Trustwave experts published a report, in which they said that the American company was exposed to a rare attack through BadUSB. An unnamed American hotel company was mailed a fake BestBuy gift card along with a malicious USB stick.
The accompanying letter said that the drive must be connected to a computer in order to access the list of products for which you can use a gift card.
 Such targeted attacks by BadUSB are extremely rare in practice.
Such targeted attacks by BadUSB are extremely rare in practice.
Let me remind you that BadUSB is a class of attacks that allows using tools like Rubber Ducky to take control of many devices that have a USB port. In this way, you can emulate any peripherals, but most often criminals fake a keyboard.
“The victim company found the letter suspicious and turned for help in investigating the incident”, – say experts at Trustwave.
As found the researchers, after connecting BadUSB to the test workstation, the flash drive launched the PowerShell command (through a series of automatic keystrokes). In turn, this command downloaded a more voluminous PowerShell script from a remote site, and then installed a Malware bot – a JScript-based bot – on the test machine.
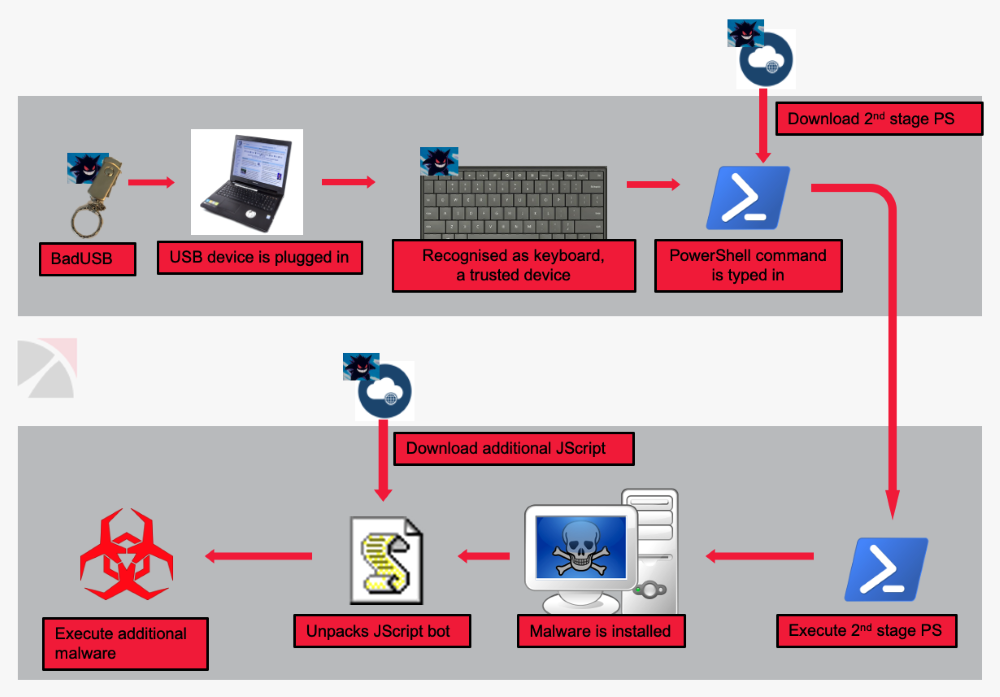
“At the time of the analysis, we were not able to find another similar strain of malvari. The malware is unknown to us. It is difficult to say whether it was created on an individual order, but probably it was, because it is not very widespread and seems to be targeted”, – say the experts.
Trustwave experts told ZDNet that after the initial analysis, a file similar to the malware was uploaded to VirusTotal for analysis.
According to a subsequent analysis by Facebook experts, the file is probably associated with the well-known hacker group FIN7 (aka Carbanak, Carbon Spider, Anunak). It is unclear who uploaded the file to VirusTotal. Perhaps other information security experts that are also investigating the BadUSB attack on another victim did it.
“Similar [BadUSB] attacks are often modeled during pentests and used during red team exercises. But in the real world, attacks of this type are much less common”, – say experts at Trustwave.
Let me remind you that the last time Kaspersky Lab researchers described a practical attack of the BadUSB type in December 2018. Then it became known about the attacks on banks, called DarkVishnya. As part of this campaign, the attackers used a special tool for conducting USB attacks Bash Bunny, comparable in size to a regular USB flash drive.
Please read about other serious dangers of USB devices.




