
What is Doxing?
April 03, 2025
Doxing (or doxxing) is a type of online harassment that involves revealing someone's personal information, such as their real name, phone number, address, job, or other identifying information, and publicly disclosing it, usually online. Doxing occurs without the victim's consent with the intent to disclose information intended to preserve privacy.
The term "doxing" comes from the "documents". The hacker culture of the 1990s shortened the term to "docs" and then "dox" where "dropping dox" meant collecting personal documents or information (such as someone's physical address) and posting it online. The hacker collective Anonymous helped popularize the term.
Today, doxing is publishing someone else's information online without permission. It can be used to reveal the real person behind an anonymous username and that person's real identity online. Some doxxing attacks are based on stalking or retaliation. In contrast, others target people who anonymously post bigoted comments online or are caught on a video promoting such beliefs.
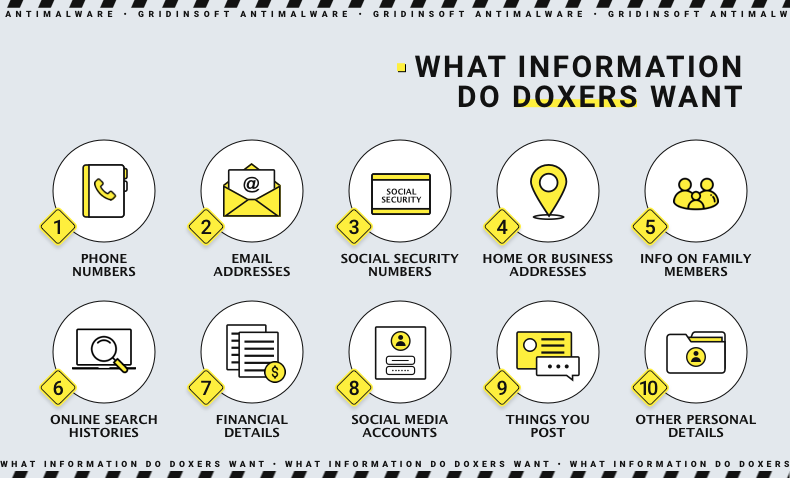
Although the concept is decades old, doxxing is still relevant. However, it can be hazardous, especially as it becomes increasingly popular. Once someone's physical address, place of work, phone number, email, or other information becomes available, they can become an easy target. Doxing attacks range from relatively innocuous, such as fake email subscriptions or pizza delivery, too much more dangerous, such as stalking a person's family or employer, swatting, identity theft, threats, and other forms of cyberbullying, or even personal presence or harassment.
Doxing Methods
Doxers collect "breadcrumbs" of small pieces of information about someone scattered all over the Internet and then add them up to reveal the real person behind the alias. These "breadcrumbs" can include the target's name, physical address, e-mail address, phone number, and more. Doxers can also buy and sell personal information on the Darknet. A doxer can combine small pieces of information to reveal the real person behind the alias. Small pieces of information can be combined to reveal the real person behind the alias.
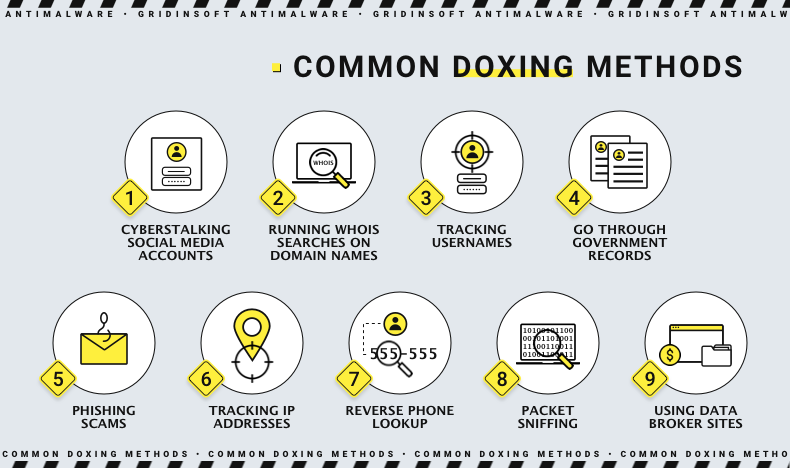
Traditionally, doxing started with online arguments and then moved on to one person digging up information about an opponent. Recently, doxxing has become a popular tool in the culture wars, with activists doxxing those who hold opposing ideologies. As a result, many celebrities and journalists have been doxxed, causing them to suffer Internet mobs and even death threats. Tracking personal information is an essential part of doxing. And while many people think of the Internet as anonymous, that's not true. There are many ways you can be identified online.
Types of Doxing
Hackers use many methods to gather information about their targets. They can look at your social media profiles, buy data from data brokers, use phishing campaigns, use your IP address, and even intercept Internet traffic.
IP/ISP Doxing
IP doxxing (or ISP doxing) is when doxers get your IP address linked to your physical location. The doxer then uses social engineering techniques to trick your Internet Service Provider (ISP) into revealing more information about you. Using a call spoofing application to disguise your phone number as that of your ISP, the doxer calls the ISP and pretends to be a customer service representative. Then, they can use your IP address to ask for the rest of your customer's information, which can include:
- Your full name
- Phone number
- Date of birth
- Email address
- ISP account number
- Physical address
- Social security number
It takes a few steps, manipulation, and a trusting internet service provider employee. However, when such tech support scams work, a doxer can get much personal information with a single phone call.
Social Media Doxing
Social media doxing involves collecting personal information from your social media accounts. This data may include your location, where you work, your friends and photos, your likes and dislikes, places you've visited, names of your family members, names of your pets, and more. Some of this information may even give doxers answers to your control questions, which they can use to hack into your other online accounts.
You should make your social media accounts private. Create different usernames and passwords for each service if you use online social platforms such as Instagram, Reddit, 4Chan, YouTube, and others. If you use the same username on multiple platforms, a doxer can link your accounts to get a detailed picture of your activity. And always be careful about disclosing personal information.
Data Broker Doxing
Some doxers buy personal information about their targets from data brokers, companies that collect information about people and sell it for profit. Many data brokers sell information to advertisers. However, several people's search sites also sell complete personal information to anyone. Data brokers collect their information from public records (marriage licenses, government records, voter logs), customer loyalty cards (your online and offline buying behavior), online search history (anything you search, read or download), and other sources and data brokers.
Sniffing
Sniffing is when someone intercepts Internet traffic on its way from sender to receiver. Internet traffic is sent in small packets called data packets. A sniffer is a software or tool that can collect these packets and read the data they contain. A sniffer can use sniffing to collect someone's Internet traffic and search it for personal data.
WHOIS Lookups
WHOIS is a service that allows anyone to find out information about the person who owns an Internet domain. You can make your WHOIS information private, but if you forget, your name, address, phone number, and e-mail address will be available to anyone looking for your domain name.
Phishing
Phishing is using fraudulent messages to trick victims into revealing sensitive personal information. Additionally, phishers can use targeted phishing attacks against specific individuals to gather information about potential victims. Although the ultimate goal of many phishing attacks is identity theft, the information obtained can just as quickly be used in attacks.
Swatting
Swatting is when someone calls the police to report a severe emergency, such as a bomb threat or hostage situation, to their victim's address. A SWAT team rides to the scene, assuming the emergency is real, and surprises the victim. More often than not, the streamers become the targets of a squawk, and the attackers thus seek to interrupt their live broadcasts.
One tragic example of lapping involves a teenage gamer who was shot because of a $1.50 bet he made on a Call of Duty game. He recruited a known scammer, who then reported a hostage situation at his opponent's house, but with an old address where the alleged victim no longer lived. When the heavily armed police arrived, they shot and killed the unarmed 28-year-old resident when he opened the door.
Swatting is a relatively recent phenomenon, but it is becoming increasingly dangerous. Many cities don't know how to defend themselves against swatting, but Seattle, Washington, has developed a good tactic. They've run a special anti-slamming registry so people worried about being intercepted can put their addresses in a database. Then, if a call comes in, the police check the registry before showing up at the address. This means they can be much more careful and potentially avoid hurting or killing someone.
Doxing Laws: Is Doxing Illegal?
In the absence of specific anti-doxing laws, the legality of doxing is usually determined on a case-by-case basis. Although it is rarely illegal to collect or publish publicly available information, there are other crimes for which doxers may be prosecuted, depending on the nature of the case. These include stalking, harassment, identity theft, or incitement to violence. In the United States, the Interstate Communications Act and the Harassment Statute may apply to dox, depending on the details of the particular case. There are also no laws prohibiting doxing, although perpetrators may be prosecuted under other laws.
Can You Go to Jail For Doxing?
You can go to jail for doxxing or swatting someone. The Call mentioned above of Duty flyboy was caught, charged with 52 felony counts of making phony calls and threats (including an earlier phony bomb threat to the FBI), and sentenced to 20 years in prison.
Examples of Doxing
There have been some high-profile examples of doxing over the years, including some very recent instances:
- Skai Jackson, 2020: Teenage actress Skai Jackson has been exposing racist messages on social media by re-posting them with the names and handles of the posters, as well as tagging their employers or schools. She stated that she wants these cyberbullies to experience real-world consequences for their behavior.
- Jackson Cosko, 2018 Former government intern Jackson Cosko, 27, was arrested after publishing the home address and private telephone numbers of Senator Lindsey Graham on his Wikipedia page.
- Kyle Quinn, 2017: University professor Kyle Quinn was doxed by online vigilantes. But it turned out to be a case of mistaken identity. Pictures of a white nationalist rally in Charlottesville were shared online, and the teacher was wrongfully identified as one of the marchers. Digital detectives launched a harassment campaign and vowed to get him fired until the mistake was revealed.
How to Prevent Doxing
Doxing can be traumatic. To prevent doxing, minimize the information available about you online. Here are some ways to hide your IP address, protect your social media accounts, and remain anonymous online.
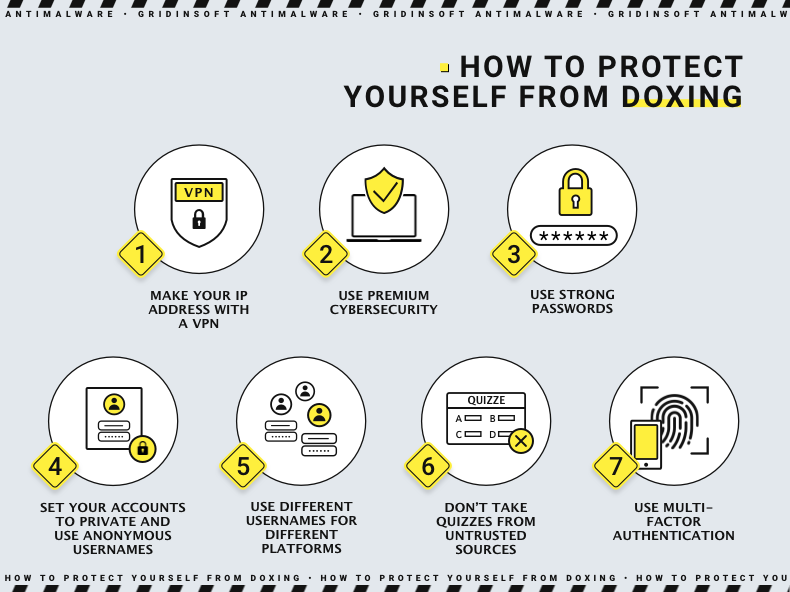
- Use a VPN or proxy to protect your IP address. You can easily hide your IP address using a VPN or proxy server to access the Internet. These tools allow you to connect to a secure server before connecting to the public Internet. This means that anyone trying to find your IP address will only see the IP address of the VPN or proxy server, and yours will remain hidden.
- Logging into many different sites using just your Google or Facebook account can make you vulnerable to a data breach. If your account password becomes known, a hacker can gain access to all of the sites you have linked together. This makes it easy for a hacker to get your personal information, making it much harder for you to block your accounts.
- Keep social media profiles private. Our social media profiles contain much information about us: our general location (sometimes even our full address), work history, date of birth, friends, family members, photos, interests, and so on. Having so much information in the public domain makes it easy to doxxing. You should hide your social media accounts even if you think you have no enemies. You should also tighten your privacy settings on Instagram and any other social media you use.
- Use pseudonyms on online forums. If you use Reddit or other online forums, use an alias to remain anonymous. Never use your real name as your username or use any personal information in your nickname. When creating new accounts, choose a unique username for each service you use. If you reuse descriptors between sites, Docker can connect your accounts and extract clues to your identity from them.
- Request removal of your information online. Data brokers collect and sell massive amounts of personal data. These data brokers store vast files, including your browsing history, online and offline purchases, medical, financial, criminal, and more. And when a data breach inevitably occurs, like the Equifax leak, your information can be exposed to the world.
- If your data hits the darknet, it will likely stay forever. You can contact the data brokers individually to ask them to remove you from their database. However, while they are legally obligated to comply, the process can be time-consuming. And it's almost impossible to identify every data broker who has your data.
- If you have been doxed, you will know as soon as your information is publicly available. People you know will likely let you know if you haven't seen the data. Depending on the information released, you may be harassed through social media, phone calls, emails, or even in person.
- If you start receiving threatening messages, hide all your accounts. Check to see if your Google account has been hacked, and ensure your Gmail account is protected. And while it's also helpful to know if your personal information is being sold on the darknet, it's not easy to get there without special software such as Tor.
🟥 If you have been doxed or think someone may be doxing you, act quickly to stop the spread of your personal information. Here are a few steps you can take if you think you've been doxed:
- 1️⃣ Document the evidence. Take screenshots of everything if you need to report it to the police.
- 2️⃣ Contact the tech support of the platform that hosts your information and report the doxing. For example, sites like
Facebook and Twitter have terms of service agreements that prohibit doxing, and they should respond to your request and suspend the
doxer(s) account.
- 3️⃣ Report cybercrime - doxing is often cybercrime - to the appropriate authorities in your area.
- 4️⃣ Hide your accounts. Create new strong passwords for your accounts and store them securely in one of your password
managers. Protect your accounts with two-factor authentication and tighten your privacy settings across all your accounts.
- 5️⃣ Ask a family or friend member for support. Doxing can be emotionally challenging. Ask someone to help you figure out
the problem so you don't have to deal with it yourself.
- 6️⃣ Changing your number. Depending on what information has been disclosed, you may want to consider changing your phone number, username, or other personal data where possible.
