There’s a demand for users to secure their privacy and security when using Snapchat. This is due to the fact that it’s one of the most popular social media platforms. Here are the ways hackers usually hack your Snapchat accounts.
How Attackers Hack Someone’s Snapchat Account
Snapchat does not seem to be the place where something important and unremarkable for hacking is stored. But still Snapchat accounts are under threat of various hacks. The main motives of intruders are espionage, obtaining personal information (passwords, phone numbers, etc.), blackmail, etc. Here is a list of the main methods of hacking that cybercriminals use for their attack.
1. Downloading Spyware and Keylogger Apps
People use spyware tools called spyware to monitor someone else’s Snapchat account. This is the most popular way that people monitor someone else’s social media account.
The apps covertly install spyware on the smartphone of the intended victim, continuously recording their every move and accessing them remotely at any time. This information is accessible to the invader, who uses it to view and archive Snapchat messages from the victim. These apps store messages, photos, and videos, as well as screenshots. Some also include location tracking.
There are numerous ways to enter someone else’s account. Keyloggers are a common tool that record every keystroke a person makes. This allows anyone to track what text a person enters on their keyboard. A keylogger is a software program installed on someone’s device that records their password. If a person doesn’t use a password manager, manually entering their password can cause trouble. Because of this, hackers can set up keyloggers on the victim’s devices and quickly obtain their account ID and password.
2. Third-Party Data Leaks
Monitoring apps can record Snapchat data and store it, even after the content is deleted by the user. When these apps uncover data leaks, including the username and password they contain, all of that information becomes publicly available on the internet. Anyone can access your account information through third-party data leaks. It’s wise to check for possible data leaks from other sources.
3. Phishing
Also known as phishing pages, fake websites created by hackers use deceptive methods to trick people. For example, one could be a seemingly identical copy of the official Snapchat website. After logging in with their username and password, people are hacked. They mistakenly provide the password to the hackers when they enter the credentials on the official website. If someone has been phished, they should know what to do after a hacking attack.
When evaluating a website’s URL, always consider the information it contains for phishing purposes. Any words or ending in a .com domain that appears suspicious should be noted and avoided.
4. Brute Force Attacks
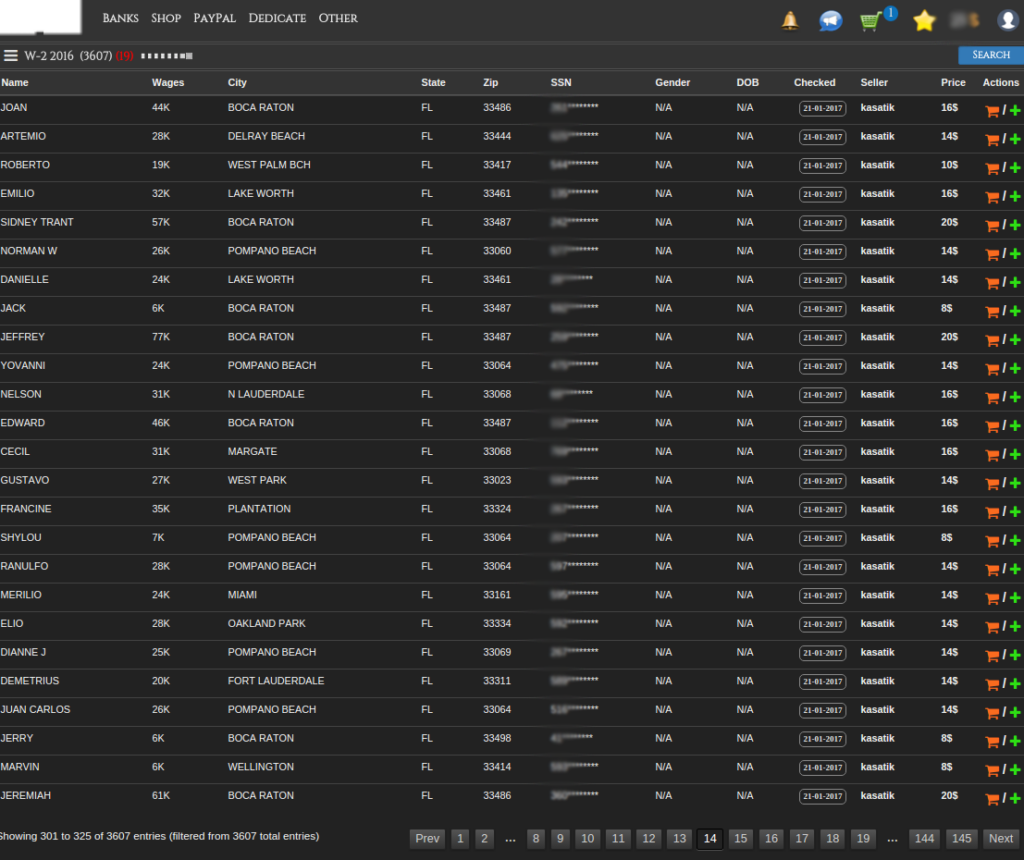
Brute force attack is one of the common methods of intruders, thanks to which they manage to bombard login pages with thousands of different passwords and the duration of this method occurs until one of the accounts is hacked, after which the user will not be able to login to his account.
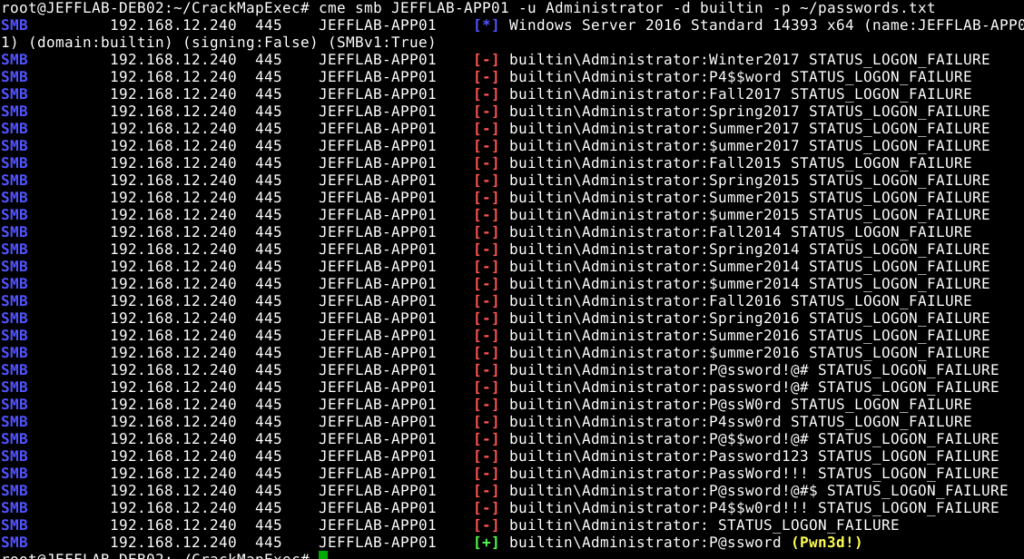
For testing take easy and common passwords such as 12345 or qwerty 123. Because users use such easy passwords, hackers can decrypt them in just a few seconds. It’s a method of entry that looks like a burglar who cracks safes and uses every number in the lock.
5. Using Wireless Sniffing
Most of us prefer to use public WiFi, but sometimes we need to be more careful. Hackers can gain access to a wireless network such as B. public Wi-Fi and start intercepting every bit of data sent over the network to get your Snapchat password. Of course, this isn’t just limited to passwords. Hackers can also target your private information, such as credit card numbers, addresses, dates of birth, social security numbers, and more.
How to Protect Your Snapchat Account
You will hardly find a man who will do nothing to dig into other people’s accounts and even more to hack them. This means that behind all of the above hacking methods are hackers who have a specific purpose and will do everything to achieve it. But, there is another side to all this, users can on their own prevent attackers and protect their data. Here is a list of the most suitable methods that you will need if you use social media, including Snapchat.
- Keep your smartphone password private. Likewise, if you’re an iPhone user, do this for accounts associated with numerous devices, such as your Apple ID and password.
- Confirm your Snapchat account phone number and email address to keep it safe.
- Choose a secure password for your Snapchat. It should be a combination of characters that does not contain any personal information; it must be different from your other accounts, and you should keep it private.
- Check your account privacy settings. This lets you control who can see your stories, send you Snaps, and see where you are. This prevents others from finding your username.
- You should only add real friends to your contact list. Don’t associate with strangers. Yes, it may seem fun and frivolous, but it’s not worth risking your security and privacy.
- Enable two-factor authentication to protect yourself from others trying to log into your account. This feature ensures that the person signing up is actually you, as you need to verify it twice.




🫀🫀🫀