LOBSHOT, a recently-detected malware family, appears to be a new strong player in the malware market. Carrying a combination of backdoor and spyware functionality, it uses novice spreading ways that make it more effective. Its ability to provide Hidden VNC connections may be a go-to point for numerous cybercriminals. Let’s analyse this malware and see, is it really that dangerous and how to counteract it.
Short overview
LOBSHOT is a novice malware debuted around mid-2022. By its capabilities, it is an advanced stealer malware, accompanied by backdoor functionality. Being primarily a stealer, it generally aims at crypto wallets, particularly ones present as browser extensions. It does not seek for any other sensitive data, i.e. it is a pure crypto stealer. That is quite unusual for malicious programs of that kind, as they are commonly capable of stealing some other stuff, like login credentials, email addresses or so. Though such a narrow specialisation allows malware to be much more stealthy. hVNC is another unusual, yet not new feature present in this malware.
Another interesting detail about LOBSHOT is its possible association with TA505 – cybercrime gang that is best known for its Cl0p ransomware. The key clue of LOBSHOT belonging to TA505 is the use of the threat actor’s infrastructure as C2 servers for this malware. Despite being generally oriented towards attacks on corporations and governments, crooks now opted for clearly user-oriented malware. Such a step is unclear, as attacks on single users are not trending and are rather on their descending. Still, diversification is never a bad idea, and spreading malware to users rather than companies may be pretty easy to accomplish, especially considering TA505’s connections with Amadey dropper.
Distribution
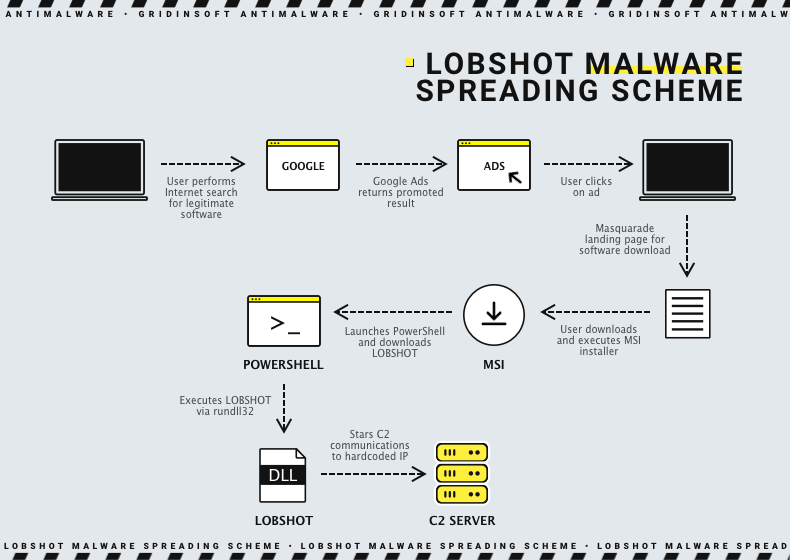
Have I already told you that LOBSHOT is mostly about peculiarities? Unusual masters and narrow functionality are not the only things that make analysts wonder. The malware generally bears on malicious advertisements in Google Ads – a pretty rare approach. It supposes creating a landing site that resembles a downloading page of a well-known free software vendor. Then, crooks purchase a promotion from Google, posting it to search results. Because of plentiful SEO spam used on that counterfeit, it is getting boosted to the top of search results. Users who trust either Google and its advertisements will blindly click on these promoted traps and download malware.

It is worth noting that it may be only a temporary decision. As Google continues to develop anti-fraud protection for its advertisement services, the chance to do such a trick in future may cease to exist. In that case, more “classic” ways may become an option – such as phishing emails or cracked software. Spreading via downloader malware may also be an option: as we said, TA505, who controls LOBSHOT, has a long-term relationship with crooks that stand behind Amadey dropper.
LOBSHOT threat analysis
Currently, analysts located ~500 samples of LOBSHOT circulating in the wild. Malware may have the form of a 32-bit DLL or executable file. Most probably, that depends on the way it is delivered: DLL form is more convenient for launching through PS scripts or dropper malware, while .exe is more convenient for a stand-alone start. The latter, actually, is a typical case for spreading via Google Ads.
Launch
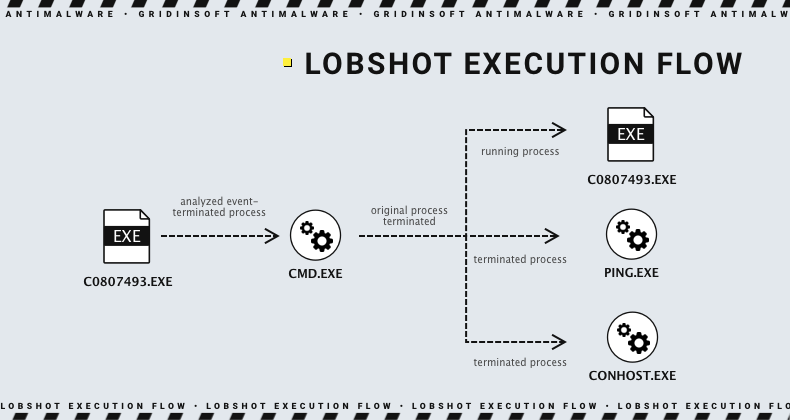
Regardless of the way it was launched, LOBSHOT starts by creating its copy in the C:\ProgramData folder. Then, using explorer.exe, the malware launches this copy, terminates its original process and removes the original file – a pretty common detection evasion trick. After that, the malware starts providing itself persistence for further operations, using Run key in the system registry. A randomly-named entry that refers to the new malware location is spawned in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. It allows malware to start at the logon of this particular user – which is not pretty common. Malware generally tries to be user-agnostic when it comes to gaining persistence, and tries to use HKEY_LOCAL_MACHINE registry hive.
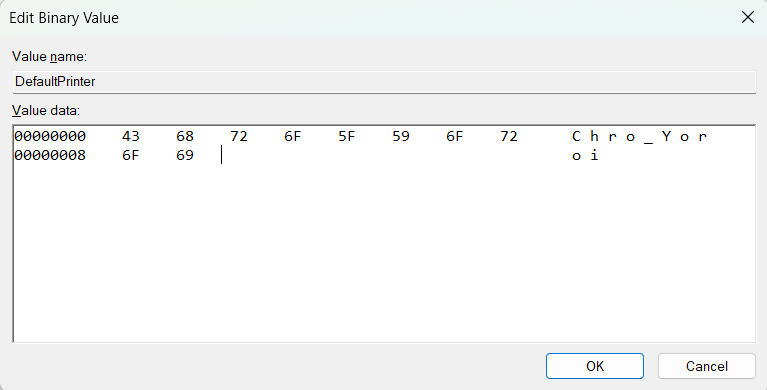
One more action that the stealer does with the registry is a checkup of Software\Microsoft\Windows NT\CurrentVersion\Devices key. LOBSHOT uses the DefaultPrinter value in this key as a check-in point by adding the specific string (134a1160) to that value. Other malware usually rely on the system fingerprint to understand if it was infected earlier, or mutex – to prevent the second instance of malware from launching. It is yet another unusual, but effective decision.
Anti-analysis features
Actually, this malware includes a couple of anti-detection features inside the initial execution flow. Establishing persistence through an unusual registry key is a possible way to evade anti-malware software attention. However, not all of them pay attention to registry alterations and prefer behavioural analysis. For that case, LOBSHOT has another couple of tricks.
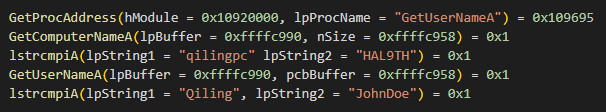
Since malware generally aims at single users, it was obvious that the most often antivirus software it may encounter is Microsoft Defender. Featuring a specific testing environment, it is capable of locating and weeding out even complicated malware. This environment, however, has a couple of properties that allow malware to uncover its presence. A combination of JohnDoe username and HAL9TH system name forces LOBSHOT to suspend execution. This practice is pretty rare and is met only in two widespread malware families – Arkei and Vidar stealers.
Two other features are quite common, though still effective. Dynamic API resolution supposes slower, but less predictable execution flow. Malware resolves the names of Windows API calls on run rather than having them ready to go at the moment of execution. This is accompanied by string encryption: they are XOR-encrypted with the key added at the malware compilation. Despite being known to anti-malware engines, these tricks are not counted as malicious activity, since legit apps may use them as well.
Stealer functionality
As I mentioned above, LOBSHOT is a pure crypto stealer malware, i.e. its sole target is credentials to cryptocurrency wallets. It particularly targets wallet extensions available for Firefox, Edge and Chrome browsers. The malware starts scanning for extensions (by their IDs) and their files right after establishing persistence. Overall, there are 5 Firefox, 9 Edge and 32 Chrome extensions hunted by LOBSHOT.
List of attacked extensions:
Chrome
Yoroi, Binance Wallet, TronLink, Brave Wallet, Nifty Wallet, Guarda, MetaMask, Equal, Math Wallet, Jaxx Liberty, Coinbase Wallet, BitApp, iWallet, Ronin Wallet, Wombat, Coin98, Oxygen, Phantom, MyEtherWallet, Station, GuildWallet, BOLT X, Saturn Wallet, Harmony, EVER, Pali Wallet, Liquality Wallet, Nami, MultiversX DeFi Wallet, XDEFI Wallet, KardiaChain Wallet.
Firefox
Yoroi, TronLink, MetaMask, Ronin Wallet, Phantom.
Edge
Glow, Ronin Wallet, BDLT Wallet, OneKey, MetaWallet, Station Wallet, Math Wallet, Yoroi, MetaMask
When meeting a match in extensions, malware edits the aforementioned DefalutPrinter value, adding the string that represents the located extension. It follows the naming convention of “Browsername_Extension”. For example, if malware finds MetaMask plugin in Chrome, it will add a Chrome_MetaMask string to the value.
Before communicating with the C2 server, LOBSHOT also gathers some information about the system it is running in. It will only look noteworthy if we remember that malware offers hidden VNC capabilities. The list of gathered data is as follows:
- Windows version and edition;
- Host computer name and username;
- Number of processes and the result of VM-related processes checkup;
- ID of the malware process and parent process of the malware;
- Machine’s GUID;
- Display resolution, DPI and device model;
- Handles to the windows and desktop objects.
Two last items are pretty useful for tricky approaches to banking fraud. Instead of using leaked credentials on their machines, hackers can do the same using hVNC service. However, some sites feature security systems that can be triggered with unusual screen resolution/DPI/system setup. Stolen handles and display data allow hackers to spoof these parameters, circumventing security solutions. There even was an entire Darknet market that was offering such a data for sale. Law enforcement took care of it in early April 2023.
C2 communication
After gathering basic information about the system, LOBSHOT initiates a connection to the C2 server. Sample commonly carries a single IP address and port info, and sends POST requests to the server every 5 seconds. The initial request package contains only hardcoded information about the exact malware variant.
Then, after succeeding with the initial connection, the malware starts sending the server all the data it gathered about the system. In return, it may receive shutdown commands, requests for hVNC connections and also information about the alternative C2 addresses. The latter is written into the Video value of Software\Microsoft\Windows NT\CurrentVersion\Devices key. That is another strange moment of communication, as malware masters usually apply other ways to notify the bots about new C&C IP addresses.
LOBSHOT hVNC feature
Obviously, the main, distinctive feature of LOBSHOT stealer is its ability to provide Virtual Network Computing connection. Actually, it creates a hidden one – by playing with certain system calls. As a result, the user of an infected PC will have no clue that someone performs malicious actions in their system, and can even use it in a regular manner.
Malware creates a hidden desktop by calling the CreateDesktopW function. Simultaneously, it assigns this desktop to malware by using SetThreadDesktop. To make all the actions impossible to witness under the “main” user profile, malware adds a new instance of explorer.exe specifically for the hidden desktop.
After that, LOBSHOT malware starts streaming the screen of the hidden desktop to the command server. They can perform whatever they want – now they are reigning over this computer too. Aside from manual actions, the client hackers use for connecting to the infected computer offers several hotkeys that may ease certain actions.
Protection against LOBSHOT stealer malware
Protective measures against LOBSHOT are the same as against any other stealer malware. Based on the fact it does not feature evasion of security software other than Microsoft, an obvious step is to have an alternative anti-malware solution.
Anti-malware solution is helpful advice for both reactive and proactive counteraction. Considering that the developers of this malware rely heavily on malicious pages in Google Ads, the network monitor will be nice to have. Meanwhile, it may be useful to prevent LOBSHOT from running, if it manages to get to your system unnoticed. Sure, such tasks require much more than just an “anti-malware program”. That’s why GridinSoft Anti-Malware may be a pretty good option. Its multi-component detection systems allow it to spot not only known malware, but also novice samples – a very demanded option for the modern threat landscape.





