AT&T researchers have discovered a new Linux stealth malware called Shikitega that targets computers and IoT devices and uses privilege escalation vulnerabilities to run the Monero cryptocurrency miner on the infected devices.
Shikitega can evade antivirus software with a polymorphic encoder that makes signature-based static detection impossible.
Let me remind you that we also said that New Linux Malware Lightning Framework Installs Backdoors and Rootkits, and also that Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable.
According to the AT&T report, the malware uses a multi-stage infection chain in which each level delivers only a few hundred bytes, activating a simple module, and then moves on to the next. That is, Shikitega incrementally delivers its payload, with each step revealing only a fraction of the total payload.
The infection starts with a 370-byte ELF file containing an encoded shellcode. The encoding is done using the Shikata Ga Nai payload encoding scheme.
Using the encoder, the malware goes through multiple decoding cycles where one cycle decodes the next layer until the final shellcode payload is decoded and executed.
After the decryption is completed, the shellcode is executed, which communicates with the C&C server and receives additional commands stored and executed directly from memory.
One command downloads and executes Mettle, a small, portable Metasploit Meterpreter payload that gives an attacker additional ability to remotely control and execute code on the host.
Mettle extracts an even smaller ELF file that uses CVE-2021-4034 (PwnKit) and CVE-2021-3493 to elevate privileges to root and load a cryptominer
Persistence for the cryptominer is achieved by deleting all downloaded files to reduce the chance of detection.
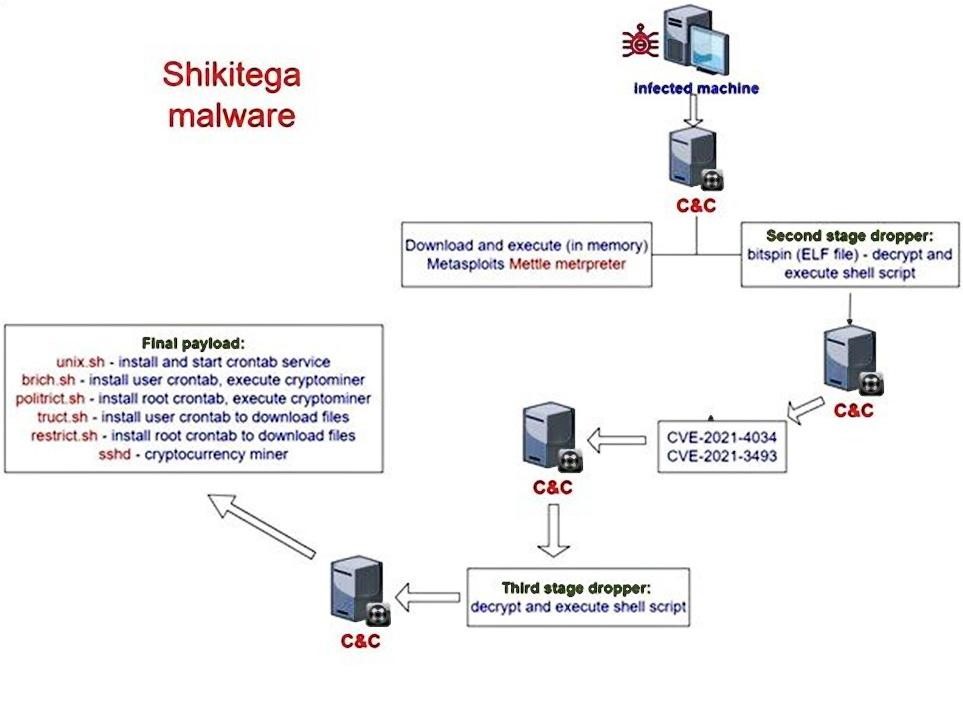
Also, to avoid detection, Shikitega operators use legitimate cloud hosting services to host their C&C infrastructure. This puts operators at risk of being detected by law enforcement, but provides better stealth in compromised systems.
The AT&T team has recommended that administrators apply available security updates, use EDR on all endpoints, and regularly back up critical data.




