Ransomware groups come and go, but the people behind them continue to use their hacking and extortion skills in new operations. For example, former members of the now-defunct Russian-language ransomware group Conti continue to conduct their dirty business under many other “sub-brands”.
Conti Ransomware in a nutshell
Conti ransomware, led by Russia-based threat actors, appeared in February 2020 and soon became one of the most active groups in the ransomware space. They use a Ransomware-as-a-Service attack model and pay affiliates for successful deployment. Conti’s structure was exposed in August 2021 when a former companion leaked training documents. Additionally, there are indications that the same group operates the Ryuk ransomware, but definitive proof is yet to be observed. Conti ransomware is known for its advanced capabilities. However, a key feature is that the people behind it are difficult to deal with. They often break promises to victims, even if they agree to pay. This means compliance may still result in leaked data or encrypted files.
The death of the Conti
The Russia-Ukraine war has contributed to the takedown of the Conti ransomware group since, in February 2022, Conti fully supported Russia’s invasion of Ukraine. As a result, such actions were met with negativity from anywhere, as members and the public. In addition, the insider leaked tens of thousands of internal chat logs to the public just four days after the official start of the Russia-Ukraine war, following Conti’s announcement of his support for Russia. Internal chat logs leaked to the public reveal Conti’s day-to-day operations and structure. Its structure resembled an ordinary organization’s, including salary structures and HR recruitment procedures.
Moreover, some employees were unaware that they worked for cybercriminals. However, those who did suspect what was going on were offered bonuses to stay silent. In addition to the fact that the leak included Conti ransomware source code, hints were found that the end was nearest for the group even before the leak.
The verdict is signed
Such a high-profile announcement to the group about support for Russia and threatening to act on its behalf made it nearly impossible for victim companies to negotiate with them. As a result, almost no payments were made to the group in the months following. This is usually discussed with law enforcement before deciding to pay the ransom. This is required to make sure they are legitimate. Still, Conti’s alignment with Russia made financial support to the group illegal and extremely risky. This significantly reduced the group’s income and weakened its ability to function.
What’s Becoming of Group members?
Experts report that the ransomware group Conti has ceased its activities. Its infrastructure has been shut down, and the group’s leaders have stated that the brand no longer exists. Subsequently, the extortion market was divided between Lockbit, which dominated, and smaller groups. Although the Conti brand no longer exists, experts believe that this crime syndicate will long play an essential role in the extortion industry.
Thus, experts believe that instead of the traditional rebranding (and subsequent transformation into a new group) of hacker groups, Conti broke up into smaller groups of extortionists to conduct attacks. As part of this “transformation,” small hack groups get an influx of experienced pentesters, negotiators, and operators from among Conti members. And the Conti syndicate, by splitting into smaller “cells” controlled by a single leader, gains mobility and the ability to evade the attention of law enforcement.
Post-Conti Groups
Conti’s latest attack was less potent than noisy. “The only goal Conti wanted to achieve with the last attack was to use the platform as a promotional tool, arrange its own ‘death,’ and then revive itself in the most plausible way possible,” experts say. In addition, according to the researchers, Conti has several subsidiaries, such as Royal, Black Basta, Silent Ransom Group, HelloKitty, AvosLocker, Zeon, Hive, BlackCat, and BlackByte.
Royal Ransomware
The Royal ransomware group has targeted over 1,000 organizations with a social engineering attack, tricking victims into trusting the attackers. The scheme involves pressuring victims to open a file that is actually a malware loader. If successful, victims can fall victim to ransomware. The group may have even created a fake version of the Midnight Group to further deceive victims. This variation of a gambit known as BazarCall involves scaring victims into thinking their systems have been locked by ransomware and manipulating them into installing the actual ransomware. Royal is a ransomware group splintered from Conti after backing the Kremlin’s war on Ukraine. The group targets healthcare companies and top-tier corporations for ransom demands ranging from $250,000 to over $2 million. They use BazarCall strategies and have recently targeted Linux systems. Their encryption scheme is implemented correctly, making recent backups or a decryptor the only way to recover lost files.
Black Basta
Black Basta is a group formerly called Conti Team Three. They typically use QBot to gain initial access and then deploy the main payload known as Black Basta ransomware. Additionally, the BlackByte and Karakurt groups are engaged in data exfiltration. The group is relatively new in 2022 and has made a name for itself. In a few months since its ransomware was first discovered, Black Basta has updated its toolkit and increased the number of victims worldwide. It operates on the ransomware-as-a-service principle. The number of Black Basta ransomware detections is currently low, probably because of how recently it was discovered.
Like most modern ransomware, Black Basta has a more targeted approach to selecting its victims rather than relying on spray-and-pray tactics. However, the speed with which the malware authors have increased their arsenal of attacks and developed a new Linux build merits further investigation by the ransomware gang behind it.
Zeon Ransomware
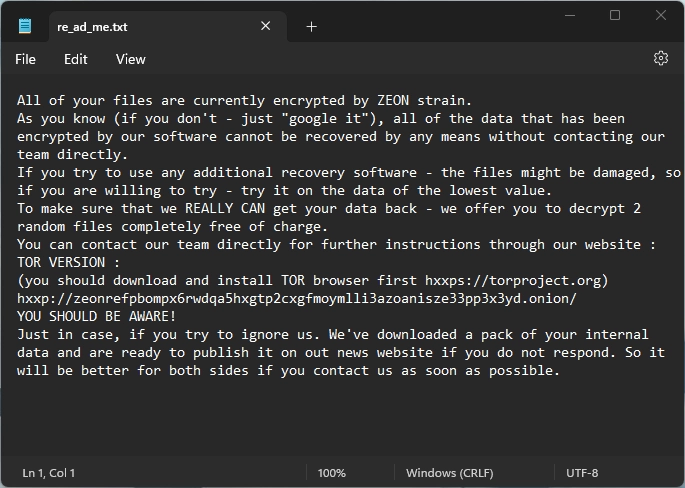
The Zeon ransomware was first detected in late January 2022 and is characterized as unsophisticated at the mass production level. Zeon ransomware prompts victims to visit a TOR-based payment portal. Zeon is a precursor to the Royal ransomware. ZeonThanos targets small and medium-sized businesses (SMBs). It spreads via phishing emails, services such as Remote Desktop Protocol (RDP), and third-party platforms (e.g., Empire, Metasploit, Cobalt Strike).
Silent Ransom Group
Luna Moth, aka the Silent Ransom Group, began with a campaign to hack organizations with fake subscription renewals. The group used phishing campaigns that provided remote access tools to steal corporate data. Having stolen sensitive data, the group has threatened to share the files publicly unless a ransom is paid. Luna Moth engages in callback phishing, a social engineering attack that requires the attacker to interact with the target to achieve their goals. This attack style is more resource-intensive but less complex than script-based attacks and is said to have a much higher success rate.
AvosLocker
AvosLocker is another variant working on the RaaS model. First spotted in July 2021, and several variants have been released. One notable feature of AvosLocker campaigns is the use of AnyDesk. This is a remote administration tool (RAT) for connecting to victim computers. In this way, the operator can manually control and infect the machine. It can also run safely as part of an evasive hacking tactic. Attackers sell the stolen data on their website in addition to their double extortion scheme. This could be a way to further monetize one successful attack or save a failed attack.
Experts also believe Conti members have created new and autonomous groups that focus entirely on stealing data rather than encrypting it. These groups include Karakurt, BlackByte, and Bazarcall.
How to protect against ransomware?
Based on the above, we understand ransomware can cause problems for individual users and businesses. Therefore, protecting against ransomware requires a holistic and comprehensive approach and preventive measures. The following recommendations will help prevent ransomware infections and be generally helpful when surfing the Internet.
For users
To prevent a ransomware infection, it is sufficient to follow cyber hygiene, which is as follows:
- Only click on links and only open attachments in an email if you are sure of the reliability of the sender.
- Don’t use hacked software. Often there is an unpleasant surprise in the form of a virus and a disabled license check in the installer.
- Update the operating system on time and the software you use. This is how developers fix detected vulnerabilities.
- Use reliable antivirus software. If malware does get on your computer, the protection tool will neutralize it before it is deployed and begins its dirty actions.
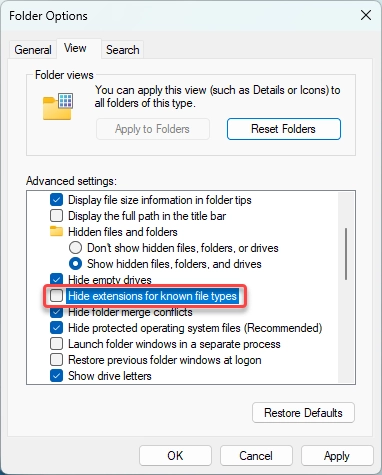
Hint: You can enable display file extensions in Explorer settings. This will help you recognize fake files that are executable but masquerade as document files.
For businesses
The following tips can help prevent a ransomware attack on your organization:
- Make backups. Use a data backup and recovery for all critical information. Note that backups connected to the network can also be affected by ransomware. Therefore, your backup files should be appropriately protected and stored offline so attackers can’t use them. Ideally, implement the 3-2-1 rule, keeping three copies of your information. The data is stored on two different types of storage, and one of those media is off-site. It’s also essential to test the backups periodically to ensure they work and maintain data integrity.
- Application safelisting. A safelist identifies which applications can be downloaded and run on the network. Any unauthorized program or website not on the safelist will be restricted or blocked. Limit users’ ability (permissions) to install and run software applications unnecessarily. Apply the “least privilege” to all systems and services. Restricting these privileges can prevent malicious software from running or limit its spread across the network.
- Endpoint security. As enterprises begin to expand, the number of end users increases. This creates more endpoints, such as laptops, smartphones, and servers, that must be protected. Unfortunately, each remote endpoint creates the opportunity for criminals to gain access to the main network. When you work from home or for a larger company, consider endpoint detection and response (EDR) for all network users.
- Train the team. Because end users and employees are the most common cyberattack gateways, security training is key to preventing ransomware spread. Everyone protects the organization when employees know how to detect and avoid malicious emails. In addition, security training can teach team members what to pay attention to in an email before they click a link or download and open an attachment.





