What is Chargeware?
Chargeware is a specific type of mobile rogue software, that bills your phone number or bank card via the subscriptions to some paid services. It usually tries to mimic some legitimate application available at Google Play or App Store and may even have the claimed functionality. But besides what the developers promise it will do, this app manages to make money for their developers and some other crooks in a very sly way.
Such types of unwanted apps as chargeware have existed for a long time. Its peak spreading was at the edge of the ‘10s, and now they are less active. The main reason for their decline is the serious control over money transactions established by authorities, including money transfers from mobile numbers. Other cybercriminals, whose money channels were compromised, switched to other payment methods - in particular, cryptocurrencies. But chargeware still applies the same tactics as earlier - and changes the names each time the authorities start searching for them.
How does chargeware work?
As it was mentioned, chargeware is an example of rogue programs - the ones which look like and are advertised as legit tools. They sometimes even have a part of the claimed functionality, but their key features work only for their developer or the crooks who spread it. Rogue apps will ask the user to pay for being able to use the advertised potential, saying that all other functions are just a demonstration. However, that’s how it usually works with this sort of unwanted app on the PC - while chargeware generally aims at mobile devices.
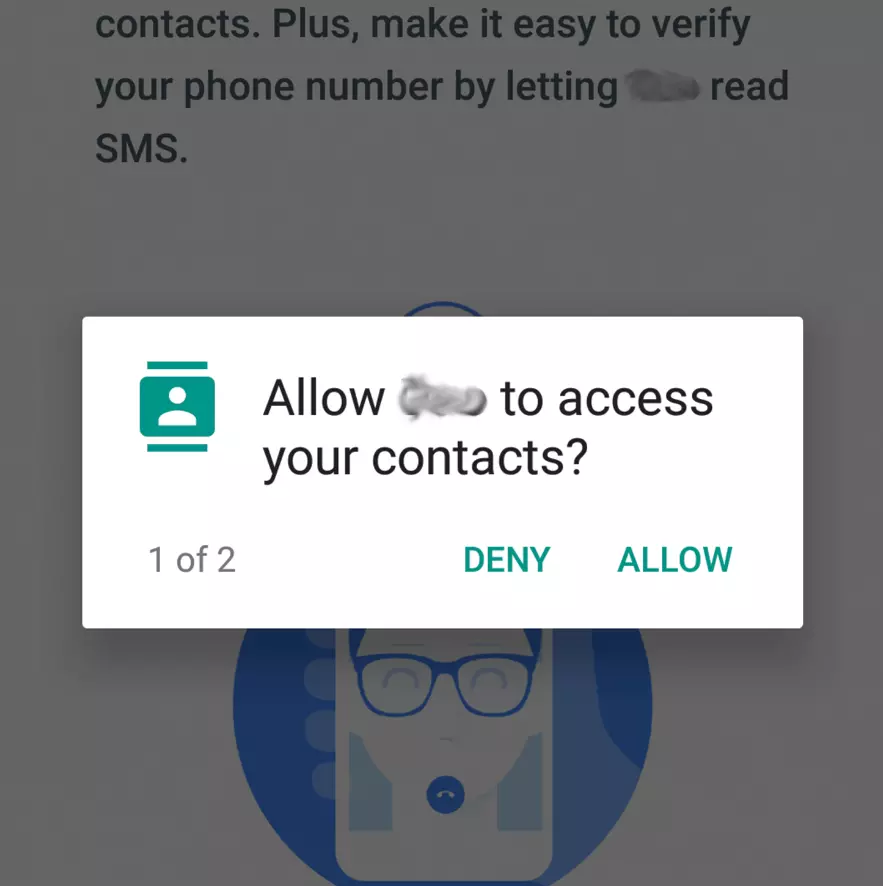
On mobile phones, there are plenty of ways to make the victim pay for something they never wanted to. First of all, most people have one or several bank cards attached to their App Store/Play Store accounts. Users somewhy count this approach as 100% safe, even though these accounts are not secured in any way. Another rare way chargeware works depends upon the ability to subscribe for services by mobile number. Both of them need to have permission to commit in-app purchases or, in the case of mobile number subs, to interact with the phone app.
After gaining these rights, chargeware starts its nasty actions. It may show you different pop-up windows that contain some disguise - the request to show you the details or to download the additional functionality. By pressing the “confirm” button , you automatically agree to the subscription to a paid service. This way, the crooks, on the other side, receive a commission for each subscriber for that scam thing, or even the full sum if they control both crimeware and this “subscription service”.
The problem is that chargeware developers is quite hard to blame and punish, as it is not a fraud in fact. By pressing the confirmation button, the user subscribes to the services of one's own free will - , and all these details are described in the EULA, or somewhere in the app settings, with fine print or in the unobvious place. De jure, everything is legit, and crooks have never forced you to pay for something - but you still have zeros on your mobile number.
Chargeware forms
Like other mobile malware, chargeware is polymorphic as spyware or adware. It generally looks like a genuine tool, and may even have a well-designed page in Google Play. App Store contains way fewer examples of any malicious or untrustworthy apps because of extreme moderation. It can be advertised as a tool for phone call recording, an alternative calendar, the camera app, or whatever you can imagine. As they will still trick you to allow it to perform in-app purchasesand USSD requests, there is no need to have a deep disguise.
Yes, some applications can have a realistic disguise - and even good reviews online. However, their development and distribution are more complex, and some disguise variants will be checked with increased diligence - as these apps pose a potential security concern. However, there are plenty of other ways of spreading such tools - for example, online forums or warez sites that offer hacked and non-approved programs for everyone. Be very careful when using such programs, even in case someone recommends them to you.
An obsolete form of chargeware that was active before smartphones usually looked like an app for convenient files downloading from the Internet. In particular, on push-button telephones, these tools were pervasive. Operating systems of that time usually asked the user several times about their confirmation for the downloading, even when you were using the standard browser. People used to click through these questions, as nothing was informative. Meanwhile, the mentioned tools were showing the requests to subscribe to a certain kind of mobile service among these windows, and people were applying him having no clue about what is happening.
How dangerous is chargeware?
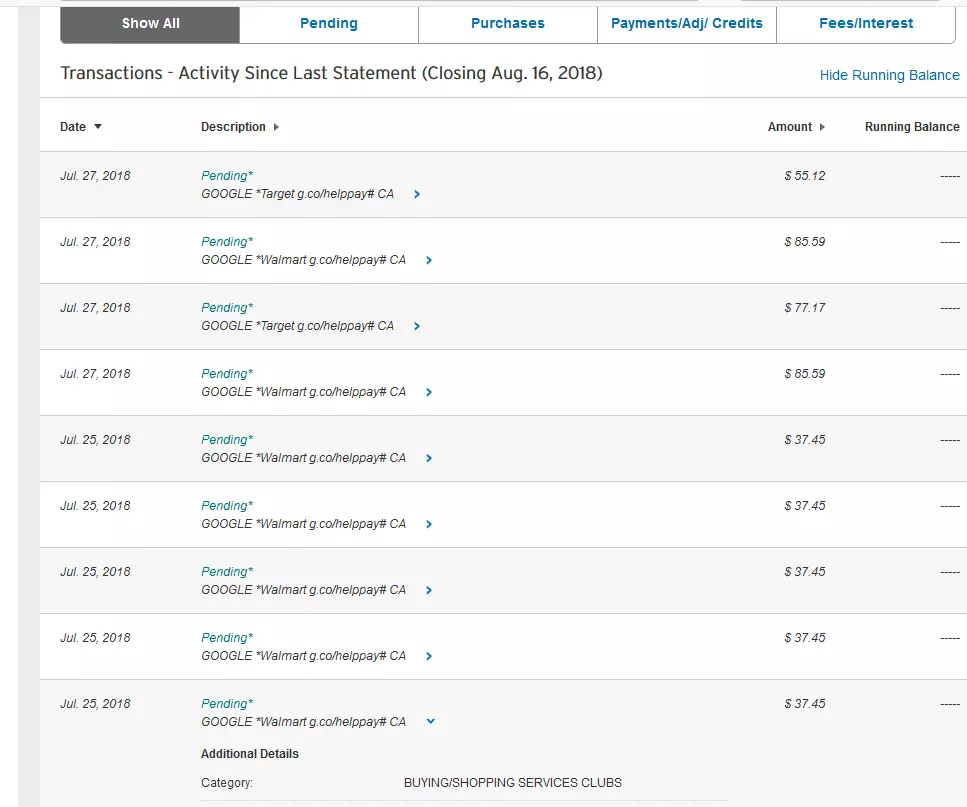
Based on the paragraphs above, you may have concluded that the only danger of chargeware is a money loss. Sure, subscriptions rarely cost a lot per month, and malicious ones try to keep up with that image - to call less suspicion. When it comes to mobile numbers, people never keep enormous sums there, especially these days - with the spreading of prepaid plans. And having a particular sum on the account makes the user even more paranoid about how they are spending. Dubious transactions or unexpectedly fast draining may be missed ones, but repetitive cases will cause questions.
The critical problem of this situation that can look not so serious is that chargeware and the subscriptions it makes for you are pretty hard to remove. While regular apps and subscriptions can be deleted or stopped in a few clicks, chargeware and related things will make you mad. You may notice that the exact application refuses to delete, and the service has a dozen terms and conditions where it cannot be canceled. Once again - juridically, everything is legal, but that does not make the crooks less of a swindler in your eyes.
However, that is not the only danger of this situation. As we have mentioned, the chargeware tries to mimic a legit app to get permission to do different things on your phone. And they may not stop at just the ability to bill your attached cards and send USSD queries. Someone on the Darknet will give a pretty big sum for a database with full information about the users of such apps. Email address, name, phone number, address, and frequent locations, along with the list of applications installed and the detailed info on your device - that’s what spyware usually gathers. And the only thing that divides it from such non-excuse actions is the permission to access certain areas of your phone. Chargeware got them once if it already runs and has subscribed you to several things you did not ask for. So why not try to do that once again? That’s a rhetorical question.
Chargeware examples
The issue of describing the chargeware cases is that its examples usually never had a great scale. It was popular generally by the number of samples rather than by the effectiveness of a spreading campaign or a great disguise of certain examples. Steadily popular, it acted without serious spikes in activity and never had any outstanding examples. Still, several campaigns were known around the entire globe. In the early ‘10s, the activity of this malware kind reached its peak and then started decreasing slowly. It has likely reached a plateau in the last three years and has had no significant spikes.
The most significant pandemic of chargeware happened around 2013 when multiple countries around the world suffered a great spike in the number of victims. Mostly the campaign touched European countries, such as France, the UK, and Spain. The chosen disguises were legal tools that had nothing to raise suspicion, and in those times, people were generally unaware of the malware on mobile devices (mostly Android phones). Such an approach had such massive results that in some countries, chargeware was as spread as adware - and the latter is considered as widespread as a common cold.
How to protect yourself?
First advice to make yourself away from this kind of unwanted software is to use only trustworthy programs. The ones that know the price of their image will never do such sly things. Moreover, programs that ask for access to the phone book and make calls should have a reason to do so - otherwise, these functions may be used for an ill purpose. Still, there is no guarantee that the one who needs them will not misuse these privileges - so the best way to ensure the quality is to read the reviews.
Another way to avoid such frauds is to check up on the requests you confirm in the app. It may be bothersome to read each notification diligently, but it is recommended to do that, at least for programs that can be risky. Apps you’ve got not from the official source, tools made by a handyman you met on an online forum - you cannot be sure about their actions. Officials who moderate the app distribution marketplaces exist not just to make the developers’ life harder - they check up on these programs for benevolence. And having no approval is a security concern.
To mitigate your risks, creating a special banking card, possibly the online one, that will solely be used for subscriptions, and in-app purchases are recommended. Top up that card only a day before the services you pay for a bill, and with the sum roughly enough. That card will act as a security layer that will not give the fraudsters a chance to suddenly bill you, as most of the time, the card will be empty. Overall, having such a proxy card is a good idea for shopping online - especially when you often use marketplaces you’re not sure about.
Aside from your attentiveness and, in some cases, paranoid doubt, it is possible to use antivirus - an app that will do everything for you. Among mobile antiviruses, we can recommend you the Gridinsoft Trojan Scanner for Android - a free app that inherited the qualities of our other products – GridinSoft Anti-Malware and GridinSoft Trojan Killer. Using the security solution, you will be free from paying excessive attention to the messages apps send you. When it detects something suspicious, you will receive a report, and the detected thing will be blocked.