Cryptocurrency
What is Cryptocurrency?
Cryptocurrency is a digital or virtual form of money that uses cryptography for security and operates on decentralized networks based on blockchain technology. Unlike traditional currencies issued by governments (fiat currencies), cryptocurrencies function without a central authority, allowing peer-to-peer transactions directly between users with no intermediaries like banks.
Key characteristics of cryptocurrency include:
- Decentralization: No central issuing authority controls the currency
- Digital-only: Exists solely as digital records in a blockchain
- Cryptographic security: Uses advanced encryption to secure transactions
- Pseudonymity: Provides some degree of privacy (varies by cryptocurrency)
- Immutability: Once recorded on the blockchain, transactions cannot be altered
The name "cryptocurrency" derives from the cryptographic techniques used to secure the network and verify transactions. The first and most well-known cryptocurrency, Bitcoin, was introduced in 2009 by an individual or group using the pseudonym Satoshi Nakamoto. Since then, thousands of alternative cryptocurrencies (altcoins) have emerged, each with different features, purposes, and underlying technologies.
How Blockchain Works
At the core of most cryptocurrencies is blockchain technology—a distributed ledger that records all transactions across a network of computers. This innovation solves the "double-spending problem" (preventing digital currency from being spent twice) without requiring a trusted central authority.
The Blockchain Process
- Transaction Initiation: A user initiates a transaction (sending cryptocurrency to another user)
- Transaction Verification: Network participants (nodes) verify the transaction's validity
- Block Creation: Verified transactions are grouped into a "block"
- Consensus Mechanism: Nodes agree on the validity of the block using methods like Proof of Work or Proof of Stake
- Block Addition: The validated block is added to the chain of previous blocks
- Transaction Completion: The transaction is now permanently recorded on the blockchain
Blockchain security fundamentals
Mining and Transaction Validation
The process of creating new cryptocurrency units is called "mining." In Proof of Work cryptocurrencies like Bitcoin, mining involves:
- Collecting pending transactions into blocks
- Solving complex mathematical puzzles to validate transactions
- Receiving cryptocurrency rewards for successful validation
This mining process serves two critical functions: creating new currency units and validating transactions without a central authority. Other validation methods, like Proof of Stake, have emerged to address the high energy consumption associated with traditional mining.
Types of Cryptocurrency
Cryptocurrencies have evolved into several distinct categories, each with different technical foundations and use cases:
1. Based on Consensus Mechanisms
Proof of Work (PoW) Cryptocurrencies
- Function: Miners compete to solve complex mathematical puzzles to validate transactions
- Examples: Bitcoin (BTC), Litecoin (LTC), Dogecoin (DOGE)
- Characteristics: High energy consumption, established security model, slower transaction times
Proof of Stake (PoS) Cryptocurrencies
- Function: Validators stake their cryptocurrency as collateral to validate transactions
- Examples: Ethereum (ETH, after "The Merge"), Cardano (ADA), Solana (SOL)
- Characteristics: Energy efficient, faster transactions, validators earn interest on staked amounts
2. Based on Purpose and Functionality
Payment/Currency Tokens
- Function: Designed primarily as digital currency for transactions
- Examples: Bitcoin (BTC), Litecoin (LTC), Bitcoin Cash (BCH)
- Characteristics: Focus on security, decentralization, and store of value
Platform/Utility Tokens
- Function: Power decentralized applications (dApps) and smart contracts
- Examples: Ethereum (ETH), Cardano (ADA), Polkadot (DOT)
- Characteristics: Support for smart contracts, dApps, programmable functionality
Stablecoins
- Function: Maintain stable value by pegging to fiat currencies or commodities
- Examples: Tether (USDT), USD Coin (USDC), Dai (DAI)
- Characteristics: Price stability, backed by reserves or algorithmic mechanisms
Privacy Coins
- Function: Provide enhanced anonymity and privacy features
- Examples: Monero (XMR), Zcash (ZEC), Dash (DASH)
- Characteristics: Enhanced transaction privacy, obscured transaction details
Each type serves different needs in the cryptocurrency ecosystem, from everyday transactions to complex decentralized finance applications.
Popular Cryptocurrencies
While thousands of cryptocurrencies exist, several have emerged as market leaders based on market capitalization, adoption, and technological innovation:
Bitcoin (BTC)
The original cryptocurrency, created by Satoshi Nakamoto in 2009, Bitcoin pioneered blockchain technology and remains the largest cryptocurrency by market capitalization. It was designed as a peer-to-peer electronic cash system that operates without a central authority.
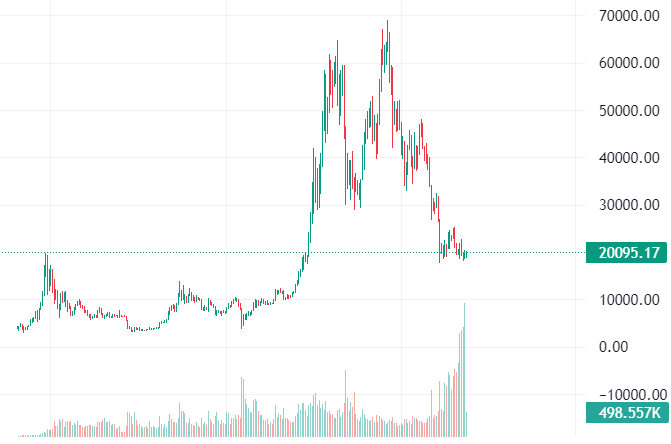
Bitcoin's primary value proposition is as a store of value and potential hedge against inflation, earning it the nickname "digital gold." Its market capitalization peaked at nearly $1.3 trillion in 2021, with its price reaching almost $69,000 per coin.
Ethereum (ETH)
Launched in 2015 by Vitalik Buterin, Ethereum expanded blockchain's capabilities beyond simple transactions by introducing smart contracts—self-executing contracts with the terms directly written into code. This innovation enabled a wide range of decentralized applications (dApps) to be built on the Ethereum platform.
Ethereum's native cryptocurrency, Ether (ETH), is used both as a digital currency and as "gas" to power operations on the network. It's the second-largest cryptocurrency by market capitalization and has become the foundation for numerous projects in decentralized finance (DeFi), non-fungible tokens (NFTs), and other blockchain applications.
Litecoin (LTC)
Created in 2011 by Charlie Lee, Litecoin was one of the first altcoins and is often described as "silver to Bitcoin's gold." Litecoin implemented several technical improvements over Bitcoin, including faster block generation times and a different hashing algorithm.
While Litecoin shares many features with Bitcoin, its simplified mining and faster transactions have made it attractive for smaller payments. Unfortunately, these same characteristics have also made it a target for malware authors who develop crypto-mining malware to exploit users' computing resources.
Other Notable Cryptocurrencies
- Ripple (XRP): Designed for cross-border payment solutions, especially for financial institutions
- Cardano (ADA): Focuses on sustainability, scalability, and transparency with a research-driven approach
- Solana (SOL): Known for high transaction speeds and low costs
- Tether (USDT): A stablecoin pegged to the US dollar
- Binance Coin (BNB): Native token of the Binance exchange, used for trading fee discounts and more
How to Acquire Cryptocurrency
There are several ways to acquire cryptocurrency, each with different considerations for security, convenience, and cost:
1. Cryptocurrency Exchanges
The most common method of acquiring cryptocurrency is through exchanges, which come in two main varieties:
- Centralized Exchanges (CEX): Platforms like Coinbase, Binance, and Kraken that function as intermediaries, managing user funds and facilitating trades.
- Decentralized Exchanges (DEX): Platforms like Uniswap and SushiSwap that operate directly on blockchain networks, allowing peer-to-peer trading without a central authority.
When selecting an exchange, consider factors like:
- Security features and history
- Available cryptocurrencies
- Fees and transaction costs
- User interface and ease of use
- Regulatory compliance in your jurisdiction
- Withdrawal options and limits
2. Peer-to-Peer (P2P) Platforms
P2P platforms like LocalBitcoins and Paxful connect buyers and sellers directly, often allowing various payment methods including bank transfers, cash, or digital payments. While these platforms can offer more flexibility, they generally require extra caution regarding security and potential scams.
3. Cryptocurrency ATMs
Cryptocurrency ATMs allow users to buy (and sometimes sell) cryptocurrencies using cash or debit cards. These machines often charge higher fees than online exchanges but offer convenience and privacy. However, they increasingly require identity verification for regulatory compliance.
4. Mining
Advanced users can mine certain cryptocurrencies by contributing computing power to validate transactions and secure the network. This process requires specialized hardware for most profitable cryptocurrencies and significant technical knowledge.
Warning: Mining Risks
While legitimate mining operations can be profitable, they require significant investment in hardware and electricity. Be extremely cautious of "cloud mining" services or mining software from untrusted sources, as these are frequently associated with cryptocurrency scams and malicious crypto-mining malware.
Secure Storage Solutions
Once you've acquired cryptocurrency, proper storage is critical for security. Unlike traditional currency held in banks, cryptocurrency security depends entirely on protecting the private keys that control access to your funds. If these keys are compromised, your cryptocurrency can be stolen with little recourse.
Types of Cryptocurrency Wallets
Hot Wallets (Online)
- Description: Connected to the internet, offering convenience but less security
- Types:
- Exchange wallets (provided by cryptocurrency exchanges)
- Web wallets (browser-based solutions)
- Mobile wallets (smartphone applications)
- Desktop wallets (software on personal computers)
- Best for: Small amounts for active trading or daily transactions
- Security considerations: Vulnerable to online attacks, malware, and exchange hacks
Cold Wallets (Offline)
- Description: Stored offline, significantly reducing the risk of unauthorized access
- Types:
- Hardware wallets (specialized physical devices like Ledger and Trezor)
- Paper wallets (private keys printed on physical paper)
- Steel wallets (private keys engraved in metal for durability)
- Best for: Long-term holdings and larger amounts
- Security considerations: Physical security, backup procedures, and recovery options
For optimal security, many experts recommend a combination approach: cold storage for long-term holdings and hot wallets for smaller amounts needed for regular transactions.
Source: Comparative analysis of wallet security features based on cryptocurrency security best practices
Critical Wallet Security Practices
- Backup your private keys or seed phrases in multiple secure locations
- Enable multi-factor authentication (MFA) wherever available
- Use unique, strong passwords for all cryptocurrency-related accounts
- Never share private keys or seed phrases with anyone
- Be wary of phishing attempts targeting your cryptocurrency holdings
- Keep wallet software updated to patch security vulnerabilities
- Consider using a dedicated device for cryptocurrency transactions
Security Risks in Cryptocurrency
While blockchain technology provides certain security advantages, the cryptocurrency ecosystem presents numerous risks that users must understand and mitigate:
Exchange Vulnerabilities
Centralized exchanges represent single points of failure in the otherwise decentralized cryptocurrency ecosystem. Major exchange hacks have resulted in billions of dollars in losses, including:
- Mt. Gox (2014): 850,000 Bitcoin stolen (worth approximately $450 million at the time)
- Coincheck (2018): $534 million in NEM tokens stolen
- BitGrail (2018): $195 million in Nano cryptocurrency stolen
- KuCoin (2020): $281 million in various cryptocurrencies stolen
Even with security improvements, exchanges remain prime targets for sophisticated attackers.
Smart Contract Vulnerabilities
Smart contracts on platforms like Ethereum can contain coding errors or security flaws that might be exploited. Notable incidents include:
- The DAO Hack (2016): $60 million stolen due to a code vulnerability
- Poly Network (2021): $611 million temporarily stolen (later returned by the hacker)
Private Key Management Risks
The security of cryptocurrency depends entirely on protecting private keys. Common risks include:
- Loss of private keys or seed phrases
- Theft through malware or physical access
- Social engineering attacks targeting key information
According to security research, cryptocurrency theft via private key compromise is becoming increasingly sophisticated, with specialized malware designed specifically to steal wallet credentials.
Regulatory and Market Risks
Beyond technical security, cryptocurrency users face additional risks:
- Extreme price volatility
- Changing regulatory environments that may restrict cryptocurrency use
- Lack of consumer protections compared to traditional banking
- Potential for sudden project abandonment ("rug pulls")
Common Cryptocurrency Scams
The cryptocurrency sector has unfortunately attracted numerous scams targeting both newcomers and experienced users. Understanding these common schemes is essential for protecting your assets:
Fake ICOs and Token Sales
Fraudulent Initial Coin Offerings (ICOs) or token sales promise revolutionary technology and massive returns but deliver nothing. These scams often feature:
- Plagiarized white papers
- Fake development teams with stolen identities
- Unrealistic promises of guaranteed returns
- Pressure to invest quickly before a "limited opportunity" ends
Ponzi and Pyramid Schemes
These schemes pay early investors with money from new investors, creating the illusion of legitimate returns until the system inevitably collapses. Notable cryptocurrency Ponzi schemes include:
- BitConnect: Collapsed in 2018 after reaching a $2.6 billion market cap
- OneCoin: A $4 billion scheme that operated from 2014-2019
- PlusToken: A $6 billion scam targeting primarily Asian investors
Fake Exchanges and Phishing
Fraudsters create fake cryptocurrency exchange websites or apps that mimic legitimate platforms. After users deposit funds, operators disappear with the money. Similarly, phishing attacks impersonate trusted cryptocurrency services to steal login credentials and private keys.
According to recent security reports, phishing remains one of the most successful attack vectors in cryptocurrency theft, with increasingly sophisticated techniques targeting even experienced users.
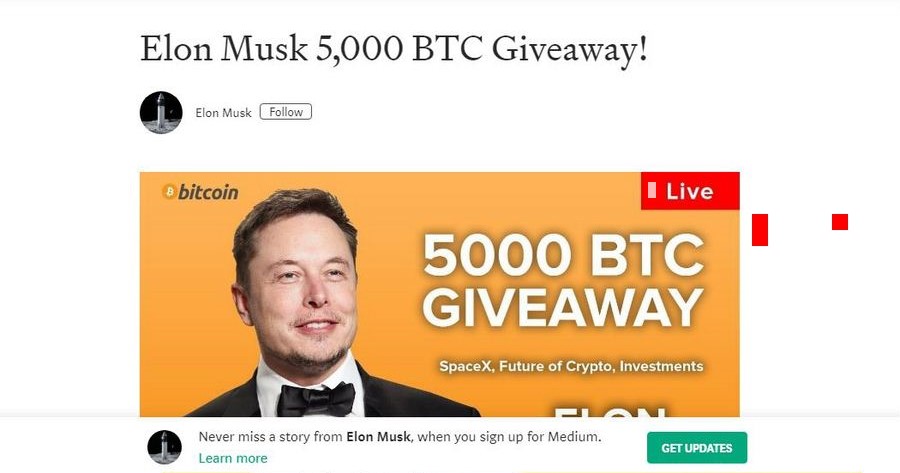
Giveaway Scams
These scams typically impersonate celebrities, influencers, or cryptocurrency founders, promising to "double" any cryptocurrency sent to a specific address. Once victims send funds, they receive nothing in return.
Romance and Investment Scams
Scammers establish romantic or friendly relationships with victims before introducing investment "opportunities" in cryptocurrency. These increasingly sophisticated schemes often unfold over months, building trust before the eventual theft.
The FBI's Internet Crime Complaint Center reported that in the first seven months of 2021 alone, they received over 1,800 reports of crypto-focused romance scams, with losses exceeding $133 million.
Recovery Scams
In a particularly cruel twist, recovery scammers target those who have already lost money to cryptocurrency scams. They pose as blockchain experts or specialized recovery services who can retrieve stolen funds—for an advance fee. After receiving payment, they disappear without providing any recovery services.
Crypto-Related Malware
Cybercriminals have developed specialized malware targeting cryptocurrency users and their assets:
Crypto-Miners
Cryptojacking malware (crypto-miners) secretly uses a victim's computing resources to mine cryptocurrency for the attacker. Signs of infection include:
- Unexplained high CPU or GPU usage
- System overheating or fans running constantly
- Significantly reduced performance
- Increased electricity bills
Popular cryptocurrencies for illicit mining include Monero (XMR) and Litecoin (LTC), as they can be effectively mined using consumer-grade hardware.
Clipboard Hijackers
These malicious programs monitor your clipboard for cryptocurrency wallet addresses and replace them with the attacker's address when you paste. When you attempt to send cryptocurrency, it goes to the attacker instead of your intended recipient.
Wallet Stealers and Infostealers
Sophisticated malware like crypto stealers specifically targets cryptocurrency wallets by:
- Scanning for wallet files on infected systems
- Capturing private keys and passwords
- Monitoring for cryptocurrency-related activities
- Exfiltrating sensitive data to attackers
According to security researchers, some advanced information stealers can even capture screenshots when cryptocurrency-related activities are detected, allowing attackers to observe security procedures and bypass them.
Protection Measures
Protecting your cryptocurrency investments requires a multi-layered security approach:
Technical Safeguards
Essential Security Measures
- Use hardware wallets for significant holdings
- Enable multi-factor authentication on all cryptocurrency accounts
- Keep operating systems and software updated
- Use a dedicated device for cryptocurrency transactions when possible
- Install reputable security software to protect against crypto-targeting malware
- Verify all wallet addresses before transferring funds
- Conduct small test transactions before large transfers
Behavioral Security
Safe Crypto Practices
- Research thoroughly before investing in any cryptocurrency
- Never share your private keys or seed phrases with anyone
- Be skeptical of promises of guaranteed returns or investment opportunities
- Verify the legitimacy of cryptocurrency exchanges and services
- Ignore unsolicited investment advice, especially via social media or messaging apps
- Use official websites accessed directly (not via links) for cryptocurrency services
- Create separate email addresses for cryptocurrency accounts
Malware Protection
To protect against specialized cryptocurrency-targeting malware:
- Install comprehensive anti-malware protection that can detect crypto-miners and wallet stealers
- Regularly scan your system for potential threats
- Be extremely cautious about downloading cryptocurrency software, wallets, or trading bots
- Verify the authenticity of all cryptocurrency-related applications
- Monitor system performance for signs of cryptojacking
GridinSoft Anti-Malware provides specialized protection against cryptocurrency-targeting threats, including crypto-miners, clipboard hijackers, and wallet stealers.
Investment Considerations
If you're considering cryptocurrency as an investment, keep these key principles in mind:
Risk Assessment
Cryptocurrency investments carry significant risks:
- Extreme volatility: Price swings of 10-20% in a single day are common
- Regulatory uncertainty: Changing government regulations can impact markets
- Technical complexity: Security and usage require technical understanding
- Market manipulation: Less regulated markets are vulnerable to price manipulation
Due Diligence
Before investing in any cryptocurrency:
- Research the project's technology, team, and use case
- Examine the tokenomics (supply, distribution, inflation rate)
- Review the project's development activity and roadmap
- Analyze community engagement and adoption metrics
- Consider the competitive landscape and potential market
Best Practices
Cryptocurrency Investment Principles
- Only invest what you can afford to lose - Cryptocurrency should typically represent only a small portion of a diversified portfolio
- Use dollar-cost averaging - Invest fixed amounts at regular intervals rather than all at once
- Maintain a long-term perspective - Short-term trading is especially risky in volatile markets
- Stay informed - The cryptocurrency landscape evolves rapidly; keep up with developments
- Be prepared for volatility - Significant price swings are normal in cryptocurrency markets
- Secure your investments - The security of your holdings is ultimately your responsibility
Remember that cryptocurrency investment success requires both financial literacy and technical security knowledge. As the saying goes in cryptocurrency communities: "Not your keys, not your coins" – highlighting the critical importance of security in this emerging asset class.
Conclusion
Cryptocurrency represents a significant innovation in financial technology, offering both opportunities and challenges. While the potential for financial inclusion, investment returns, and technological advancement is substantial, so too are the security risks and technical complexities.
By understanding how cryptocurrencies work, recognizing common threats, and implementing robust security practices, users can participate in this ecosystem more safely. Whether you're considering cryptocurrency as an investment, a technology to explore, or simply want to understand this digital phenomenon, a security-first approach is essential.
For additional protection against cryptocurrency-targeting threats, consider using GridinSoft Anti-Malware, which provides specialized detection for crypto-miners, wallet stealers, and other malicious software that could compromise your digital assets.
Frequently Asked Questions
Yes, in several different ways. You can perform a regular wireout transaction from the wallet, if you have connected it to a cryptotrading platform. It will automatically sell your crypto at market price and complete the transaction to your bank account. Alternatively, you can transfer your cryptocurrency to the exchange (it is usually over-the-counter) and get a payback on your card or directly in cash, if such is possible.
In some countries, you can withdraw money from cryptocurrency wallet directly, using special ATMs. Such a service is available only in the countries which applied cryptos as a legal tender – such as El Salvador.