Cisco Talos analysts write that the Russian-speaking hack group Gamaredon (aka Primitive Bear, Shuckworm, IronTiden and Callisto) is attacking Ukrainian organizations with the help of a new infostealer. The targets of this campaign are employees of the Ukrainian state, defense and law enforcement agencies.
Let me remind you that we also wrote that Hacker groups split up: some of them support Russia, others Ukraine, and that TrickBot Hack Group Systematically Attacks Ukraine.
Experts remind that the Gamaredon group is known for using only proprietary tools in its campaigns, including malicious scripts, backdoors and infostealers.
As part of the new campaign, which began in August 2022 and is still active, hackers began to use a new information theft tool that is able to extract certain types of files from victims’ computers, as well as deploy additional payloads.
The new malware has not yet received its own name, but it is known that it has clear instructions for stealing files with the following extensions: .doc, .docx, .xls, .rtf, .odt, .txt, .jpg, . jpeg, .pdf, .ps1, .rar, .zip, .7z and .mdb. The new Gamaredon stealer can steal files from connected devices (local and remote) by creating a POST request for each stolen file with metadata and its contents.
Experts say that this infostealer is spread via phishing emails containing Microsoft Office documents with malicious VBS macros. The VBS code is hidden in remote templates and is executed when the document is opened, after which it loads the RAR archive with LNK files.
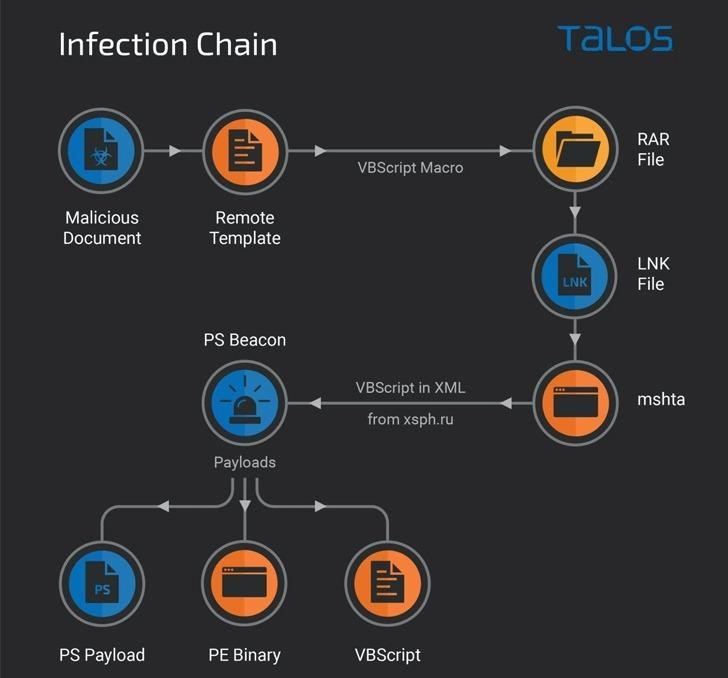
LNK files are designed to run mshta.exe to download and parse a remote XML file that executes a malicious PowerShell script that Gamaredon has previously used in its spy campaigns.
Another PowerShell script is loaded and executed to collect data about the infected system (computer name, VSN, base64 encoded screenshot) and then send this information to a remote server.




