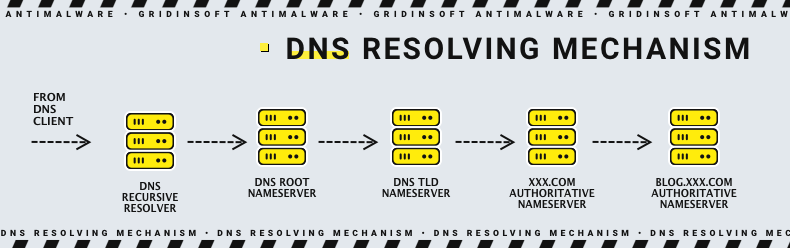
Many services rely on the large number of DNS conversion requests that appear all the time. For this reason, DNS traffic is widely used and trusted. Since DNS was not invented to transmit data packets but only to resolve names, it was not originally seen as a threat to malicious communications and data theft. However, DNS is more than just a domain name translation tool. DNS queries can also transfer small portions of data between two devices, systems, and servers, making DNS a potential vector for attacks.
Unfortunately, most organizations often don't analyze DNS packets for malicious activity. Instead, they focus on analyzing web or email traffic where they think the chance of an attack is higher. However, it is best when each endpoint should be closely monitored to prevent DNS tunneling attacks.
It's important to know
Since a DNS tunneling attack is difficult to detect, it is a widespread cyber threat. It is used to route DNS requests to an attacker-controlled server and provides them with a hidden channel of control and management and a path to steal data.
Typically, DNS tunneling includes useful data that is added to the target DNS server. In addition, that data can be used to gain control over the remote server and applications. Moreover, for this attack, the compromised system must be connected to an external network to gain access to the internal DNS server. Cybercriminals control the server, which acts as an authoritative server, and the domain name to complete server-side tunneling and executable data payload programs.
How does DNS Tunneling Work?
A DNS tunneling attack takes advantage of the DNS protocol and tunnels malware or data through the client-server model. It starts when a user downloads malware or an attacker manages to exploit a vulnerability in a compromised device to transmit a malicious payload. In most cases, the cybercriminal wants to keep a connection to the compromised machine. This will allow him to run commands on the target device or exfiltrate data. In addition, the attacker can establish a control and monitoring (C2) connection. Such traffic must be able to pass through various network perimeter security measures and avoid detection until it crosses the target network.
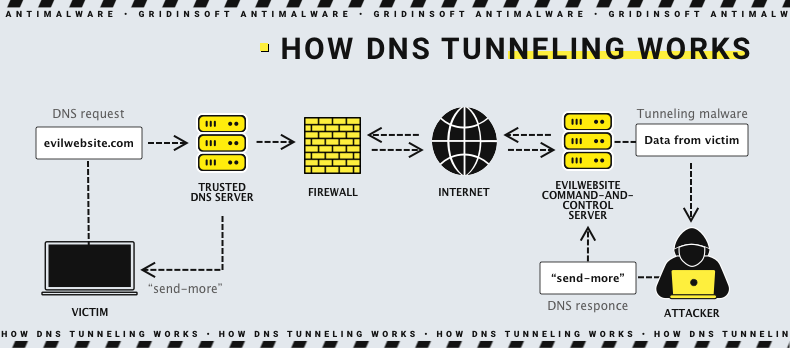
For this reason, DNS is an appropriate option for tunnel configuration. This common cybersecurity term refers to a protocol connection that transmits payloads and data (commands) and passes through perimeter security measures. Thus, a DNS tunneling attack manages to hide information in DNS queries and deliver it to a server controlled by a cybercriminal. Hackers can use base32 or base64 character sets, or even encrypt the data. Such encryption will pass unnoticed by simple threat detection utilities, which search the open text. To set up a DNS tunnel, the attacker registers a domain name and sets up an authoritative name server under his control.
Next, the malware or payload on the compromised device initiates a DNS query for the subdomain that defines the encrypted link. The recursive DNS server (DNS resolver) receives the DNS query and forwards it to the attacker's server. The server responds to the compromised device with malicious DNS data (commands). Thus, the attack goes through without triggering any security measures.
A DNS tunneling attack can be divided into several stages:
- 1. A cybercriminal registers a domain and points it to a server under his control. Then the tunneling malware is installed on it.
- 2. The cybercriminal infects the device with malware, penetrates the victim's firewall, and takes control of the device on the network or the entire network.
- 3. Then, they modify the configuration of the infected machine and send a request from it, which is transliterated by the domain name system, to the attackers' server.
- 4. The DNS resolver sends the DNS query back to the authoritative DNS server, which is controlled by the attacker and contains tunneling software.
- 5. An undetectable connection is established between the hacker and the target, and the primary payload is introduced.
DNS tunneling detection
There are several methods for detecting DNS tunneling attacks. They can be divided into two main categories - payload analysis and traffic analysis.
Payload analysis - DNS payloads for one or more queries and responses are checked for signs of tunneling.
- Examining the request and response size. Since DNS tunneling utilities try to place as much data as possible in requests and responses, tunneling requests will have long labels. For example, up to 63 characters, and generally long names up to 255 characters.
- Disorder of hostnames. Authentic DNS names usually contain dictionary words and have some meaning. However, names that are encoded usually have no order, and they even use a set with a large number of characters.
- Statistical forensics. It is also possible to detect tunneling by checking the specific character composition of DNS names. Real DNS names usually contain fewer digits, while encoded names often contain many. Examination of the percentage of numeric characters in domain names and the percentage of the length of the longest significant substring (LMS) may also help.
- Uncommon DNS Record Types. You can check DNS records that the standard client does not usually perform. For example, you can examine TXT records.
- Violating a policy. If a policy mandates that every DNS lookup goes through an internal DNS server, violating that policy can be used as a detection method.
- Special Signatures. You can use a particular signature to check the exact attributes in the DNS header, then scan for specific content in the payload.
Traffic analysis - traffic is investigated over time.
- Volume of DNS traffic per IP address. A simple and easy-to-follow method is to check the specific amount of DNS traffic coming from a particular client's IP address.
- Volume of DNS traffic per domain. Another simple and basic method is to check the amount of traffic to a specific domain name. DNS tunneling utilities are usually created to tunnel data using the exact domain name. Thus, all tunneled traffic will refer to this particular domain name.
- The number of hostnames per domain. Usually, DNS tunneling utilities ask for an individual hostname for each query. This has the effect of increasing their number compared to the usual authentic domain name.
- The geographic location of the DNS server. You can check for a lot of DNS traffic directed to geographic areas where you don't offer your services or products.
- The history of a domain. You can examine when an A record (AAAA record) or NS record was created and added to the domain name. This technique is beneficial for detecting domain names used for malicious criminal activities.
How to protect against DNS tunneling attacks
DNS is a critical service; blocking it can be a severe problem. Protecting against a DNS Tunneling attack includes several actions that can help you prevent such an attack.
- It is necessary to closely monitor and keep track of questionable IP addresses and domain names from unknown sources.
- You can configure all internal clients to direct their DNS queries (DNS requests) to an internal DNS server. In this way, you can filter out potentially malicious domains.
- It is also essential to keep an eye out for any suspicious domain names. It is best to monitor DNS traffic constantly. This will also help prevent DNS tunneling attacks.
- Installing a DNS firewall will help detect and stop any hacker intrusions.
- Another good option is a solution that can detect unusual DNS requests and traffic patterns on the DNS server in real time.
Despite the non-obvious use of DNS, DNS tunneling is a severe cyber threat. It can lead to large-scale negative consequences. This is because a cybercriminal can use the tunnel to leak information. In addition, the lack of a direct link between the hacker and the target makes it difficult to try to detect the attacker.
