
What Is Clickjacking?
Clickjacking or UI redress attack is based on a visual trick to make the user click on an element of the web page that is invisible or disguised as another element. The main goal of a clickjacking attack is to get unsuspecting website visitors to act on another website (the target website). For example, a user might be attracted to a website promising a prize. However, when the user clicks to accept the award, their click is used to purchase an item on the e-commerce website. This is achieved by hiding the user interface of the target website and placing the visual user interface on top of it so that the user does not know he or she is clicking on the target website.
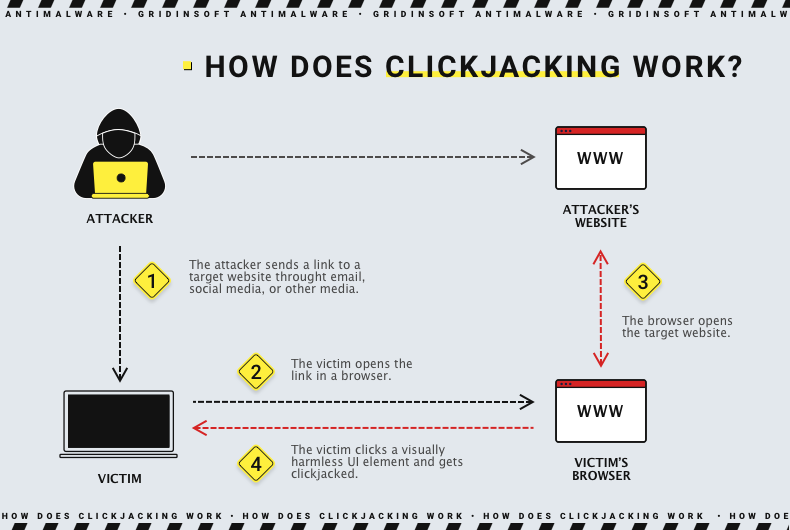
Because of this placement of the user interface, this type of attack is also known as UI redress or UI fix attack. Therefore, the user can unwittingly perform transactions such as transferring money, buying products, downloading malware, liking social networks, etc. But how does it work? Let's go further.
Types of Clickjacking Attacks
Depending on the nature of a particular situation, an attack may be called by different names. Here are some of them:
- Likejacking. An attack that intercepts user clicks and redirects them to "likes" on a Facebook page or other social networks. It is not very dangerous but will likely lead the feed to show you more liked content, even when you are not interested in this topic;
- Cookiejacking. A user interacts with a UI element by drag&drop, and provides the attacker with cookies stored in their browser. Cookies can be used to break into social networks, email, and other services. By installing your cookies with hashed passwords in their web browser, a criminal can gain access to your account without logging in;
- File hacking. In a file-hijacking attack, the attacker takes advantage of the ability of web browsers to navigate your computer's file system. For example, when you upload photos to social networks or a backup to cloud storage. When a file browser window appears, you can navigate the file system. In a file hijacking attack, clicking the "Browse Files" button can set up an active file server, potentially giving the attacker access to your entire file system;
- Cursorjacking. this method changes the cursor's position to another location where the user perceives it. Thus, the user believes he is doing something when he is doing something else;
- Password manager attacks. Even though browsers refuse to automatically fill out forms if the protocol on the current login page does not match the protocol at the time of password saving, some password managers can still insecurely enter passwords for HTTP versions of HTTPS-saved passwords. Most managers did not protect against iFrame-based and redirect-based attacks. They exposed other passwords that used synchronization of passwords between multiple devices.
This is part of the many other variants of clickjacking. However, despite the multitude of variants, the basic principle they rely on is the same: capturing user actions by tricking the user interface.
Clickjacking Examples
The attacker creates a clone of a website that looks like the real one but embeds the malicious website in an iframe tag. Since the iframe is invisible, the malicious site is not visible either, and the victim only sees the site that looks like the real one. Using social engineering, the attacker makes the target visit a malicious website and follow a malicious link. For example, it could be a link to a fake contest they won or an enticing photo or interesting picture.
The invisible elements on the embedded malicious site are the same as the interactive elements on the visible page, which looks legitimate. However, the hidden elements trigger unwanted actions, such as downloading a malicious script when clicked. Once the target visits the site and clicks on the link, the target's browser launches a malicious script, and bad things happen.
Protection Against Clickjacking
Clickjacking attacks are pretty rare nowadays, but it is better to have the risk minimized. Most of the job for your protection against clickjacking is already done by the security technologies development, in particular the security updates to web browsers. But some situations may still force us to make it.
Use browsers that support the Intersection Observer API.
The Intersection Observer API can track the "visibility" of target elements on a web page, allowing the browser to detect when a framed window is hidden. The following desktop browsers currently support the API:
- Google Chrome 58 and above;
- Mozilla Firefox 55 and above;
- Microsoft Edge 16 and later;
- Opera 45 and above
There are enough browsers available on mobile devices that it is almost impossible to list them all. If necessary, they can always be downloaded from the Apple App Store and the Google Play Store. However, the good news is that the default browsers on iOS and Android support the Intersection Observer API.
Use a browser add-on
Several browser add-ons can provide some protection against clickjacking attacks. The most popular options are:
- NoScript: The NoScript browser add-on prevents users from clicking on invisible or "fixed" web page elements. NoScript is free but only supported by the Mozilla Firefox browser.
- NoClickjack: The NoClickjack browser add-on is supported by Google Chrome, Mozilla Firefox, Microsoft Edge, and Opera. The add-on makes all frames on a web page visible.
Frequently Asked Questions
In fact, these two fraudulent tactics aim for the same thing, but via different approaches. From some point of view, clickjacking may be called a specific way of phishing. Still, phishing is more a social engineering tactic, which forces the victim to do what the fraudster wants. The victim does everything benevolently - missing the details that can uncover the fraud.
Clickjacking also makes the victim believe it is doing what it really wants to, but instead of social engineering, it spoofs the website interface in a specific way. While clicking on a button on a legit site, the victim in fact clicks a button on an invisible frame that calls the function needed by the fraudster. After that click, the latter receives the victim’s identity information, hijacks the money transfer, grabs the cookies and so on.
