PUADlManager:Win32/Snackarcin is a detection of Microsoft Defender that flags an unwanted program that is capable of downloading other unwanted programs. This, in turn, makes it pretty dangerous, at least from the user experience perspective. Ignoring it can end up with the system being cluttered with unwanted programs similar to other unwanted applications and adware infections.
Threat Summary
| Detection Name | PUADlManager:Win32/Snackarcin |
| Threat Type | Potentially Unwanted Application (PUA), Downloader, Bundleware |
| Detection Source | Microsoft Defender Antivirus |
| Primary Function | Downloads and installs additional unwanted programs without user consent |
| Common Sources | Modified Minecraft mods, system optimizers, screen time tools, visual tweakers |
| Installed Payloads | Tesla Browser, PC App Store, 7-zip, various adware and PUAs |
| System Impact | Browser hijacking, unwanted notifications, system slowdown, privacy risks |
| Risk Level | Medium (can escalate to high with additional malware downloads) |
Unwanted programs like Snackarcin are usually less dangerous than trojan malware, though I wouldn’t recommend ignoring them. Since it can deploy other unwanted programs, it all gains cumulative effect, turning the system into a mess. Moreover, apps that this PUA installs may install other unwanted programs on their own, proliferating like bunnies and creating a cascade of browser hijackers and system modifications.
What is PUADlManager:Win32/Snackarcin?
PUADLManager:Win32/Snackarcin is a detection name that Microsoft Defender uses to flag a downloader of unwanted programs. Usually, it is an installer of a program that contains a specific code, which makes it connect to a remote server and download other programs. The abbreviation “PUADl” at the beginning of the detection name is, in fact, self-explanatory: Potentially Unwanted Program Downloading Manager. This type of threat falls into the broader category of malware threats that security software actively monitors.
Among other detections of this type, Snackarcin stands out by the type of a program that carries the said code. According to the user reports, this detection appears on mods or mod engines for Minecraft, downloaded from a third party website. Although completely safe by design, they were modified by a person who uploaded it. This, exactly, is what Microsoft Defender is not happy about. The range of the unwanted programs it can install is vast, I will show my tests later on.
The said mods and mod engines are not the only possible program type that backs the PUADlManager:Win32/Snackarcin. Review of the actual samples show quite a few shady utilities that contain bundler code. Visual tweakers for Windows, screen time control tools, system optimizers – they always were less than trustworthy. These types of programs often serve as delivery mechanisms for more serious threats, similar to other software bundling schemes we’ve analyzed.
PUADlManager:Win32/Snackarcin Runtime Analysis
To have a better understanding of what Snackarcin is, I run a sample on a virtual machine. It appears to have only a few visible signs that something phishy is going on: the installer had no “usual” windows, and asked to install 7-zip at the end. However, shortly after, the obvious issues appeared.
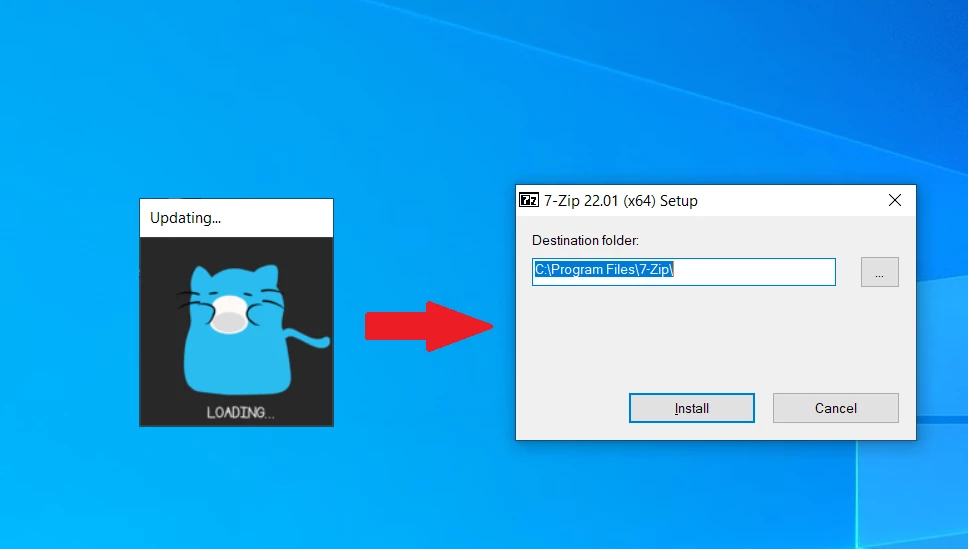
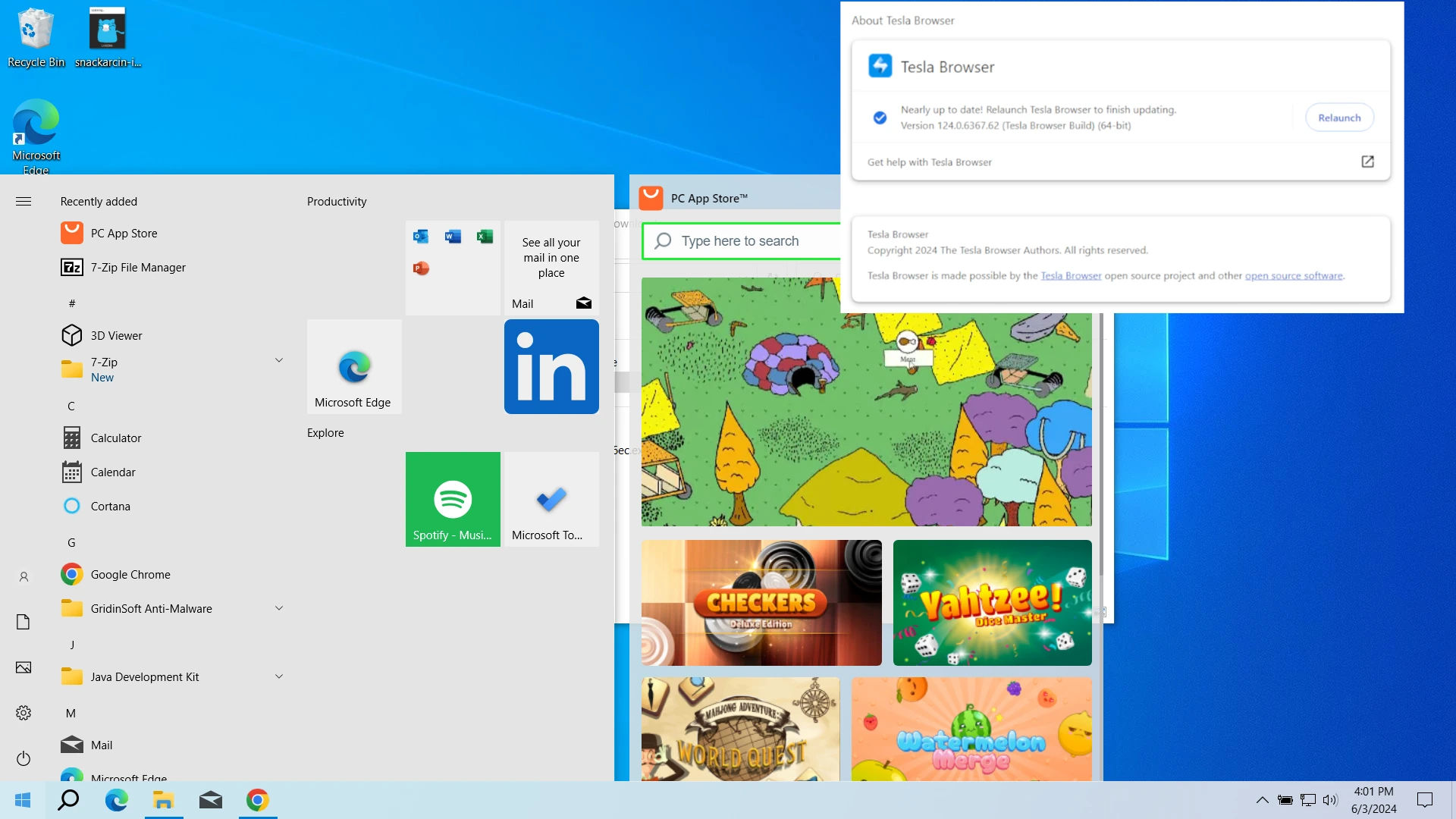
Without a single notification from the installer, it injected Tesla Browser, a known adware-like rogue browser, and a PC App Store. The latter tries to look like what it sounds, but is in fact akin to adware, that adds promotions to system windows. Both of them are particularly obtrusive in their presence: starting with the system, notifications that pop on top of all apps, the default browser changed to Tesla, and so on. This behavior is typical of spyware-like programs and adware removal scenarios. This, however, is not the complete list of unpleasant things Snackarcin is capable of.
To target the bundled programs, PUADLManager:Win32/Snackarcin collects basic system information. This is represented in its activity logs: the installer accesses the registry keys and system config files:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MUI\UILanguages\en-US
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Nls\CustomLocale
C:\Windows\System32\WinTypes.dll
This provides Snackarcin with the information about the system version and location, which most likely defines what kind of unwanted apps will it install. Having this data, the bundler connects to the command server (C2) and retrieves the PUAs. C2 addresses are usually built into each sample.
TCP 20.99.186.246:443
TCP 192.229.211.108:80
TCP 23.216.147.64:443
One thing that looks disturbing to me is the occasional usage of command line calls to svchost.exe and wuapihost.exe. These two system processes are capable of hosting the execution of other apps, and, what’s more important, DLLs. For that reason, they are often exploited by dropper malware, particularly for launching injected malware that has a form of a DLL file. Considering the aforementioned networking behavior, nothing stops Snackarcin from downloading and launching more dangerous threats through these legitimate Windows processes.
C:\Windows\System32\wuapihost.exe -Embedding
C:\Windows\System32\svchost.exe
Impact on System Performance and Security
PUADlManager:Win32/Snackarcin creates multiple negative impacts on infected systems beyond just installing unwanted programs. The bundled applications consume system resources, slow down startup times, and create persistent background processes that affect overall performance. Users often report significant browser slowdowns, unexpected pop-ups, and changed homepage settings similar to other virus-related attacks.
From a security perspective, Snackarcin creates vulnerabilities by establishing network connections to remote servers and potentially downloading additional payloads. The ability to execute system processes like svchost.exe and wuapihost.exe means it could theoretically be used to deploy more serious threats including InfoStealer malware or ransomware variants.
The networking behavior also raises privacy concerns, as the software can potentially collect system information, installed programs lists, and user behavior data to send back to command servers. This data collection often happens without explicit user consent and may violate privacy regulations in many jurisdictions.
Prevention and Best Practices
Preventing PUADlManager:Win32/Snackarcin infections requires careful attention to software sources and installation practices. Always download programs from official websites or reputable software repositories. Gaming modifications, in particular, should come from trusted modding communities with established reputations, as gaming-related PUAs are increasingly common.
When installing any software, especially system utilities or gaming modifications, read installation prompts carefully and opt for custom installation when available. Many bundlers hide their payload installations in “quick” or “recommended” installation options. Enable Windows Defender real-time protection and keep your security software updated to catch PUA detections before installation completes.
Be particularly cautious of software that promises system optimization, PC cleaning, or performance enhancement. These categories frequently contain potentially unwanted bundlers and serve as common distribution vectors for threats like Snackarcin. If you encounter fake virus alerts or suspicious system warnings, they may be attempting to trick you into installing similar PUA threats.
How to remove PUADlManager:Win32/Snackarcin?
I recommend using GridinSoft Anti-Malware to remove PUADLManager:Win32/Snackarcin. As you could have seen from the analysis above, it does quite a lot of changes in the system, and may install pretty much any other programs or even malware. That’s why a dedicated malware removal utility is pretty much a must.
Download and install GridinSoft Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.

After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click “Advanced mode” and see the options in the drop-down menus. You can also see extended information about each detection – malware type, effects and potential source of infection.

Click “Clean Now” to start the removal process.

Additional Manual Cleanup Steps
After running GridinSoft Anti-Malware, perform these additional cleanup steps to ensure complete removal of PUADlManager:Win32/Snackarcin components:
1. Check and Reset Browser Settings: If Tesla Browser or other unwanted browsers were installed, reset your default browser settings. Remove any suspicious browser extensions and restore your preferred homepage and search engine using the browser settings options or the Reset Browser Settings in the GridinSoft Anti-Malware.
2. Review Installed Programs: Open Windows Settings > Apps & Features and look for recently installed programs you don’t recognize, especially PC App Store, Tesla Browser, or suspicious system optimization tools. Uninstall any unwanted applications found during this review.
3. Clear Temporary Files: Use Windows Disk Cleanup or a third-party cleaner to remove temporary files and cached data that may contain remnants of the unwanted programs. This helps ensure no leftover components remain on your system.
4. Scan with Windows Defender: Run a full system scan with Windows Defender as a secondary check. While GridinSoft Anti-Malware is more comprehensive for PUA removal, Windows Defender may catch any remaining components or related threats.
Conclusion
PUADlManager:Win32/Snackarcin represents a significant threat to system security and user experience, despite being classified as “potentially unwanted” rather than malicious malware. Its ability to download and install multiple unwanted programs creates a cascade effect that can severely compromise system performance and security.
The key to protection lies in prevention: download software only from trusted sources, avoid third-party mod repositories, and maintain updated security software with real-time protection enabled. When installing any software, especially system utilities or gaming modifications, always choose custom installation options and read prompts carefully.
If you’ve encountered this threat, prompt removal is essential. Use comprehensive security tools like GridinSoft Anti-Malware rather than relying solely on Windows Defender, as PUA threats often require specialized detection and removal capabilities.
For additional protection against similar threats, consider reading our guides on detecting OfferCore bundlers, understanding InstallCore threats, and recognizing online scam patterns. Stay informed about system optimization scams and maintain good cybersecurity hygiene to protect your system from future infections.
Frequently Asked Questions (FAQ)
What does PUADlManager:Win32/Snackarcin mean?
PUADlManager:Win32/Snackarcin is Microsoft Defender’s detection name for a potentially unwanted application that downloads and installs other unwanted programs. “PUADl” stands for “Potentially Unwanted Application Download Manager,” indicating its primary function as a software bundler that connects to remote servers to retrieve additional programs without explicit user consent.
Is PUADlManager:Win32/Snackarcin dangerous?
While not as immediately dangerous as ransomware or banking trojans, PUADlManager:Win32/Snackarcin poses significant risks to system security and user privacy. It can install browser hijackers, adware, and other unwanted applications that compromise system performance. More concerning is its ability to execute system processes that could potentially be exploited to install more serious malware in the future.
How did PUADlManager:Win32/Snackarcin get on my computer?
Most users encounter PUADlManager:Win32/Snackarcin through modified Minecraft mods downloaded from third-party websites, bundled system optimization tools, or fake PC cleaning utilities. The threat often comes disguised as legitimate software but contains additional code that downloads unwanted programs after installation. It may also arrive through software bundling, where legitimate programs are packaged with unwanted additions.
Can I ignore the PUADlManager:Win32/Snackarcin detection?
No, you should not ignore this detection. While it may seem less threatening than traditional malware, PUADlManager:Win32/Snackarcin can significantly degrade system performance and create security vulnerabilities. The unwanted programs it installs often lead to browser hijacking, persistent advertisements, and potential privacy breaches. Additionally, its network connectivity capabilities mean it could potentially download more serious threats.
Will Windows Defender remove PUADlManager:Win32/Snackarcin automatically?
Windows Defender will detect and quarantine PUADlManager:Win32/Snackarcin, but it may not remove all associated components and installed programs. The bundler often installs multiple applications before detection occurs, requiring manual cleanup or specialized anti-malware tools to completely remove all unwanted components. A comprehensive scan with dedicated security software is recommended for complete removal.
What programs does PUADlManager:Win32/Snackarcin typically install?
Common programs installed by PUADlManager:Win32/Snackarcin include Tesla Browser (an adware-laden browser), PC App Store (promotional software), 7-zip (legitimate but used as cover), and various system optimization tools. The specific programs may vary based on the command server configuration and your system’s characteristics, but they typically focus on browser modification and system advertising.
How can I prevent future PUADlManager:Win32/Snackarcin infections?
Prevent future infections by downloading software only from official sources, avoiding third-party mod repositories, reading installation prompts carefully, and choosing custom installation options when available. Keep Windows Defender enabled with real-time protection, avoid system optimization utilities from unknown publishers, and maintain updated security software that can detect PUA threats before they install.